Veröffentlichungen und Aktualisierungen
Alle aktuellen Änderungen und Verbesserungen Vectra AI .
Vielen Dank! Ihr Beitrag ist eingegangen!
Huch! Beim Absenden des Formulars ist etwas schief gelaufen.
Klar
Datum:
Januar 2026
Freigabe:
2026.1
RUX: SaaS-Bereitstellung
Abdeckung
Verbesserungen für eine schnelle Freigabe
Die folgenden Verbesserungen wurden seit dem letzten Software-Release-Zyklus an den Algorithmen vorgenommen. Kunden, die mit dem Update-Service von Vectra verbunden sind und den Remote-Support aktiviert haben, haben diese Verbesserungen erhalten. Alle anderen Kunden erhalten die folgenden Verbesserungen als Teil dieser Version:
- Vectra AI die Umstellung der bisher über die Suricata-Engine bereitgestellten Erkennungen auf native Erkennungen Vectra AI , die direkt auf der Vectra-Flow-Engine ausgeführt werden. Diese fortlaufenden Bemühungen stellen sicher, dass allen Kunden erweiterte Funktionen zur Erkennung von Angreiferverhalten zur Verfügung stehen, ohne dass Suspect Protocol Activity (SPA) oder eine signaturbasierte Erkennungslogik erforderlich sind.
- Diese Version führt zusätzliche Erkennungen für Cobalt Strike, Brute Ratel und PowerShell Empire.
- Vectra AI die Genauigkeit der Smash-and-Grab-Erkennung verbessert, indem sichergestellt wird, dass die Ziel-Domänennamen korrekt aktualisiert werden, wenn sie später in einer Sitzung beobachtet werden. Durch diese Verbesserung funktioniert die Whitelist-Logik wie vorgesehen, wodurch unnötige Warnmeldungen reduziert und die Genauigkeit der Smash-and-Grab-Erkennung verbessert werden.
- Vectra AI die Erkennung auf Informationsebene für Remote Management and Monitoring (RMM)-Tools verbessert, indem Anwendungsprotokolldetails korrekt in die Erkennungsmetadaten eingefügt werden. Diese Verbesserung sorgt für einen klareren Kontext auf Host-Seiten, wenn RMM-Aktivitäten beobachtet werden, und verbessert so die Klarheit der Untersuchungen, während gleichzeitig eine störungsarme, nicht bewertende Alarmierung gewährleistet bleibt.
- Vectra AI seine Mythic C2-Erkennungs -Logik verfeinert, um Fehlalarme zu reduzieren, indem die Auswertung von Serverzertifikatsfeldern verschärft wurde. Dieses Update schränkt übermäßig breite Musterabgleiche ein, verhindert, dass harmlose Domains mit ähnlichen Begriffen Warnmeldungen auslösen, und verbessert die allgemeine Erkennungsgenauigkeit.
Neue Erkennung: Verdächtige Azure-Operation – Änderung der DNS-Sicherheitsrichtlinie
Vectra AI eine neue Erkennungsfunktion eingeführt, die verdächtige Verhaltensweisen im Zusammenhang mit Änderungen an der Protokollierung des Netzwerkdatenflusses aufdeckt. Die neue Erkennungsfunktion „Azure Suspect Operation – DNS Security Policy Modification” (Verdächtige Azure-Vorgänge – Änderung der DNS-Sicherheitsrichtlinie) wurde entwickelt, um Aktionen aufzudecken, bei denen eine Entität beim Löschen oder Ändern einer mit einer DNS-Sicherheitsrichtlinie verbundenen Ressource beobachtet wurde. Dies könnte die Protokollierung von DNS-Abfragen deaktivieren oder auf andere Weise die DNS-Auflösung innerhalb der Azure-Umgebung manipulieren. Bedrohungsakteure nutzen diese Technik, um die Protokollierung zu beeinträchtigen und der Erkennung zu entgehen.
Neue Erkennung: Verdächtige Azure-Operation – Flow-Protokolle deaktiviert
Vectra AI eine neue Erkennungsfunktion eingeführt, die verdächtige Verhaltensweisen im Zusammenhang mit Änderungen an der Netzwerkflussprotokollierung aufdeckt. Die neue Erkennungsfunktion „Azure Suspect Operation – Flow Logs Disabled” (Verdächtige Azure-Vorgänge – Flussprotokolle deaktiviert) wurde entwickelt, um Aktionen aufzudecken, bei denen eine Entität beim Löschen einer Azure-Flussprotokollressource beobachtet wurde. Dies deutet auf die Entfernung der Flussprotokollierung für ein VNet, ein Subnetz oder eine Netzwerkkarte hin und ist eine bekannte Technik zur Umgehung cloud , die von Angreifern genutzt wird, um die Sichtbarkeit und Überprüfbarkeit von Aktionen zu beeinträchtigen.
Neue Erkennung: Verdächtige Azure-Operation – Änderung der Netzwerksicherheitskonfiguration
Vectra AI eine neue Erkennungsfunktion eingeführt, die verdächtige Verhaltensweisen im Zusammenhang mit Änderungen an Netzwerksicherheitskonfigurationen aufdeckt. Die neue Erkennungsfunktion „Azure Suspect Operation – Network Security Config Change” (Verdächtige Vorgänge in Azure – Änderung der Netzwerksicherheitskonfiguration) wurde entwickelt, um Aktionen aufzudecken, bei denen eine Entität unerwartet eine Azure-Netzwerksicherheitsgruppe (NSG) erstellt oder ändert oder eine Azure-Firewall-Ressource modifiziert. Dies kann auf laterale Bewegungen innerhalb des Netzwerks oder einen Versuch hinweisen, die Abwehrmaßnahmen zu beeinträchtigen.
Neue Erkennung: Verdächtige Azure-Operation – riskante Löschung
Vectra AI eine neue Erkennungsfunktion eingeführt, die verdächtige Verhaltensweisen im Zusammenhang mit risikoreichen Löschvorgängen in einer Azure-Umgebung aufdeckt. Die neue Erkennungsfunktion „Azure Suspect Operation – Risky Deletion” (Verdächtige Vorgänge in Azure – riskante Löschvorgänge) wurde entwickelt, um Aktionen wie das Entfernen sensibler Backups und Unveränderbarkeitsrichtlinien aufzudecken, die Angreifer nutzen könnten, um Abwehrmaßnahmen zu umgehen und Schaden anzurichten. Diese Erkennungsfunktion stärkt den Schutz vor cloud wie Storm-0501, die diese Techniken in dokumentierten Angriffen eingesetzt haben.
Verbesserung der Erkennung: Azure TOR-Aktivität
Das Azure TOR-Aktivitätserkennungsmodell wurde verbessert, um die Priorisierung der mit diesem Verhalten verbundenen Entitäten zu optimieren. Künftig Vectra AI den Entitäten, die dieses Verhalten aufweisen, mehr Gewicht beimessen, damit sie umgehend auf der Seite „Respond“ (Reagieren) angezeigt werden. Kunden können aufgrund dieser Änderung einen leichten Anstieg der priorisierten Entitäten feststellen.
Neue Erkennung: Azure AD Verdächtige Operation: Gastbenutzer hinzugefügt
Vectra AI eine neue Erkennungsfunktion eingeführt, die verdächtige Verhaltensweisen im Zusammenhang mit dem ersten Zugriff aufdeckt. Die neue Erkennungsfunktion „Azure AD Suspect Operation: Guese User Added” (Verdächtige Azure AD-Operation: Gastbenutzer hinzugefügt) wurde entwickelt, um Verhaltensweisen aufzudecken, bei denen ein Prinzipal einen externen Gastbenutzer in die Umgebung einlädt, was nicht mit dem beobachteten Verhaltensprofil des Prinzipals übereinstimmt. Diese Methode wird von Angreifern in Social-Engineering-Kampagnen verwendet, um Zugriff auf die Umgebung des Opfers zu erlangen und dort zu bleiben.
Neue Erkennung: Azure AD Verdächtige Operation: Ungewöhnliche Anmeldung über einen Proxy
Vectra AI eine neue Erkennungsfunktion eingeführt, die verdächtige Verhaltensweisen im Zusammenhang mit dem ersten Zugriff aufdeckt. Die neue Erkennungsfunktion „Azure AD Suspect Operation: Unusual Sign-On from a Proxy” (Verdächtige Azure AD-Operation: Ungewöhnliche Anmeldung über einen Proxy) wurde entwickelt, um Aktionen aufzudecken, bei denen ein Prinzipal sich über einen Proxy oder ein VPN anmeldet, was nicht seinem normalen Verhalten entspricht. Dies ist eine Methode, mit der Angreifer ihren tatsächlichen Standort verschleiern. Diese Erkennungsmethode ist die erste, die die neue Threat Intelligence-Engine Vectra AI nutzt – eine Sammlung privater und lizenzierter Bedrohungs-Feeds, die umfangreiche Kontext- und Reputationsinformationen für eine möglichst hohe Signalklarheit liefern.
Verbesserte Sichtbarkeit der Kerberos-Verschlüsselung
Wir haben die Berichterstattung über Kerberos-Verschlüsselungsmetadaten verbessert, um einen genaueren Einblick in die Authentifizierungsaktivitäten zu ermöglichen.
Die Plattform unterscheidet nun klar zwischen:
- Die vom Client angeforderten Verschlüsselungsalgorithmen
- Die zum Schutz des Kerberos-Sitzungsschlüssels verwendete Verschlüsselung
- Die zur Verschlüsselung des Kerberos-Tickets verwendete Verschlüsselung
Diese Verbesserung stärkt die Untersuchung von Kerberos-basierten Angriffstechniken, darunter AS-REP Roasting und Kerberoasting, indem sichergestellt wird, dass für jede Authentifizierungsstufe der richtige Verschlüsselungskontext angezeigt wird.
Sicherheitsteams, die threat hunting Authentifizierungstelemetriedaten überprüfen, werden möglicherweise ab Ende Januar aktualisierte Kerberos-Verschlüsselungsfelder bemerken. Es sind keine Maßnahmen erforderlich, aber bestehende Abfragen oder Workflows sollten überprüft werden, um die aktualisierten Metadaten zu berücksichtigen.
Verbesserte Sichtbarkeit der Kerberos-Vorabauthentifizierung
Wir haben eine verbesserte Sichtbarkeit der Kerberos-Vorauthentifizierungsaustausche (PA-DATA) während AS-REQ- und AS-REP-Flows eingeführt.
Die Plattform zeigt nun sowohl die Arten als auch die Anzahl der Vorauthentifizierungsdaten an, die vom Client verwendet und vom KDC zurückgegeben werden. Dies liefert zusätzlichen Kontext zum Verständnis der Verhandlung der Kerberos-Authentifizierung und hilft Sicherheitsteams dabei, abnormales oder unerwartetes Vorauthentifizierungsverhalten zu identifizieren.
Diese Verbesserungen unterstützen eine effektivere Untersuchung von Kerberos-basierten Angriffen und Fehlkonfigurationen, insbesondere solchen, die modifizierte oder umgangene Vorab-Authentifizierungsmechanismen betreffen.
Threat Hunter und Analysten, die die Telemetriedaten der Kerberos-Authentifizierung überprüfen, können ab Ende Januar möglicherweise neue Metadaten vor der Authentifizierung beobachten.
Datum:
Januar 2026
Freigabe:
9.8
QUX: Appliance-Schnittstelle
Abdeckung
Verbesserungen für eine schnelle Freigabe
Die folgenden Verbesserungen wurden seit dem letzten Software-Release-Zyklus an den Algorithmen vorgenommen. Kunden, die mit dem Update-Service von Vectra verbunden sind und den Remote-Support aktiviert haben, haben diese Verbesserungen erhalten. Alle anderen Kunden erhalten die folgenden Verbesserungen als Teil dieser Version:
- Vectra AI die Umstellung von zuvor über die Suricata-Engine bereitgestellten Erkennungen auf native Erkennungen Vectra AI , die direkt auf der Vectra-Flow-Engine ausgeführt werden. Diese fortlaufenden Bemühungen stellen sicher, dass allen Kunden erweiterte Funktionen zur Erkennung von Angreiferverhalten zur Verfügung stehen, ohne dass Suspect Protocol Activity (SPA) oder signaturbasierte Erkennungslogik erforderlich sind.
Diese Version enthält zusätzliche Erkennungen für Cobalt Strike, Brute Ratel und PowerShell Empire. - Vectra AI die Genauigkeit der Smash-and-Grab-Erkennung verbessert, indem sichergestellt wird, dass die Ziel-Domänennamen korrekt aktualisiert werden, wenn sie später in einer Sitzung beobachtet werden. Durch diese Verbesserung funktioniert die Whitelist-Logik wie vorgesehen, wodurch unnötige Warnmeldungen reduziert und die Genauigkeit der Smash-and-Grab-Erkennung verbessert werden.
- Vectra AI die Erkennung auf Informationsebene für Remote Management and Monitoring (RMM)-Tools verbessert, indem Anwendungsprotokolldetails korrekt in die Erkennungsmetadaten eingefügt werden. Diese Verbesserung sorgt für einen klareren Kontext auf Host-Seiten, wenn RMM-Aktivitäten beobachtet werden, und verbessert so die Klarheit der Untersuchungen, während gleichzeitig eine störungsarme, nicht bewertende Alarmierung gewährleistet bleibt.
- Vectra AI seine Mythic C2-Erkennungslogik verfeinert, um Fehlalarme zu reduzieren, indem die Auswertung von Serverzertifikatsfeldern verschärft wurde. Dieses Update schränkt übermäßig breite Musterabgleiche ein, verhindert, dass harmlose Domains mit ähnlichen Begriffen Alarme auslösen, und verbessert die allgemeine Erkennungsgenauigkeit.
Neue Erkennung: Verdächtige Azure-Operation – Änderung der DNS-Sicherheitsrichtlinie
Vectra AI eine neue Erkennungsfunktion eingeführt, die verdächtige Verhaltensweisen im Zusammenhang mit Änderungen an der Protokollierung des Netzwerkdatenflusses aufdeckt. Die neue Erkennungsfunktion „Azure Suspect Operation – DNS Security Policy Modification” (Verdächtige Azure-Vorgänge – Änderung der DNS-Sicherheitsrichtlinie) wurde entwickelt, um Aktionen aufzudecken, bei denen eine Entität beim Löschen oder Ändern einer mit einer DNS-Sicherheitsrichtlinie verbundenen Ressource beobachtet wurde. Dies könnte die Protokollierung von DNS-Abfragen deaktivieren oder auf andere Weise die DNS-Auflösung innerhalb der Azure-Umgebung manipulieren. Bedrohungsakteure nutzen diese Technik, um die Protokollierung zu beeinträchtigen und der Erkennung zu entgehen.
Neue Erkennung: Verdächtige Azure-Operation – Flow-Protokolle deaktiviert
Vectra AI eine neue Erkennungsfunktion eingeführt, die verdächtige Verhaltensweisen im Zusammenhang mit Änderungen an der Netzwerkflussprotokollierung aufdeckt. Die neue Erkennungsfunktion „Azure Suspect Operation – Flow Logs Disabled” (Verdächtige Azure-Vorgänge – Flussprotokolle deaktiviert) wurde entwickelt, um Aktionen aufzudecken, bei denen eine Entität beim Löschen einer Azure-Flussprotokollressource beobachtet wurde. Dies deutet auf die Entfernung der Flussprotokollierung für ein VNet, ein Subnetz oder eine Netzwerkkarte hin und ist eine bekannte Technik zur Umgehung cloud , die von Angreifern genutzt wird, um die Sichtbarkeit und Überprüfbarkeit von Aktionen zu beeinträchtigen.
Neue Erkennung: Verdächtige Azure-Operation – Änderung der Netzwerksicherheitskonfiguration
Vectra AI eine neue Erkennungsfunktion eingeführt, die verdächtige Verhaltensweisen im Zusammenhang mit Änderungen an Netzwerksicherheitskonfigurationen aufdeckt. Die neue Erkennungsfunktion „Azure Suspect Operation – Network Security Config Change” (Verdächtige Vorgänge in Azure – Änderung der Netzwerksicherheitskonfiguration) wurde entwickelt, um Aktionen aufzudecken, bei denen eine Entität unerwartet eine Azure-Netzwerksicherheitsgruppe (NSG) erstellt oder ändert oder eine Azure-Firewall-Ressource modifiziert. Dies kann auf laterale Bewegungen innerhalb des Netzwerks oder einen Versuch hinweisen, die Abwehrmaßnahmen zu beeinträchtigen.
Neue Erkennung: Verdächtige Azure-Operation – Löschung mit hohem Risiko
Vectra AI eine neue Erkennungsfunktion eingeführt, die verdächtige Verhaltensweisen im Zusammenhang mit risikoreichen Löschvorgängen in einer Azure-Umgebung aufdeckt. Die neue Erkennungsfunktion „Azure Suspect Operation – High-Risk Deletion” (Verdächtige Vorgänge in Azure – risikoreiche Löschvorgänge) wurde entwickelt, um Aktionen wie das Entfernen sensibler Backups und Unveränderbarkeitsrichtlinien aufzudecken, die Angreifer nutzen könnten, um Abwehrmaßnahmen zu umgehen und Schaden anzurichten. Diese Erkennungsfunktion stärkt den Schutz vor cloud wie Storm-0501, die diese Techniken in dokumentierten Angriffen eingesetzt haben.
Verbesserung der Erkennung: Azure TOR-Aktivität
Das Azure TOR-Aktivitätserkennungsmodell wurde verbessert, um die Priorisierung der mit diesem Verhalten verbundenen Entitäten zu optimieren. Künftig Vectra AI den Entitäten, die dieses Verhalten aufweisen, mehr Gewicht beimessen, damit sie umgehend auf der Seite „Respond“ (Reagieren) angezeigt werden. Kunden können aufgrund dieser Änderung einen leichten Anstieg der priorisierten Entitäten feststellen.
Neue Erkennung: Azure AD Verdächtige Operation: Gastbenutzer hinzugefügt
Vectra AI eine neue Erkennungsfunktion eingeführt, die verdächtige Verhaltensweisen im Zusammenhang mit dem ersten Zugriff aufdeckt. Die neue Erkennungsfunktion „Azure AD Suspect Operation: Guest User Added” (Verdächtige Azure AD-Operation: Gastbenutzer hinzugefügt) wurde entwickelt, um Verhaltensweisen aufzudecken, bei denen ein Prinzipal einen externen Gastbenutzer in die Umgebung einlädt, was nicht mit dem beobachteten Verhaltensprofil des Prinzipals übereinstimmt. Diese Methode wird von Angreifern in Social-Engineering-Kampagnen verwendet, um Zugriff auf die Umgebung des Opfers zu erlangen und dort zu bleiben.
Neue Erkennung: Azure AD Verdächtige Operation: Ungewöhnliche Anmeldung über einen Proxy
Vectra AI eine neue Erkennungsfunktion eingeführt, die verdächtige Verhaltensweisen im Zusammenhang mit dem ersten Zugriff aufdeckt. Die neue Erkennungsfunktion „Azure AD Suspect Operation: Unusual Sign-On from a Proxy” (Verdächtige Azure AD-Operation: Ungewöhnliche Anmeldung über einen Proxy) wurde entwickelt, um Aktionen aufzudecken, bei denen ein Prinzipal sich über einen Proxy oder ein VPN anmeldet, was nicht seinem normalen Verhalten entspricht. Dies ist eine Methode, mit der Angreifer ihren tatsächlichen Standort verschleiern. Diese Erkennungsmethode ist die erste, die die neue Threat Intelligence-Engine Vectra AI nutzt – eine Sammlung privater und lizenzierter Bedrohungs-Feeds, die umfangreiche Kontext- und Reputationsinformationen für eine möglichst hohe Signalklarheit liefern.
Kontrolle
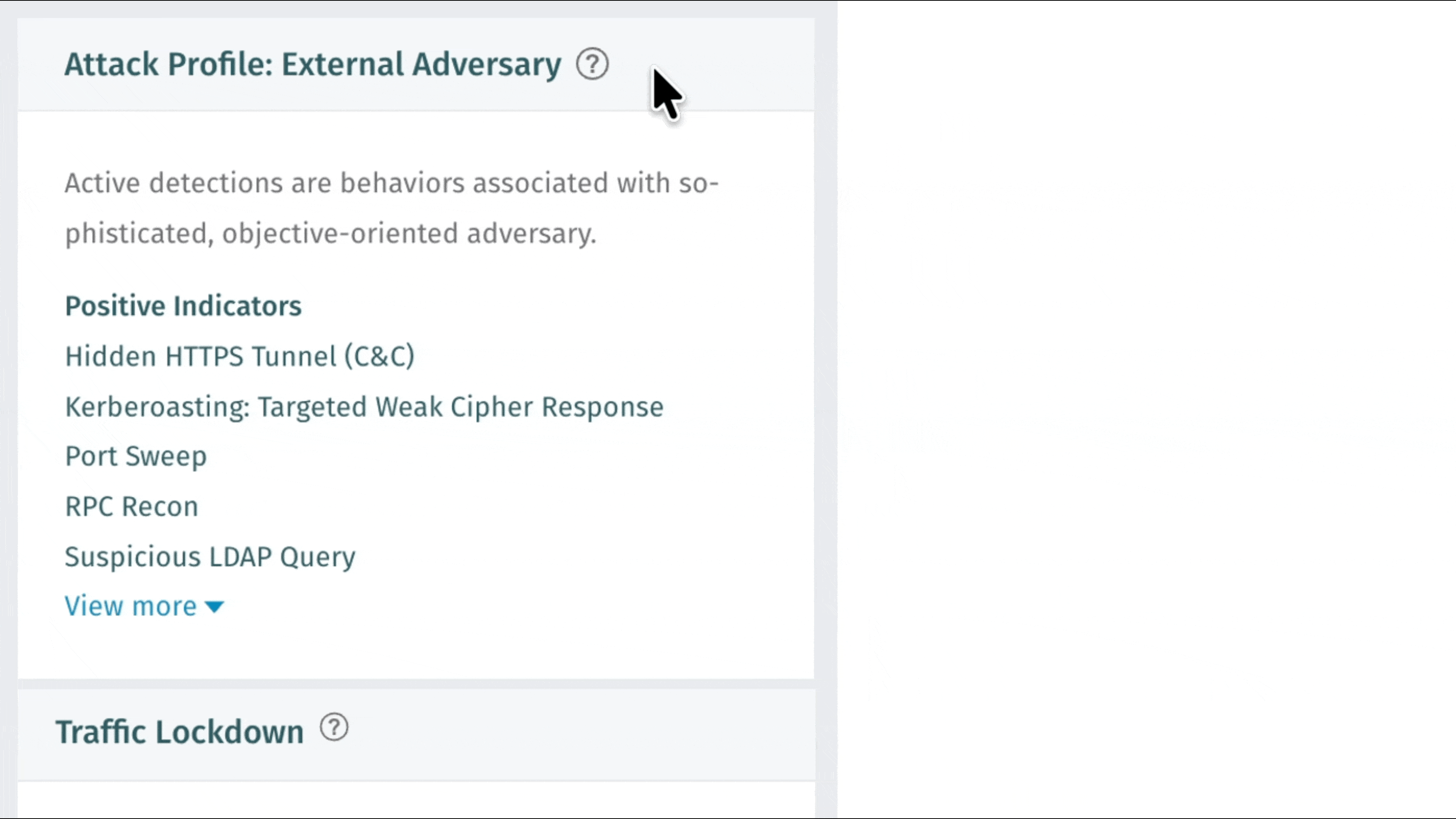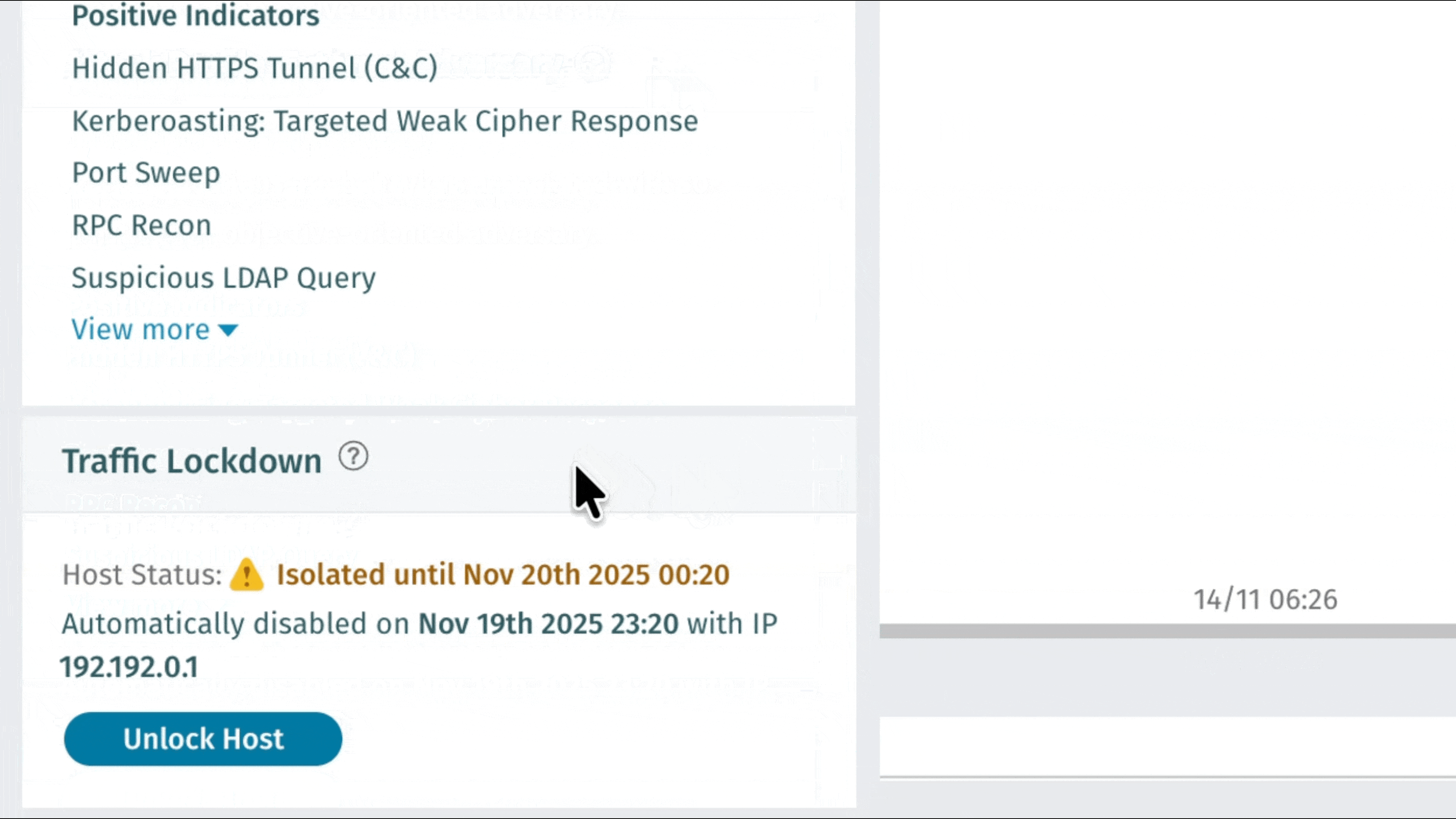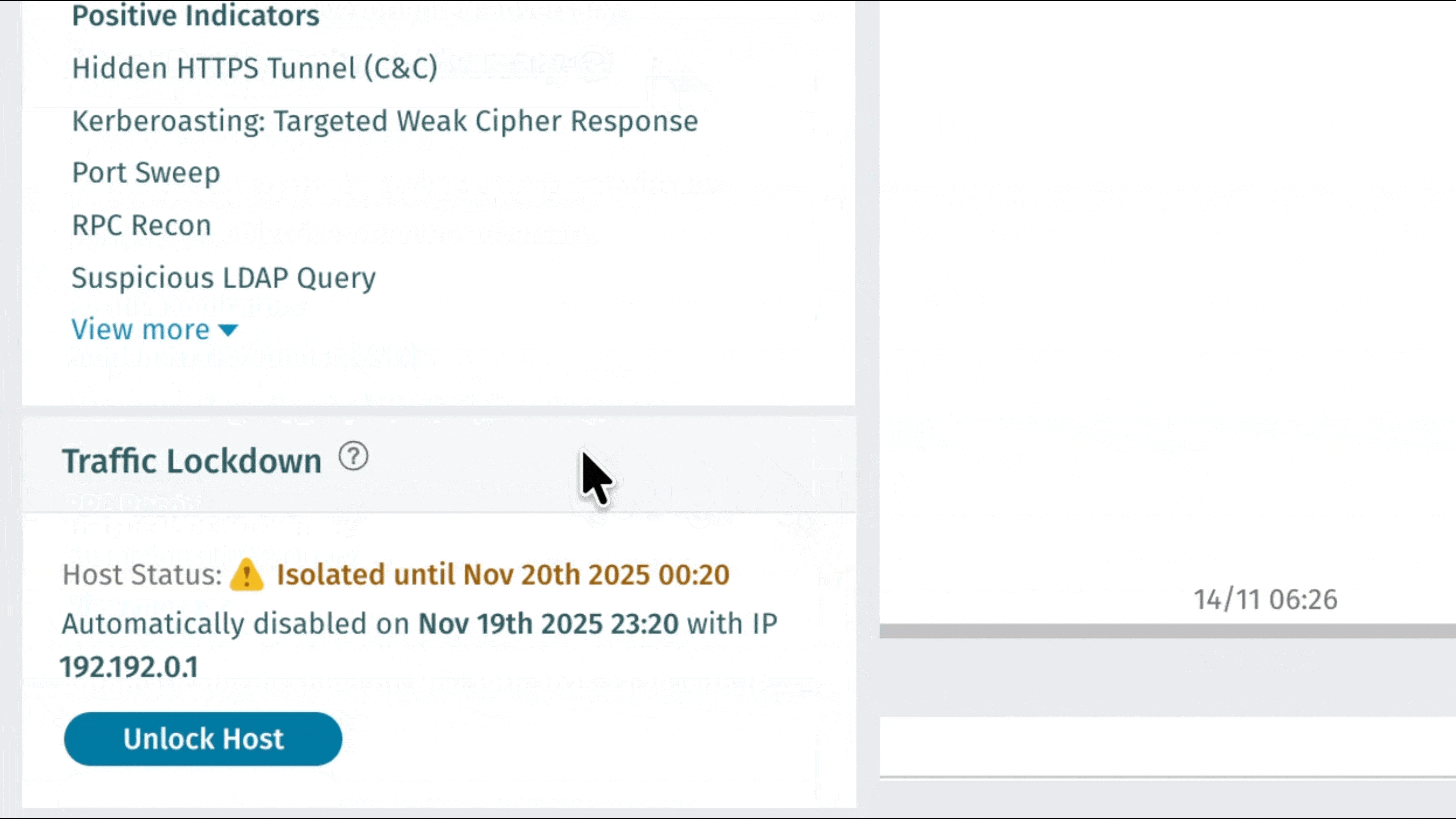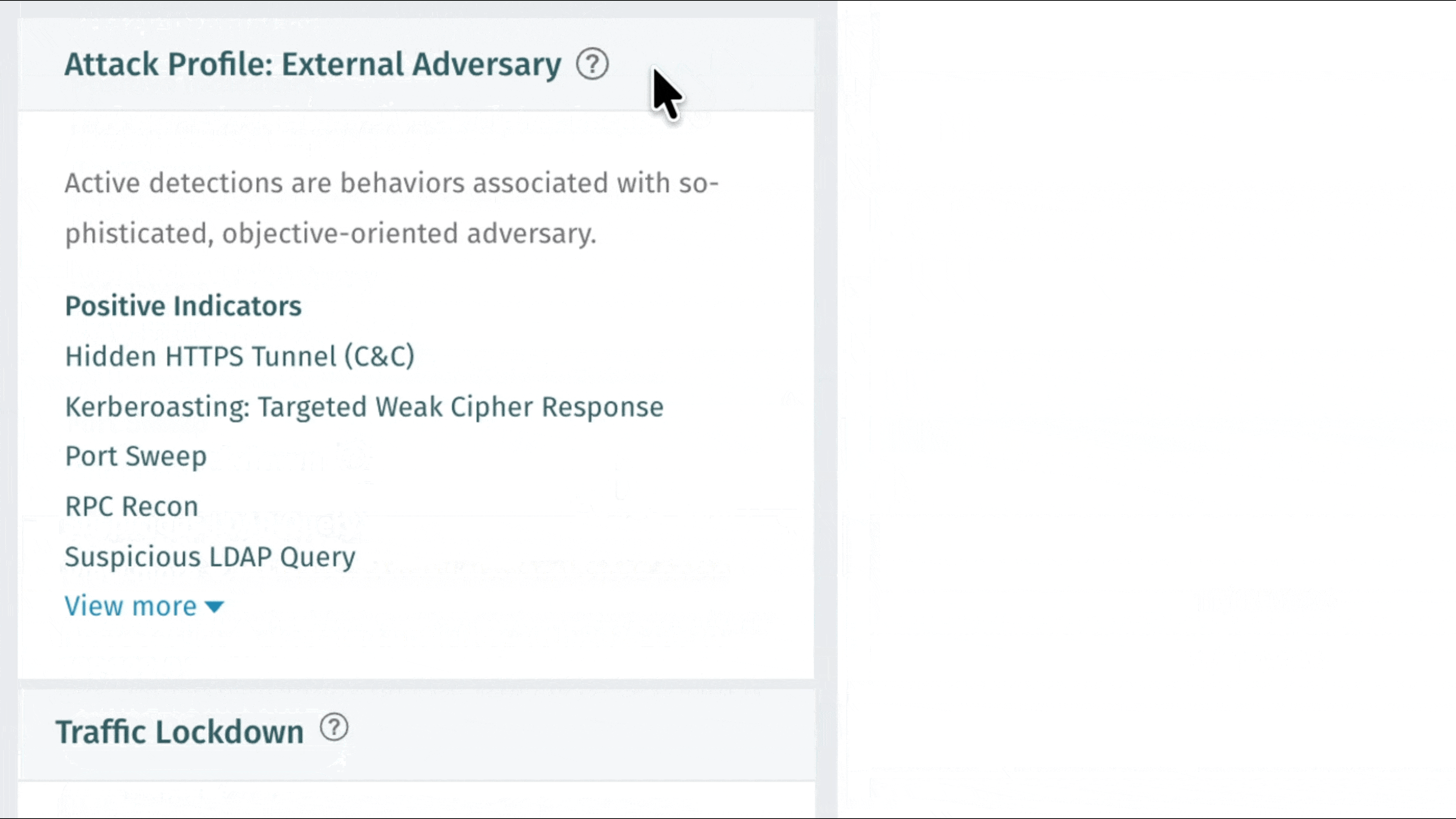
Traffic Lockdown: Automatisierte Netzwerkverteidigung durch Firewall-Integration
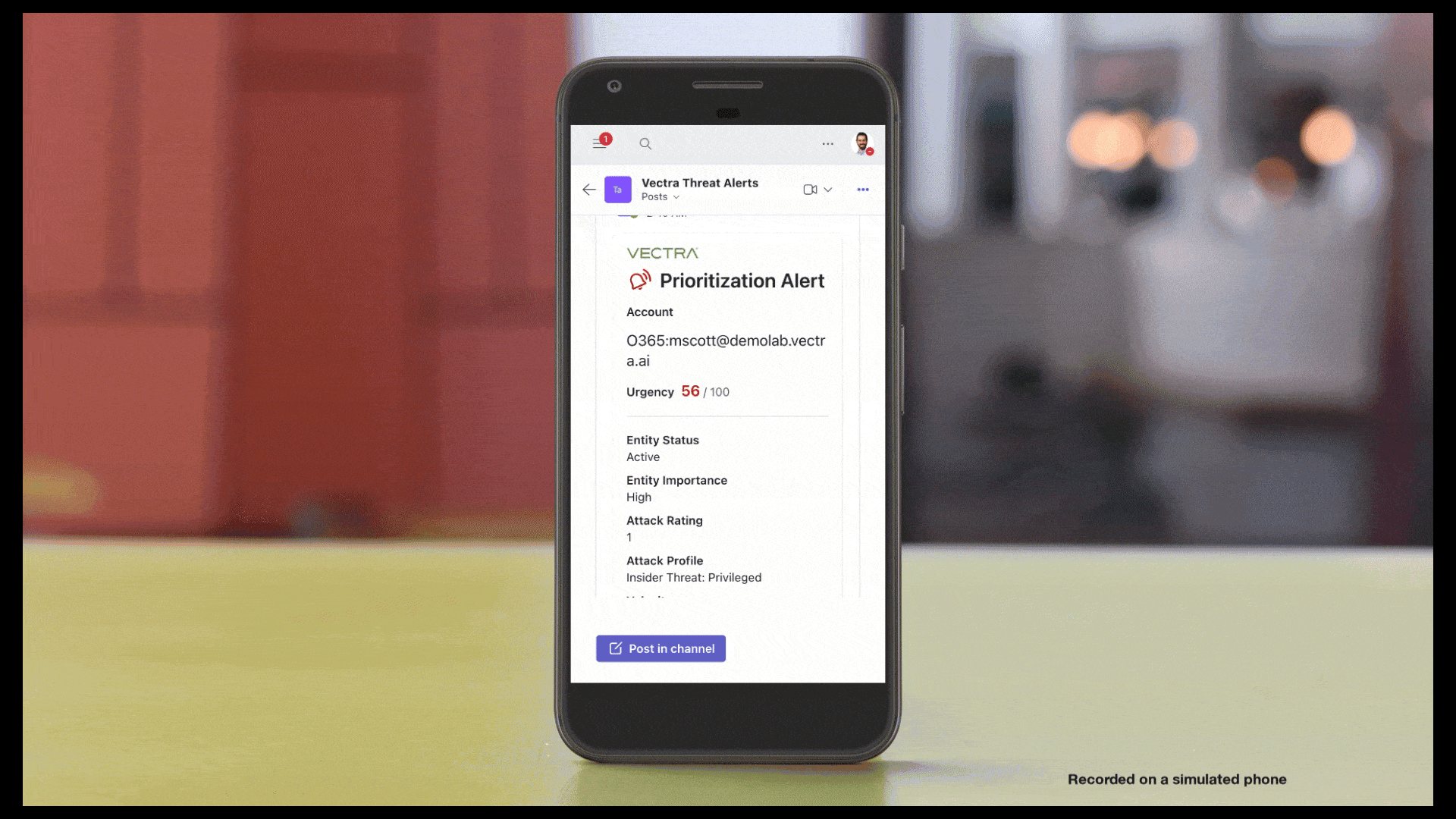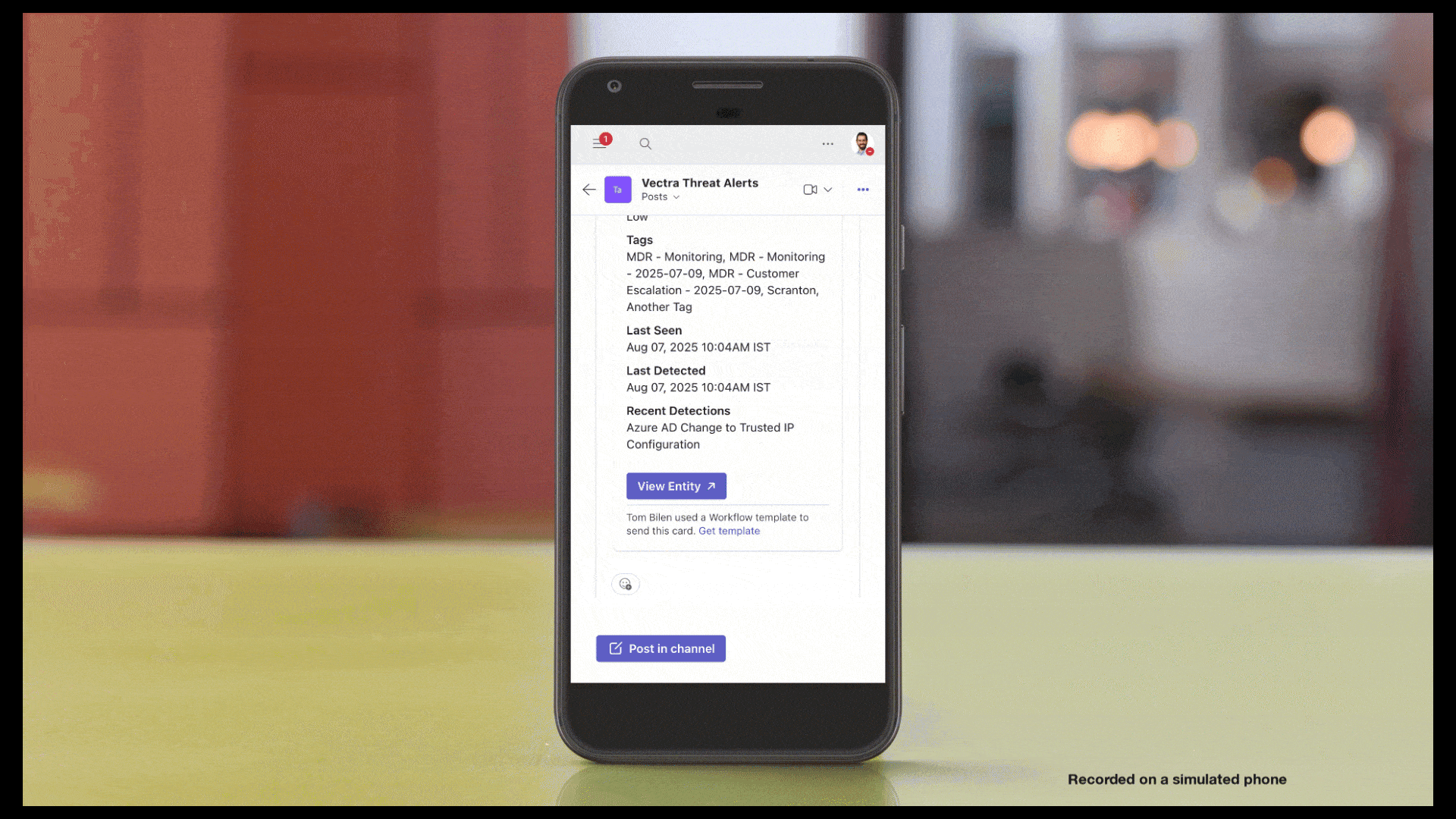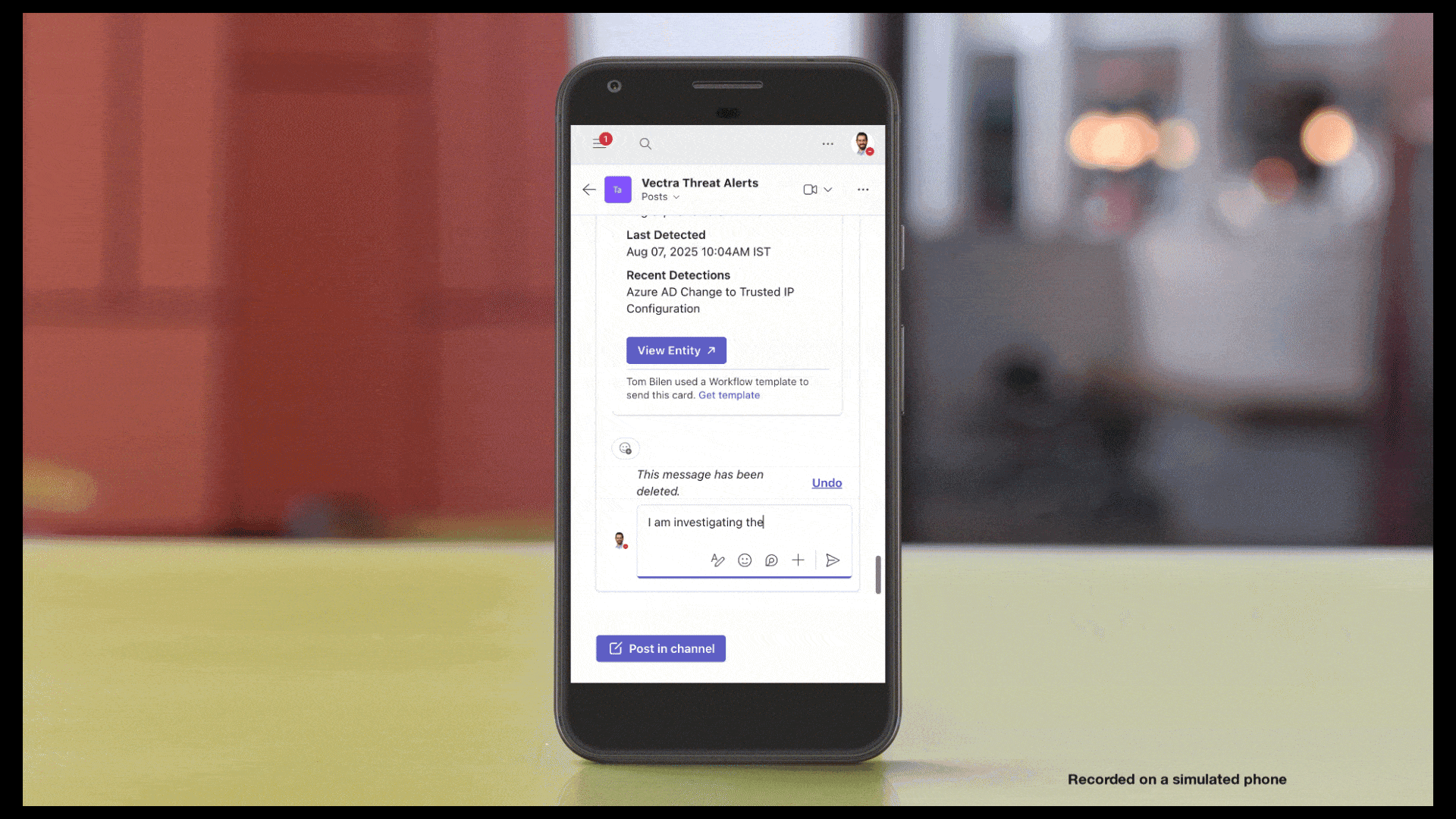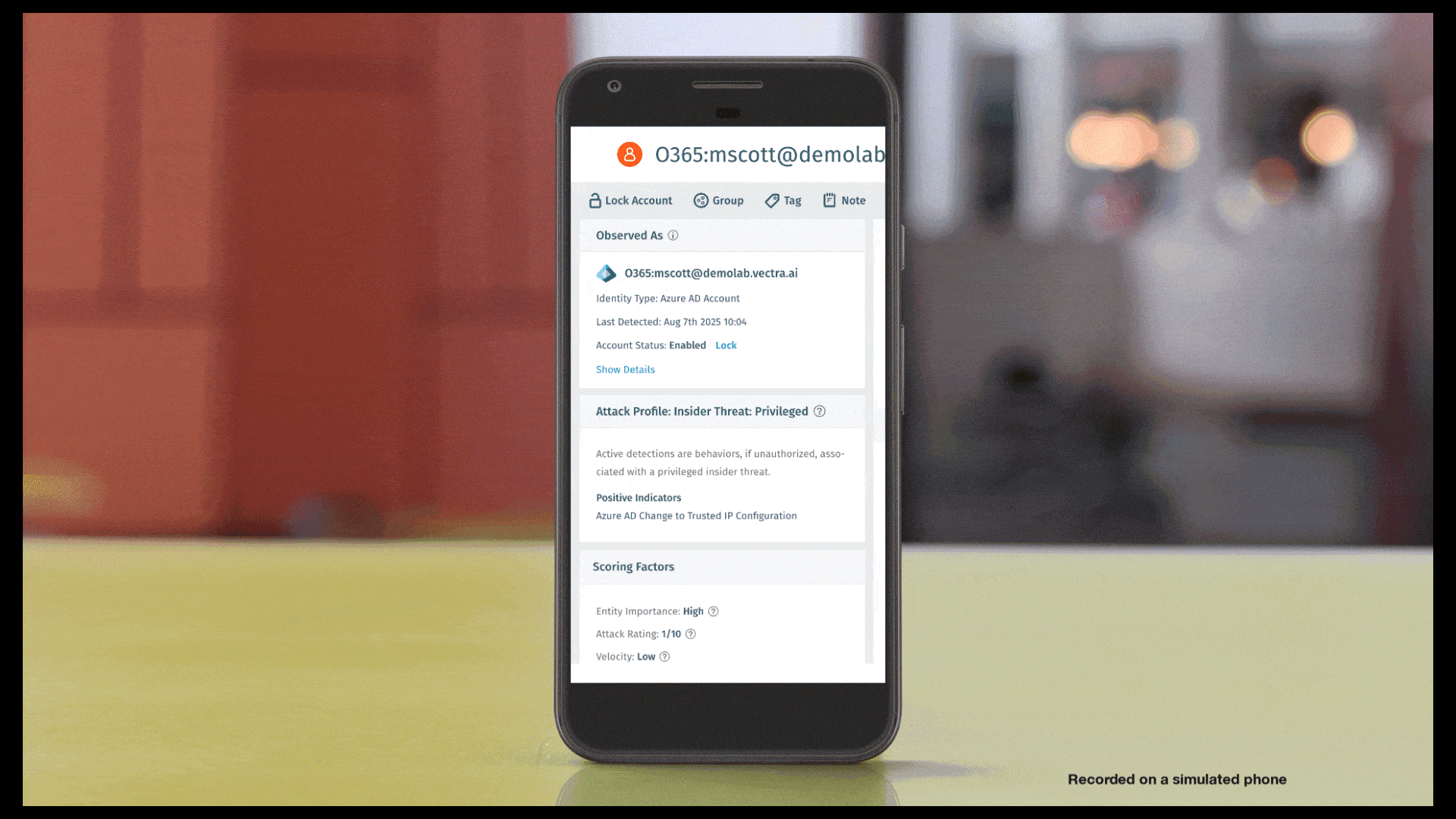
Vectra AI können Kunden Vectra AI sofort auf erkannte Bedrohungen reagieren – dank Traffic Lockdown, einer neuen Funktion, die bösartige Hosts automatisch auf Firewall-Ebene blockiert. Durch die direkte Integration in unterstützte Firewalls veröffentlicht Vectra AI IP-Adressen aus dem Threat Feed, die sofort umgesetzt werden können, ohne dass manuelle Regeln oder komplexe Einstellungen erforderlich sind. Sicherheitsteams profitieren von einer schnelleren Eindämmung, saubereren Arbeitsabläufen und einem stärkeren Schutz dort, wo es am wichtigsten ist: am Netzwerkrand. Konfigurationsanweisungen finden Sie unter Traffic Lockdown. Weitere Informationen erhalten Sie in diesem Podcast:
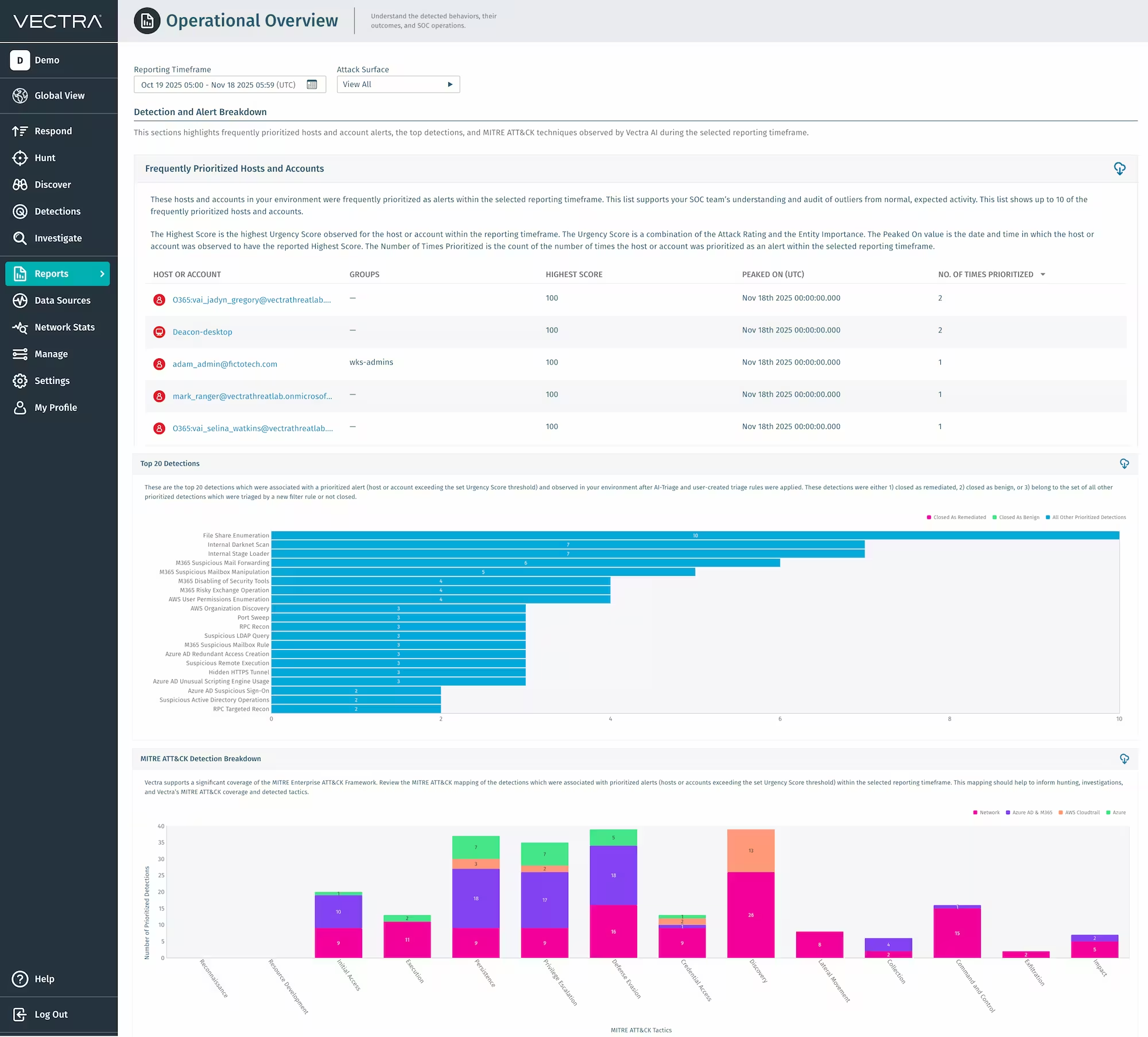
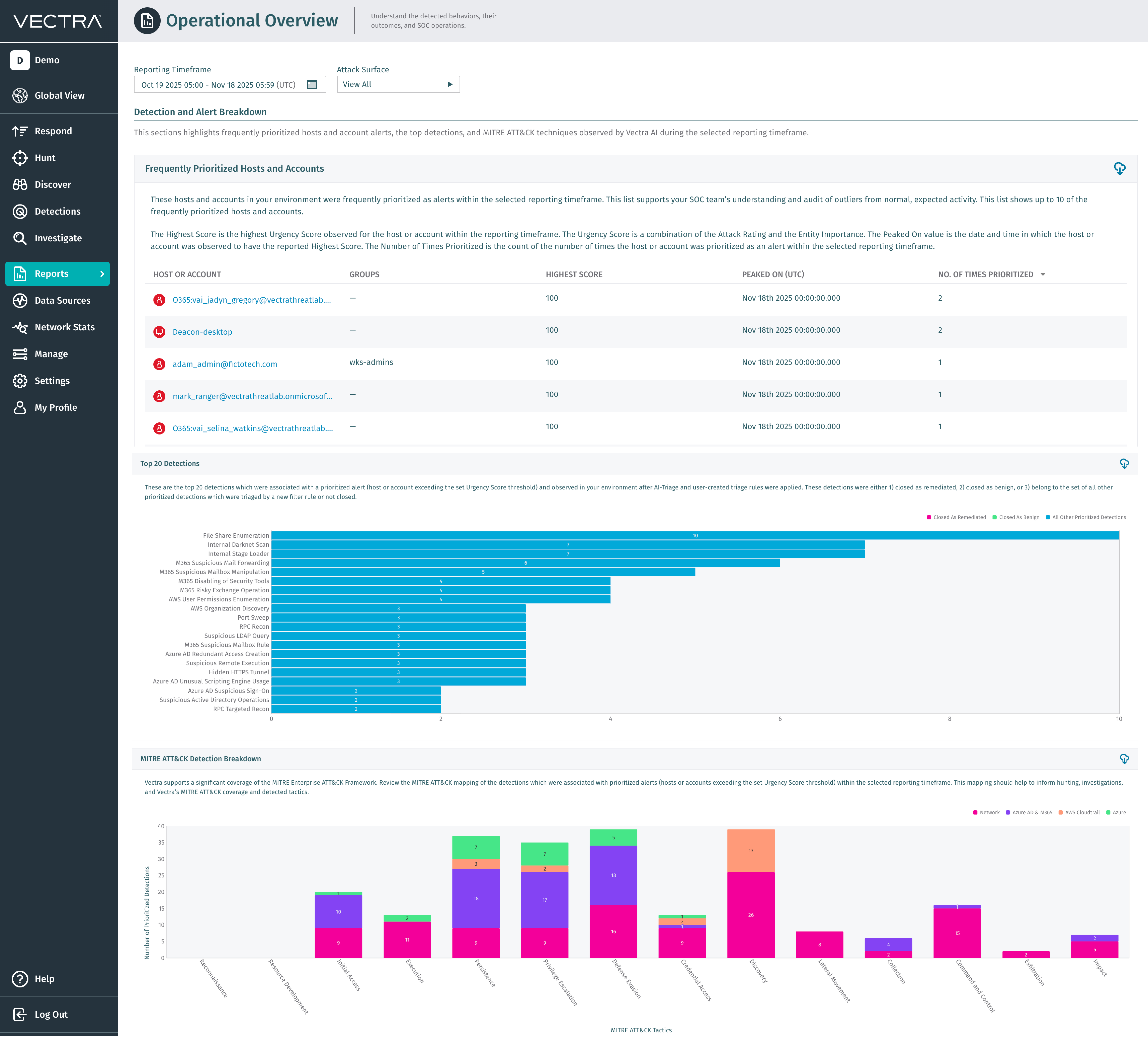
Betriebsübersichtsbericht
Wir stellen Ihnen den Betriebsübersichtsbericht vor – die neue Kommandoansicht Ihres SOC für Leistung und Wirkung. Dieser Bericht fasst wichtige Kennzahlen wie die durchschnittliche Zeit bis zur Zuweisung, die durchschnittliche Zeit bis zur Untersuchung und die durchschnittliche Zeit bis zur Lösung zusammen mit den wichtigsten Erkennungen, MITRE ATT&CK und priorisierten Entitäten in einem übersichtlichen, visuellen Dashboard zusammen. Er quantifiziert, wie Vectra AI schnellere Untersuchungen, eine präzisere Triage und messbare Effizienzsteigerungen Vectra AI . Mit aussagekräftigen Erkenntnissen für Geschäftsberichte, Führungskräfteberichte und den täglichen Betrieb verwandelt er Leistungsdaten in einen Wertnachweis. Weitere Informationen finden Sie in diesem Podcast:
Architektur/Verwaltung
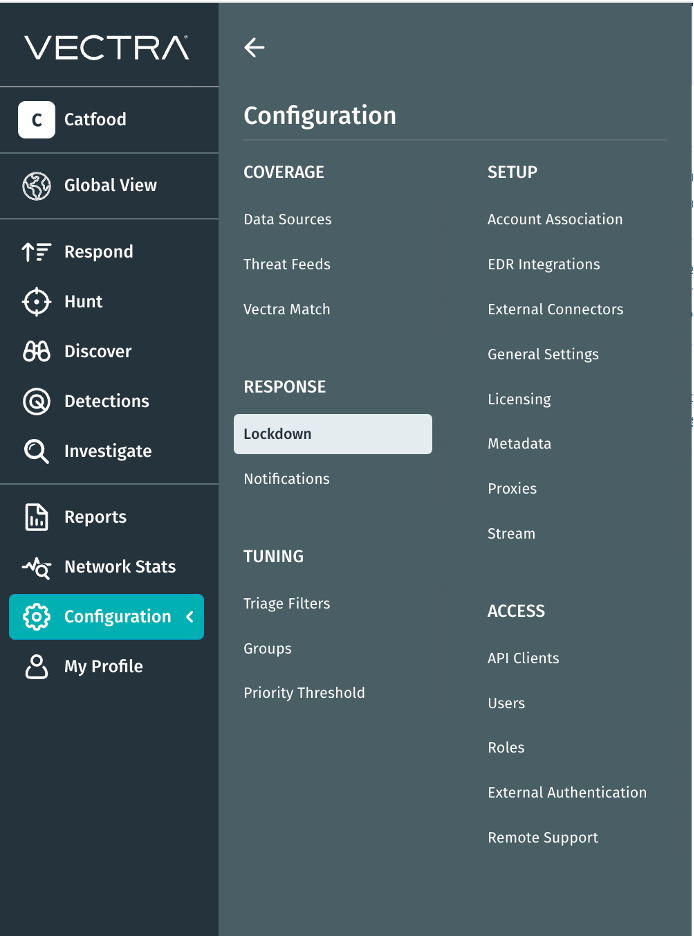
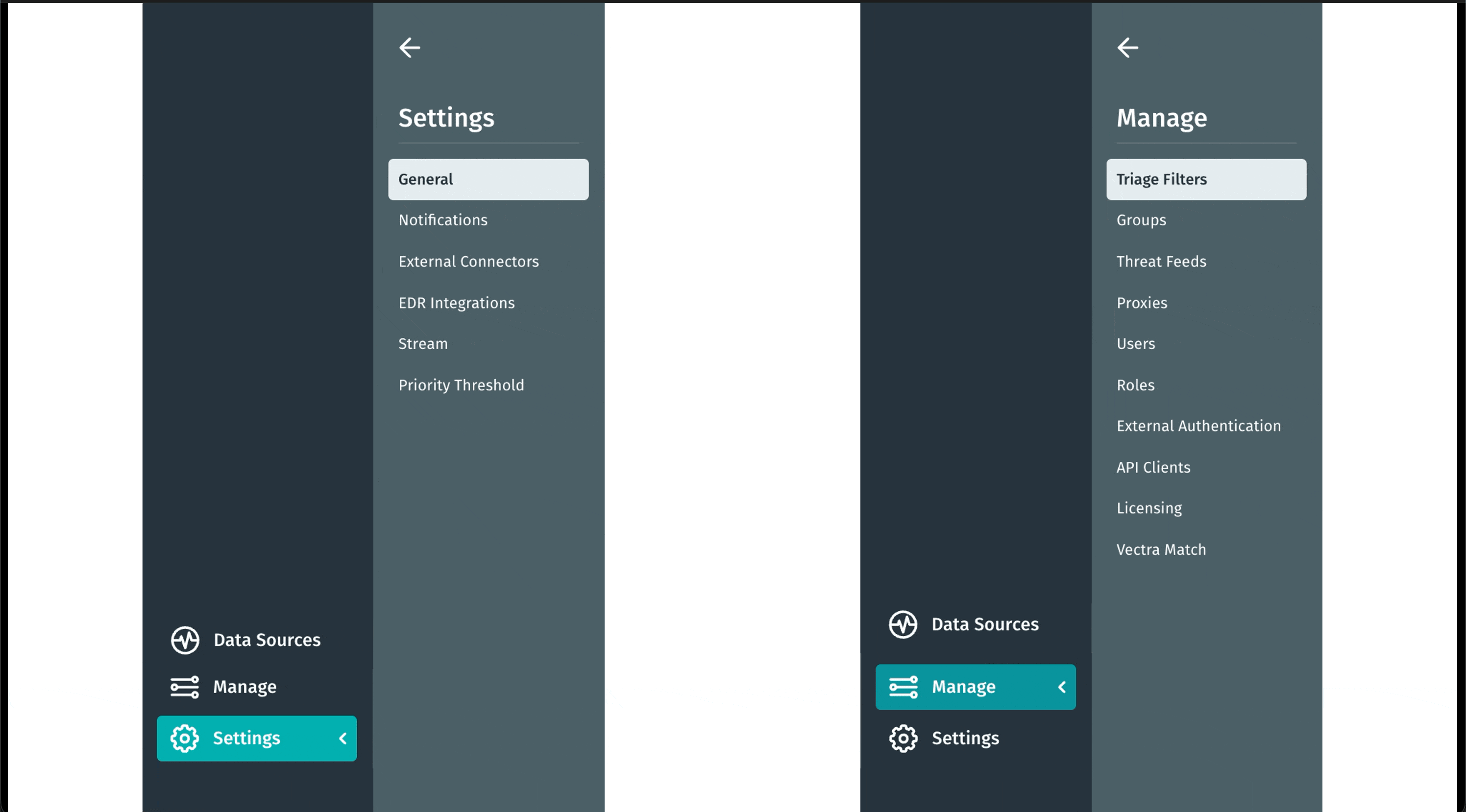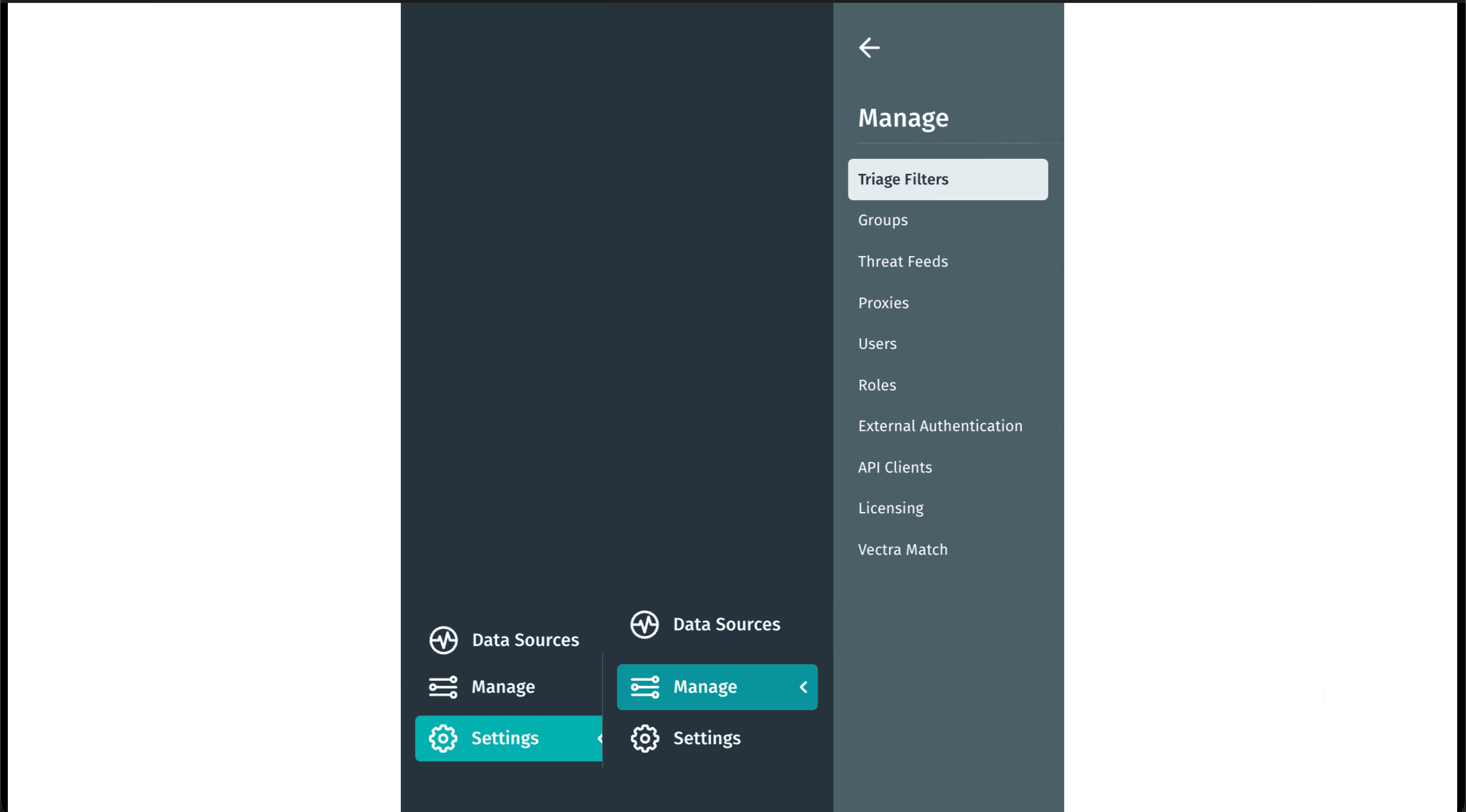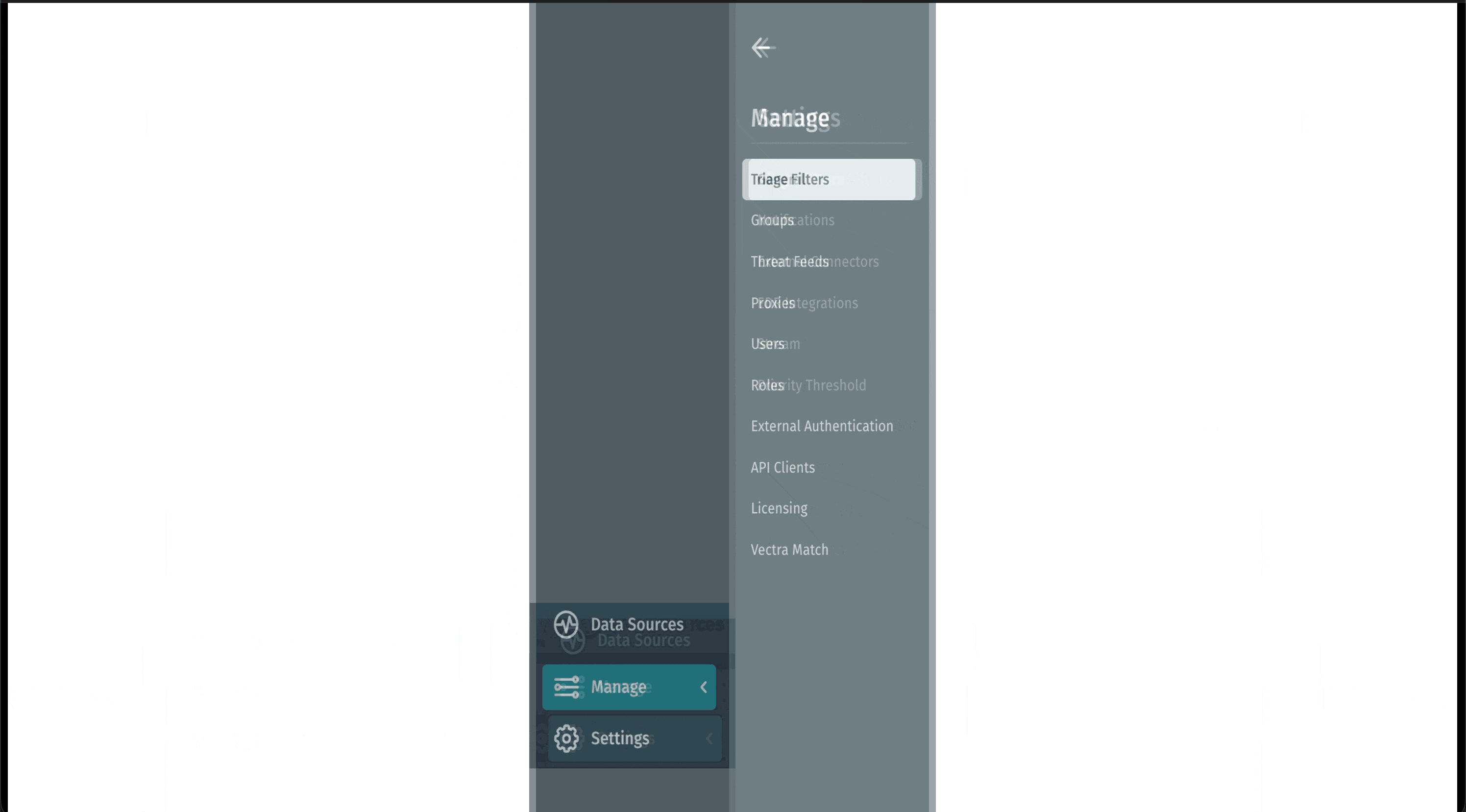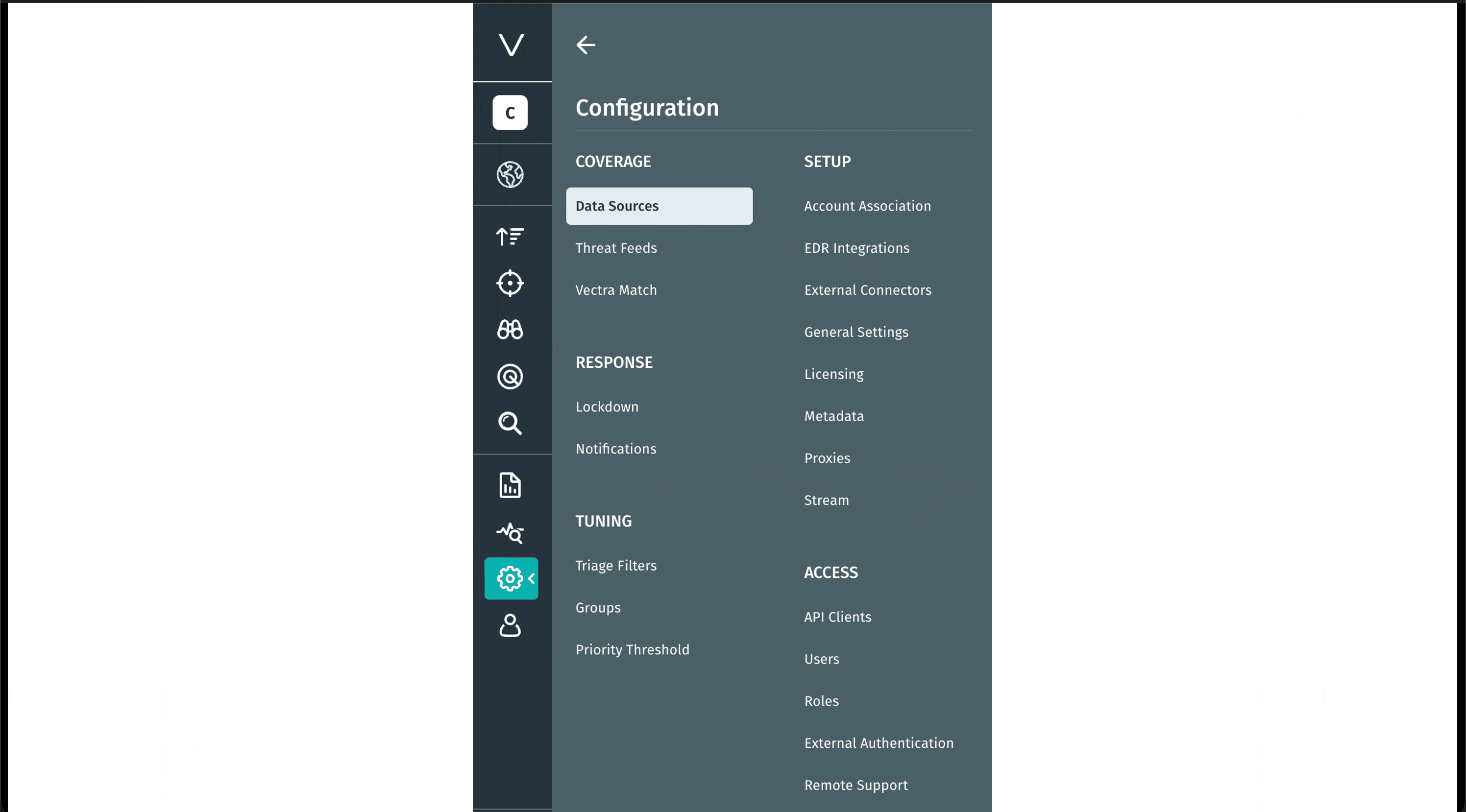
Navigationsänderung: Konfiguration
Wir haben die Verwaltung Ihrer Umgebung in der Vectra AI optimiert. Die neue Registerkarte „Konfiguration“ vereint die Optionen „Verwalten“ und „Einstellungen“, sodass alle Konfigurations- und Steuerungseinstellungen in einer übersichtlichen, intuitiven Ansicht zusammengefasst sind. So finden Sie schneller, was Sie suchen, und können sicher handeln. Dieses Update beseitigt Reibungsverluste und vereinfacht die Navigation. Weniger suchen. Mehr tun.
Syslog-Zertifikatsvalidierung
Vectra 9.8 bietet nun Unterstützung für die Validierung von Serverzertifikaten für Syslog-Ziele unter Verwendung von TLS. Die Validierung wird über ein Kontrollkästchen in der Syslog-Konfiguration gesteuert, sodass Kunden ihre Zertifikate vor der Aktivierung der Validierung bestätigen können. Befolgen Sie die Konfigurationsschritte im Syslog-Handbuch von Vectra, um weitere Anweisungen zu erhalten.
Hinweis: Während dieses Updates haben wir auch ein früheres Problem identifiziert, das in bestimmten Konfigurationen zum Fehlen eines Server-CA-Zertifikats führen konnte. Kunden sollten ihre Syslog-Einstellungen unter „Konfiguration > Reaktion > Benachrichtigungen“ überprüfen, um sicherzustellen, dass alle erforderlichen Zertifikate vorhanden sind.
SSH-Anmeldung bei Vectra-Geräten (private Vorschau)
Vectra AI den Zugriff von Administratoren auf Geräte über SSH vereinfacht und übersichtlicher gestaltet. Autorisierte UI-Benutzer können sich nun mit ihren eigenen SSH-Anmeldedaten anmelden, anstatt auf die gemeinsam genutzten Anmeldedaten zurückgreifen zu müssen. Vektoren Konto. Administratoren können persönliche SSH-Schlüssel und CLI-Passwörter direkt über die Web-Benutzeroberfläche verwalten. Diese Aktualisierungen erleichtern es Teams, Best Practices zu befolgen, die Abhängigkeit von Standard-Anmeldedaten zu verringern und einen sicheren administrativen Zugriff aufrechtzuerhalten. Weitere Informationen finden Sie unter SSH-Anmeldung bei Vectra-Geräten – Dokumentationshandbuch.
GCP-Bereitstellungen werden zu Infrastructure Manager migriert
GCP-Bereitstellungen verwenden nun Infrastructure Manager, der Deployment Manager ersetzt und so kontinuierlichen Support und eine zuverlässigere Bereitstellung gewährleistet. Dieses Update vereinfacht die Bereitstellung von Vectra-Brains und -Sensoren auf GCP und ersetzt veraltete Tools durch einen modernen, standardisierten Ansatz.
- Die Bereitstellungshandbücher werden diese Woche mit dem Infrastrukturmanager-Prozess aktualisiert: GCP vSensor-Bereitstellungshandbuch, GCP Brain-Bereitstellungshandbuch, Stream
Vorstellung des Vectra S127-Systems
Wir freuen uns, das neueste Mitglied der Vectra-Appliance-Familie vorstellen zu dürfen – das S127, das ab sofort bestellt werden kann! Der S127 ist der direkte Nachfolger unserer bewährten S101-Plattform und bietet die gleiche zuverlässige Leistung mit modernisierter Hardware und Raum für Wachstum. Der S127 unterstützt eine aggregierte Sensorkapazität von 58 Gbit/s und eine Leistung von 30 Gbit/s mit Match . Weitere Informationen zu den Spezifikationen der Appliance finden Sie unter Appliance- und Sensorspezifikationen.
- Die Bereitstellungsanleitung finden Sie in der S127-Schnellstartanleitung.
Datum:
Dezember 2025
Freigabe:
2025.12
RUX: SaaS-Bereitstellung
Abdeckung
Verbesserungen für eine schnelle Freigabe
Die folgenden Verbesserungen wurden seit dem letzten Software-Release-Zyklus an den Algorithmen vorgenommen. Kunden, die mit dem Update-Service von Vectra verbunden sind und den Remote-Support aktiviert haben, haben diese Verbesserungen erhalten. Alle anderen Kunden erhalten die folgenden Verbesserungen als Teil dieser Version:
- Vectra AI die Umstellung von zuvor über die Suricata-Engine bereitgestellten Erkennungen auf native Erkennungen Vectra AI , die direkt auf der Vectra-Flow-Engine ausgeführt werden. Diese fortlaufenden Bemühungen stellen sicher, dass allen Kunden erweiterte Funktionen zur Erkennung von Angreiferverhalten zur Verfügung stehen, ohne dass Suspect Protocol Activity (SPA) oder signaturbasierte Erkennungslogik erforderlich sind.
Diese Version enthält zusätzliche Erkennungen für Cobalt Strike, Brute Ratel und PowerShell Empire. - Vectra AI die Genauigkeit der Smash-and-Grab-Erkennung verbessert, indem sichergestellt wird, dass die Ziel-Domänennamen korrekt aktualisiert werden, wenn sie später in einer Sitzung beobachtet werden. Durch diese Verbesserung funktioniert die Whitelist-Logik wie vorgesehen, wodurch unnötige Warnmeldungen reduziert und die Genauigkeit der Smash-and-Grab-Erkennung verbessert werden.
- Vectra AI die Erkennung auf Informationsebene für Remote Management and Monitoring (RMM)-Tools verbessert, indem Anwendungsprotokolldetails korrekt in die Erkennungsmetadaten eingefügt werden. Diese Verbesserung sorgt für einen klareren Kontext auf Host-Seiten, wenn RMM-Aktivitäten beobachtet werden, und verbessert so die Klarheit der Untersuchungen, während gleichzeitig eine störungsarme, nicht bewertende Alarmierung gewährleistet bleibt.
- Vectra AI seine Mythic C2-Erkennungslogik verfeinert, um Fehlalarme zu reduzieren, indem die Auswertung von Serverzertifikatsfeldern verschärft wurde. Dieses Update schränkt übermäßig breite Musterabgleiche ein, verhindert, dass harmlose Domains mit ähnlichen Begriffen Alarme auslösen, und verbessert die allgemeine Erkennungsgenauigkeit.
Klarheit
EDR-Prozesskorrelation (Private Preview)
Vectra AI die CrowdStrike EDR-Prozesskorrelation für Kunden der privaten Vorschau veröffentlicht. Diese Funktion optimiert Untersuchungen, indem sie automatisch den wahrscheinlichen Prozess im Zusammenhang mit einer NDR-Erkennung findet und ihn zusammen mit der Erkennung in der Plattform und bei der Erfassung des Ereignisses über die API anzeigt.
Das Ergebnis ist eine leistungsfähigere Erkennung und Reaktion, weniger manuelle Arbeit und bessere Ergebnisse für Sicherheitsteams. Es macht eine benutzerdefinierte SIEM- oder SOAR-Korrelationslogik überflüssig und kann bis zu 30 Minuten pro Erkennung einsparen. Was war der Prozess, der C2 angetrieben hat – ein Browser oder ein PowerShell-Skript? Ist dies zu erwarten oder fällt es auf? Das sind Fragen, die Analysten sofort beantworten müssen, und diese Funktion macht das möglich. Wenden Sie sich an Ihr Vectra AI , um an der privaten Vorschau teilzunehmen, und besuchen Siedie FAQ zur Crowdstrike EDR-Integration, um Anweisungen zur Unterstützung dieser Integration zu erhalten.
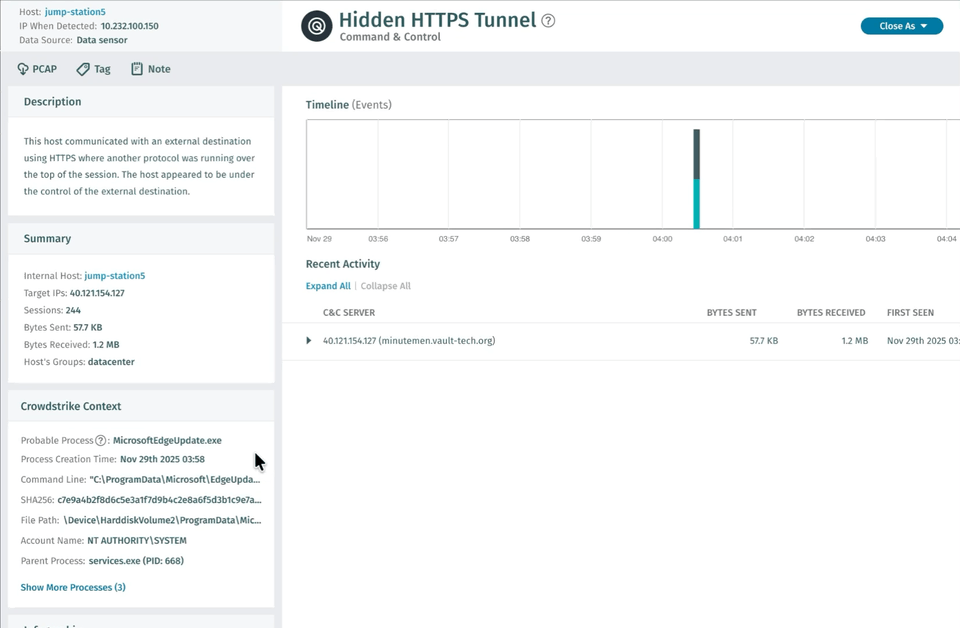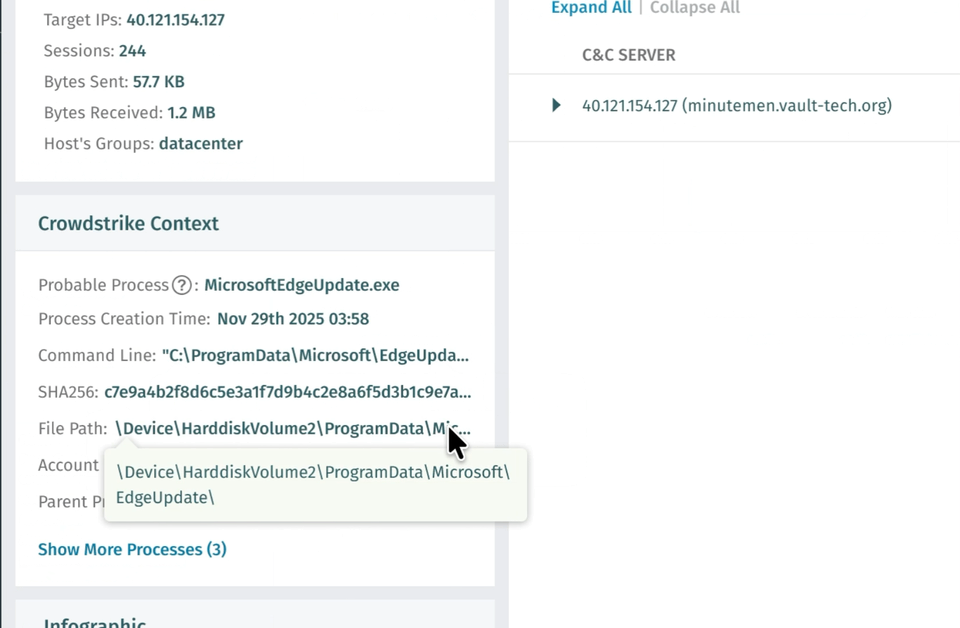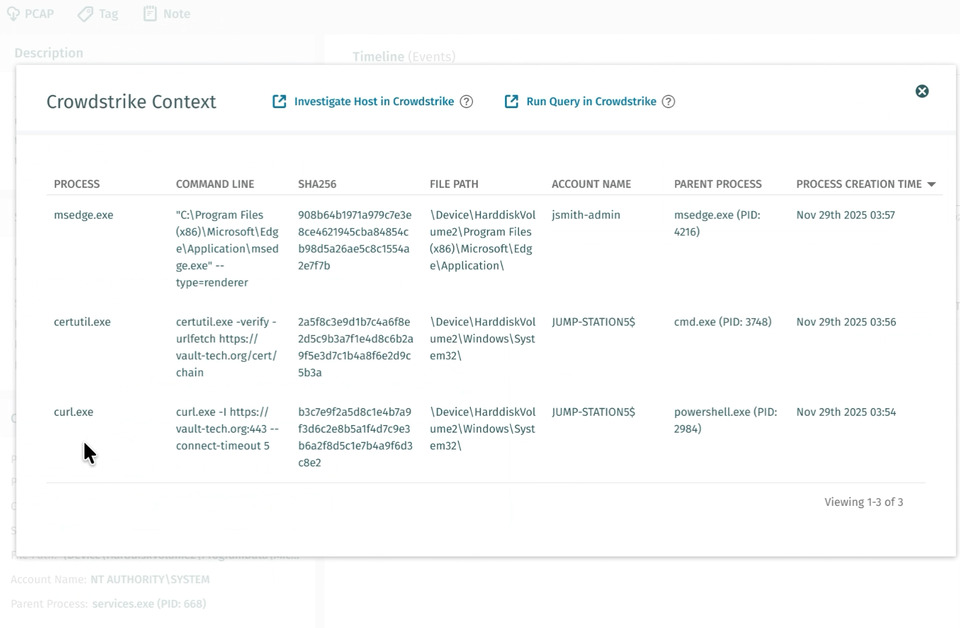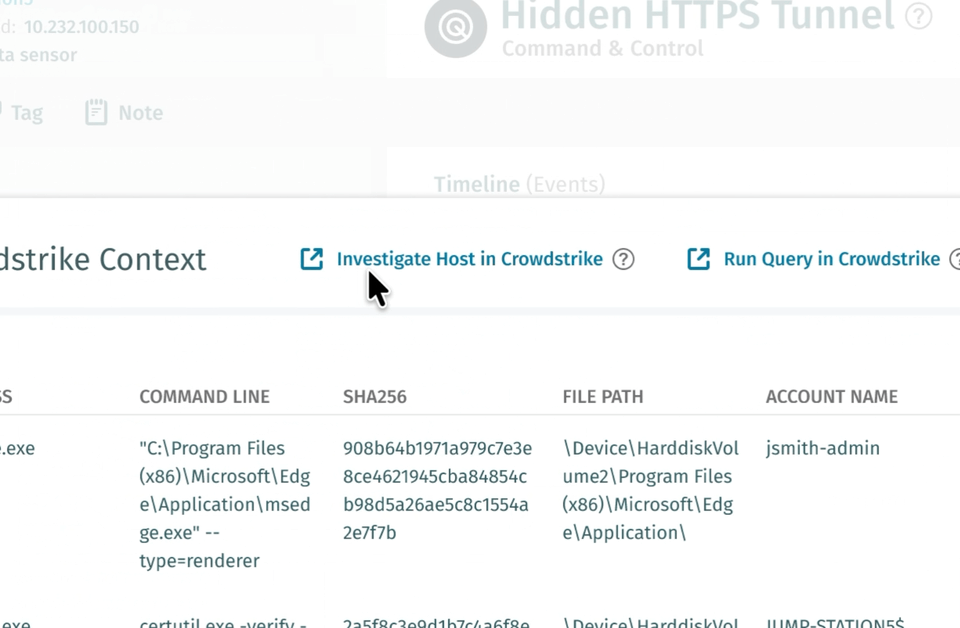
Erfahren Sie in diesem Podcast mehr darüber, wie Vectra AI mit CrowdStrike Vectra AI :
Vectra 360 Response Enhancement für Cloud
Die Account-SperrungVectra AI umfasst nun auch die Passwortzurücksetzung für AzureAD/Entra ID und bietet Kunden damit eine stärkere und zuverlässigere Möglichkeit, identitätsbasierte Angriffe, insbesondere Token-Diebstahl, proaktiv zu verhindern. Durch das Widerrufen von Sitzungen und das Erzwingen einer Passwortzurücksetzung entfernt Vectra AI den Zugriff von Angreifern, während legitime Benutzer sich mit minimalem Aufwand wieder anmelden können. Dies erweitert die 360-Response-Fähigkeit Vectra AI, die eine proaktive Reaktion über Traffic, Geräte und Identitäten hinweg ermöglicht. Weitere Informationen zu dieser Funktion finden Sie im Support-Artikel „https://support.vectra.ai/vectra/article/KB-VS-1123” (Sperren von Konten in Azure AD/Entra ID). Weitere Informationen zu dieser Funktion finden Sie unter:
Datum:
Dezember 2025
Freigabe:
9.7
QUX: Appliance-Schnittstelle
Abdeckung
Verbesserungen für eine schnelle Freigabe
Die folgenden Verbesserungen wurden seit dem letzten Software-Release-Zyklus an den Algorithmen vorgenommen. Kunden, die mit dem Update-Service von Vectra verbunden sind und den Remote-Support aktiviert haben, haben diese Verbesserungen erhalten. Alle anderen Kunden erhalten die folgenden Verbesserungen als Teil dieser Version:
- Vectra AI mehrere Cobalt Strike als native Python-Erkennungen neu. Durch die Verlagerung dieser Erkennungen in die Python-basierte Engine von Vectra profitieren nun alle Kunden von dieser Cobalt Strike , ohne sich auf signaturbasierte Logik verlassen zu müssen.
- Vectra AI seine Kali Repo Usage-Erkennung verfeinert, um die Genauigkeit zu verbessern und Fehlalarme zu reduzieren, indem die Identifizierung von Kali-bezogenen User Agents verschärft wurde. Diese Verbesserung konzentriert die Übereinstimmungskriterien auf echte Kali Linux-Aktivitäten und gewährleistet so zuverlässigere Warnmeldungen und zuverlässigere Erkenntnisse bei der Untersuchung potenzieller Angreifer-Tools.
- Vectra AI neue Erkennungsfunktionen auf Informationsebene für Remote Management and Monitoring (RMM)-Tools eingeführt, die in Kundenumgebungen beobachtet werden. Da RMM-Dienstprogramme zunehmend bei Cyberangriffen eingesetzt werden, bieten diese Warnmeldungen Einblick in ihre Verwendung, ohne Störungen zu verursachen oder die Bewertung zu beeinflussen. Die Benachrichtigungen werden auf einzelnen Host-Seiten angezeigt – eine pro Host-Sitzung – und bleiben auf der Hauptseite „Erkennungen“ verborgen, sofern keine Filter angepasst werden. Dieses Update bietet Kunden einen klareren Einblick in potenziell sensible Verwaltungsaktivitäten und sorgt gleichzeitig für eine Warnmeldung mit geringen Auswirkungen.
Klarheit
Gruppen auf der Grundlage der Active Directory-Mitgliedschaft in Quadrant UX
Bringen Sie Ihre bestehenden AD-Gruppen nahtlos in Vectra ein und halten Sie sie perfekt synchron - keine manuelle Neuerstellung oder mühsame Pflege mehr. Durch den Massenimport entfällt die sich wiederholende Verwaltungsarbeit, sodass sich Ihre Teams auf die threat hunting und nicht auf die Gruppenverwaltung konzentrieren können. Durch die Straffung der Triage-Regeln und die Reduzierung des Rauschens können Sie schneller auf die wirklich wichtigen Alarme reagieren. Das ist Effizienz und Signalklarheit, direkt eingebaut. Besuchen Sie Active Directory (AD)-Gruppen für weitere Informationen.
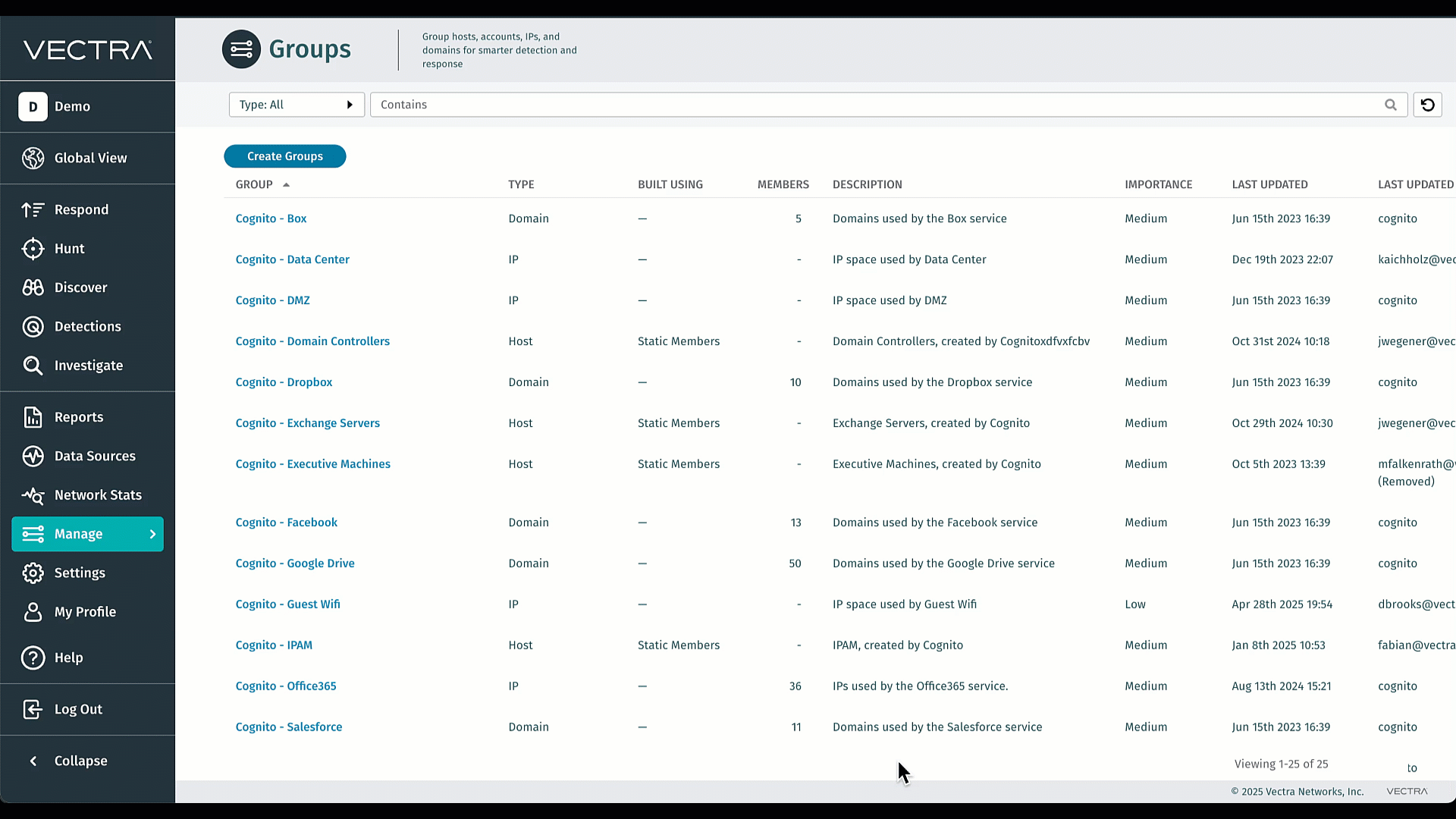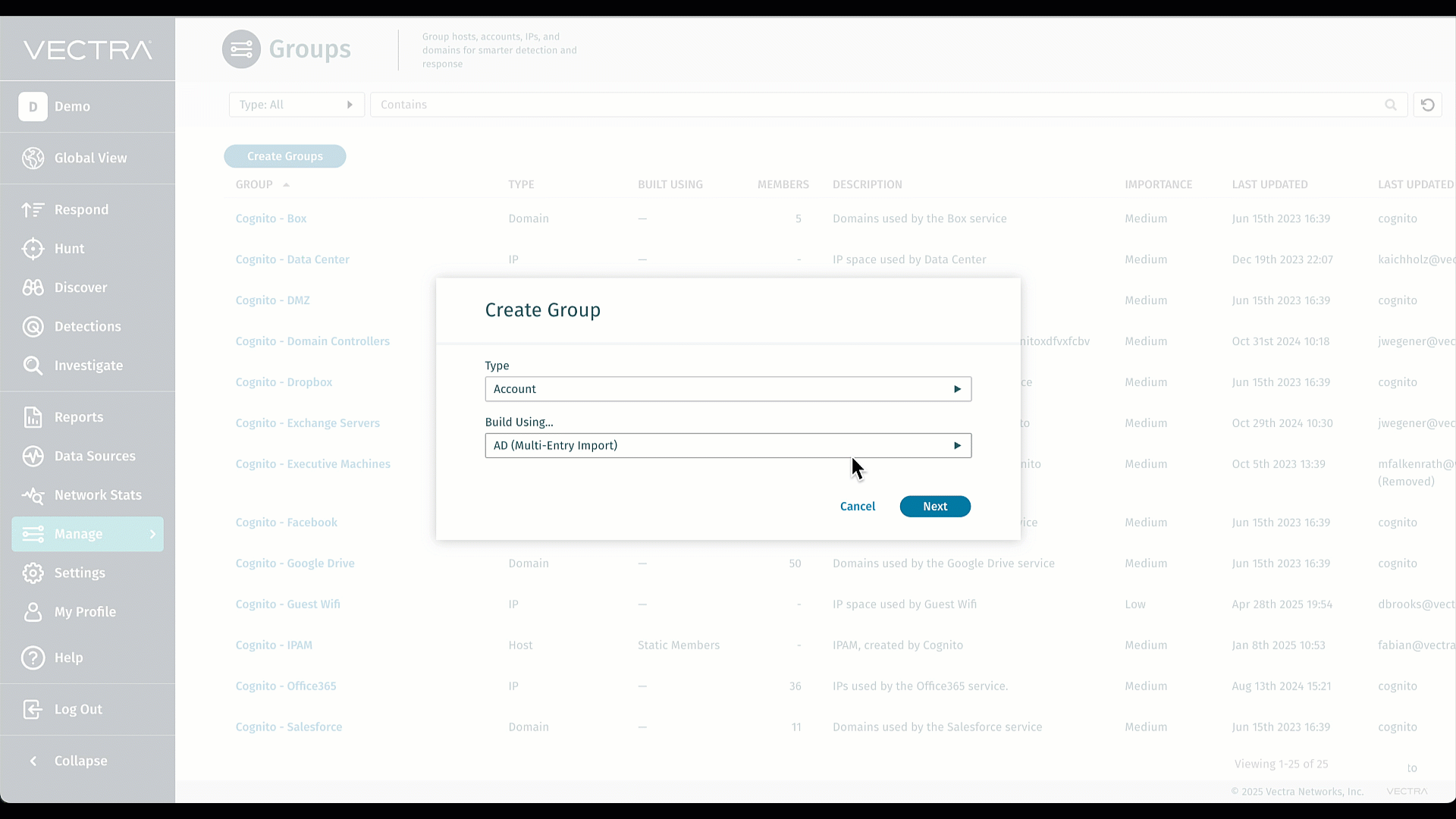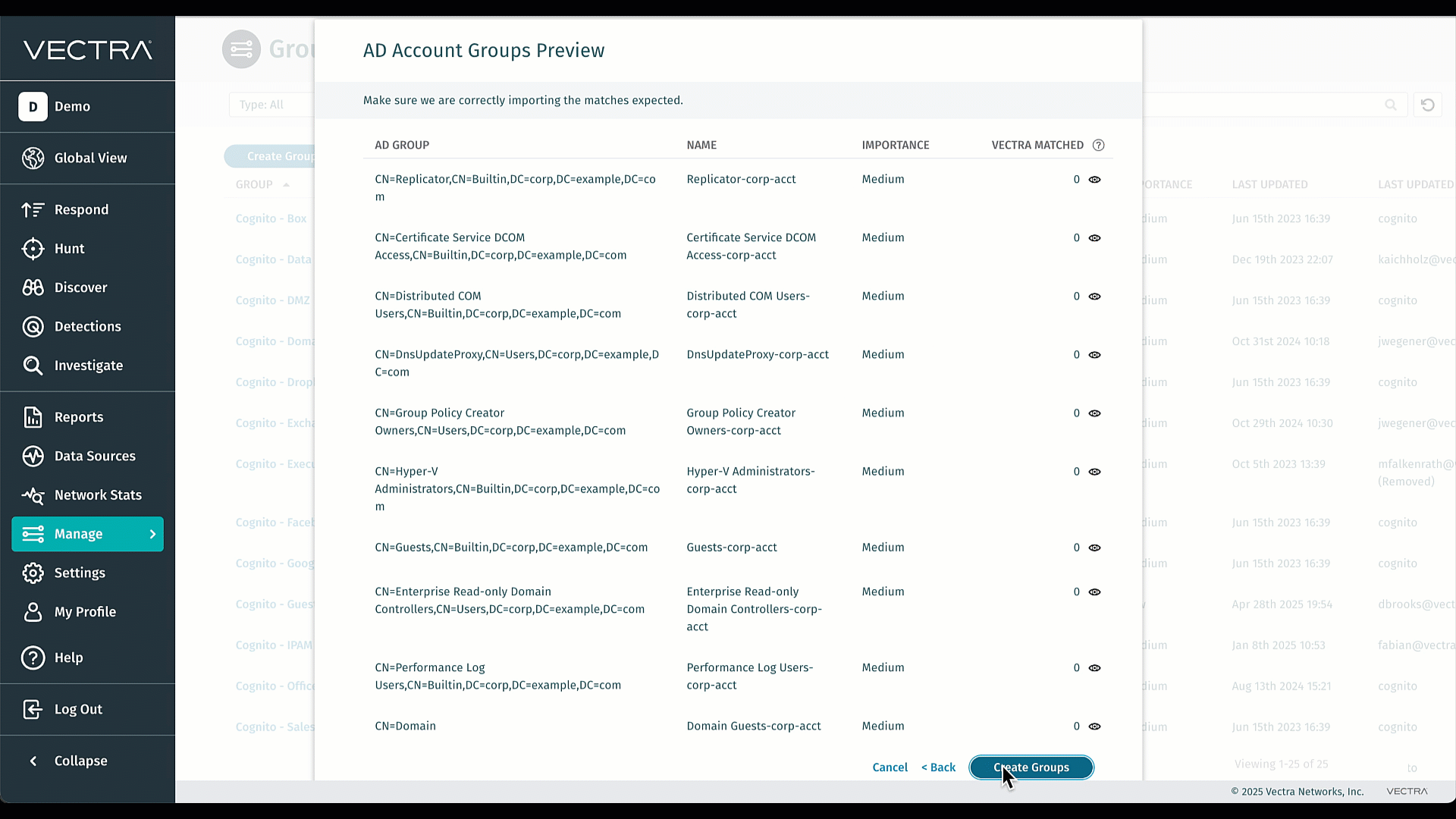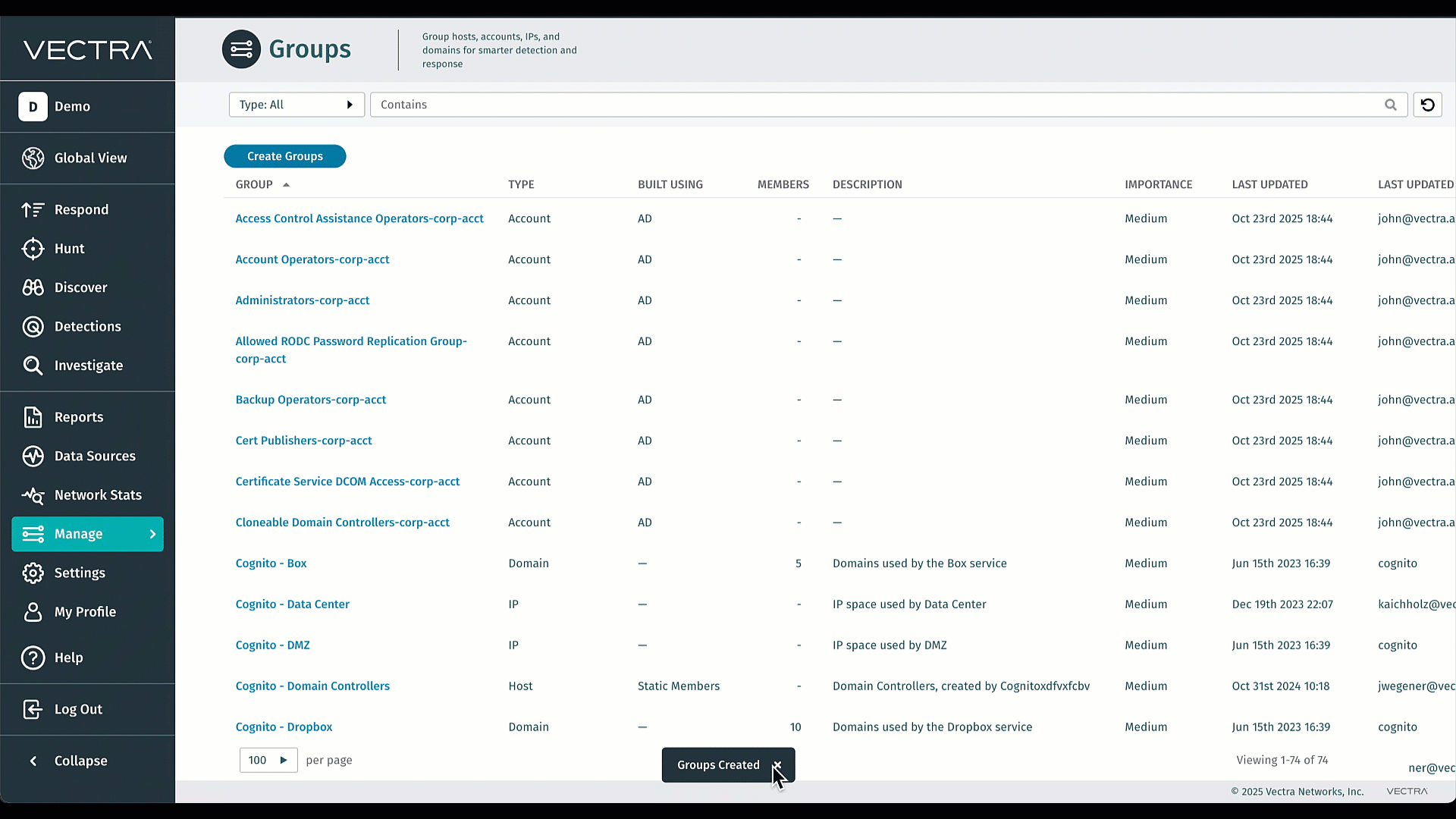
KI-Bewertungs-Priorisierungsagent
Der AI Prioritization Agent erkennt jetzt, wenn Angreifer neue Systeme einsetzen - von bösartigen Laptops bis hin zu Raspberry Pis - und berücksichtigt dies bei der Bewertung der Bedrohungen.
Es lernt auch aus historischen Trends, um wichtige seltene Erkennungstypen in Ihrer Umgebung zu markieren, was eine schnellere und genauere Priorisierung mit weniger Störungen ermöglicht.
Der Kunde sieht möglicherweise eine kleine Anzahl von Hosts mit aktualisierten Punktzahlen. Weitere Informationen finden Sie in diesem Podcast: https://youtu.be/DvsvR57xCS8
Architektur/Verwaltung
HTTPS-only-Zugriff für iDRAC und Embryo-Statusseite
Im Rahmen unseres kontinuierlichen Engagements für die Plattformsicherheit deaktiviert Version 9.7 den Zugriff über Port 80 (HTTP) sowohl für die iDRAC-Out-of-Band-Verwaltungsschnittstelle als auch für die Embryo-Statusseite (die während der Entschlüsselung und Bereitstellung vor VHE verwendet wird).
Mit diesem Update sind diese Komponenten nun ausschließlich über HTTPS (Port 443) zugänglich, wodurch das Risiko unverschlüsselten HTTP-Datenverkehrs ausgeschlossen wird. Kunden sehen nun keinen offenen Port 80 mehr auf Vectra-Geräten, wodurch sichergestellt ist, dass die gesamte Kommunikation standardmäßig verschlüsselt ist.
Diese Änderung erfordert keine Maßnahmen seitens der Benutzer und sorgt dafür, dass alle Systeme den aktuellen Sicherheitsbestimmungen entsprechen.
REST-API v2.5 (Quadrant UX)
Das Vectra AI aktualisiert die QUX-API weiterhin jeden Monat mit neuen Funktionen. Um über die neuesten Funktionen auf dem Laufenden zu bleiben, besuchen Sie das REST API v2.5 Changelog.
Datum:
November 2025
Freigabe:
2025.11
RUX: SaaS-Bereitstellung
Abdeckung
Verbesserungen für eine schnelle Freigabe
Die folgenden Verbesserungen wurden seit dem letzten Software-Release-Zyklus an den Algorithmen vorgenommen. Kunden, die mit dem Update-Service von Vectra verbunden sind und den Remote-Support aktiviert haben, haben diese Verbesserungen erhalten. Alle anderen Kunden erhalten die folgenden Verbesserungen als Teil dieser Version:
- Vectra AI mehrere Cobalt Strike als native Python-Erkennungen neu. Durch die Verlagerung dieser Erkennungen in die Python-basierte Engine von Vectra profitieren nun alle Kunden von dieser Cobalt Strike , ohne sich auf signaturbasierte Logik verlassen zu müssen.
- Vectra AI seine Kali Repo Usage-Erkennung verfeinert, um die Genauigkeit zu verbessern und Fehlalarme zu reduzieren, indem die Identifizierung von Kali-bezogenen User Agents verschärft wurde. Diese Verbesserung konzentriert die Übereinstimmungskriterien auf echte Kali Linux-Aktivitäten und gewährleistet so zuverlässigere Warnmeldungen und zuverlässigere Erkenntnisse bei der Untersuchung potenzieller Angreifer-Tools.
- Vectra AI neue Erkennungsfunktionen auf Informationsebene für Remote Management and Monitoring (RMM)-Tools eingeführt, die in Kundenumgebungen beobachtet werden. Da RMM-Dienstprogramme zunehmend bei Cyberangriffen eingesetzt werden, bieten diese Warnmeldungen Einblick in ihre Verwendung, ohne Störungen zu verursachen oder die Bewertung zu beeinflussen. Die Benachrichtigungen werden auf einzelnen Host-Seiten angezeigt – eine pro Host-Sitzung – und bleiben auf der Hauptseite „Erkennungen“ verborgen, sofern keine Filter angepasst werden. Dieses Update bietet Kunden einen klareren Einblick in potenziell sensible Verwaltungsaktivitäten und sorgt gleichzeitig für eine Warnmeldung mit geringen Auswirkungen.
Klarheit
Traffic Lockdown: Automatisierte Netzwerkverteidigung durch Firewall-Integration (öffentliche Vorschau)
Mit Traffic Lockdown, einer neuen Funktion, die bösartige Hosts automatisch auf Firewall-Ebene blockiert, ermöglicht Vectra AI seinen Kunden Vectra AI , sofort auf erkannte Bedrohungen zu reagieren. Durch die direkte Integration in unterstützte Firewalls veröffentlicht Vectra AI IP-Adressen aus dem Bedrohungsfeed, die sofort umgesetzt werden können, ohne dass manuelle Regeln oder komplexe Einstellungen erforderlich sind. Sicherheitsteams profitieren von einer schnelleren Eindämmung, übersichtlicheren Arbeitsabläufen und einem stärkeren Schutz dort, wo es am wichtigsten ist: am Netzwerkrand. Konfigurationsanweisungen finden Sie unter Traffic Lockdown.
_compressed.gif)
Kontrolle
Traffic Lockdown: Automatisierte Netzwerkverteidigung durch Firewall-Integration (öffentliche Vorschau)
Vectra AI können Kunden Vectra AI sofort auf erkannte Bedrohungen reagieren – dank Traffic Lockdown, einer neuen Funktion, die bösartige Hosts automatisch auf Firewall-Ebene blockiert. Durch die direkte Integration in unterstützte Firewalls veröffentlicht Vectra AI dynamisch IP-Adressen aus dem Threat Feed, die sofort umgesetzt werden können, ohne dass manuelle Regeln oder komplexe Einstellungen erforderlich sind. Sicherheitsteams profitieren von einer schnelleren Eindämmung, übersichtlicheren Arbeitsabläufen und einem stärkeren Schutz dort, wo es am wichtigsten ist: am Netzwerkrand. Konfigurationsanweisungen finden Sie unterTraffic Lockdown.
Betriebsübersichtsbericht
Wir stellen Ihnen den Betriebsübersichtsbericht vor – die neue Kommandoansicht Ihres SOC für Leistung und Wirkung. Dieser Bericht fasst wichtige Kennzahlen wie die durchschnittliche Zeit bis zur Zuweisung, die durchschnittliche Zeit bis zur Untersuchung und die durchschnittliche Zeit bis zur Lösung zusammen mit den wichtigsten Erkennungen, MITRE ATT&CK und priorisierten Entitäten in einem übersichtlichen, visuellen Dashboard zusammen. Er quantifiziert, wie Vectra AI schnellere Untersuchungen, eine präzisere Triage und messbare Effizienzsteigerungen ermöglicht. Mit aussagekräftigen Erkenntnissen für Geschäftsberichte, Führungskräfteberichte und den täglichen Betrieb verwandelt er Leistungsdaten in einen Wertnachweis.
Architektur/Verwaltung
Navigationsänderung: Konfiguration
Wir haben die Verwaltung Ihrer Umgebung in der Vectra AI optimiert. Die neueRegisterkarte „Konfiguration“vereint die Optionen „Verwalten“ und „Einstellungen“, sodass alle Konfigurations- und Steuerungseinstellungen in einer übersichtlichen, intuitiven Ansicht zusammengefasst sind. So finden Sie schneller, was Sie suchen, und können sicher handeln. Dieses Update beseitigt Reibungsverluste und vereinfacht die Navigation. Weniger suchen. Mehr tun.
Multi-SAML-Unterstützung
Die Respond UX-Plattform unterstützt derzeit Single Sign-On (SSO) durch die Integration mit dem Identitätsanbieter (IDP) eines Kunden unter Verwendung eines konfigurierten SAML-Profils. Bislang kann nur ein einziges SAML-Profil definiert werden, wodurch die Integration auf jeweils einen IDP beschränkt ist.
Um dieses Problem zu lösen, führen wir die Unterstützung für mehrere SAML-Profile ein. Diese Verbesserung ermöglicht es Kunden und MSSPs, Integrationen mit mehreren IDPs gleichzeitig zu konfigurieren und zu verwalten, was eine größere Flexibilität und eine bessere Anpassung an komplexe Identitätsumgebungen bietet.
Unterstützung für den Zugang zu RUX-Mietern
Wir haben die Möglichkeit eingeführt, dass autorisierte Mitarbeiter Vectra AIbei Bedarf sicher auf die Benutzeroberflächen von RUX-Mandanten zugreifen können. Kunden können nun ein Ablaufdatum für diesen Zugriff konfigurieren, um sicherzustellen, dass er zeitlich begrenzt bleibt und vollständig unter Ihrer Kontrolle steht.

REST-API (Respond UX)
Das Vectra AI aktualisiert die RUX-API weiterhin jeden Monat mit neuen Funktionen. Um über die neuesten Funktionen auf dem Laufenden zu bleiben, besuchen Sie unsere API-Dokumentationsseite.
Datum:
November 2025
Freigabe:
9.6
QUX: Appliance-Schnittstelle
Abdeckung
Netskope SASE-Integration in der öffentlichen Vorschau
Da sich Benutzer und Anwendungen über die Unternehmensgrenzen hinaus bewegen, verlieren Verteidiger den Überblick über kritischen Datenverkehr, der direkt in die cloud fließt. So entstehen blinde Flecken, in denen sich fortschrittliche Command-and-Control (C2) und Datenexfiltration verstecken können - und Unternehmen sind ungeschützt.
Die neue Integration von Vectra AImit Netskope CloudTAP schließt diese Lücke. Durch den Empfang des GENEVE-Verkehrs vom Netskope Stitcher bietet Vectra dieselbe tiefgreifende Bedrohungserkennung und Metadatentransparenz für Remote- und cloud Benutzer wie für On-Premise-Benutzer - wodurch blinde Flecken in modernen SASE-Umgebungen beseitigt werden.
Bitte wenden Sie sich an Ihr Vectra-Kundenteam, wenn Sie an der Netskope-Integration von Vectra interessiert sind. Siehe Netskope SASE-Integration und -Optimierung für Details zur Implementierung.
Verbesserungen für eine schnelle Freigabe
Die folgenden Verbesserungen wurden seit dem letzten Software-Release-Zyklus an den Algorithmen vorgenommen. Kunden, die mit dem Update-Service von Vectra verbunden sind und den Remote-Support aktiviert haben, haben diese Verbesserungen erhalten. Alle anderen Kunden erhalten die folgenden Verbesserungen als Teil dieser Version:
- Vectra AI erkennt jetzt LDAP-Abfragen, die auf Active Directory-Konten abzielen, denen die Kerberos-Vorauthentifizierung fehlt - ein häufiger Schritt bei AS-REP-Röstangriffen. Diese Verbesserung bietet einen früheren Einblick in die Erkundung von Anmeldeinformationen und hilft Sicherheitsteams, Angreifer zu stoppen, bevor der Missbrauch von Anmeldeinformationen beginnt.
- Vectra AI hat seine Erkennungslogik für RDP Brute-Force- und Passwort-Spray-Aktivitäten verfeinert, um die Genauigkeit zu verbessern und Fehlalarme in Umgebungen mit gemeinsam genutzten oder Bastion-Hosts zu reduzieren. Die Verbesserung verdeutlicht die Erkennungsschwellenwerte und -beschreibungen und stellt sicher, dass Kunden bei der Untersuchung von potenziellem Brute-Force-Verhalten präzisere Warnungen und mehr umsetzbare Erkenntnisse erhalten.
- Vectra AI hat die LDAP-Analyse verbessert, um die Auskundschaftung von AD-Benutzern mit Service Principal Names (SPNs) zu identifizieren - ein Vorläufer des Kerberoasting. Dieses Update ermöglicht eine schnellere Erkennung von Angriffen, die auf Anmeldeinformationen abzielen, und gibt Kunden einen besseren Einblick in heimliche Active Directory-Bedrohungen.
Klarheit
JA4T/JA4TS Fingerabdrücke: Recall und Stream
Vectra AI enthält jetzt JA4T- (TCP-Client) und JA4TS- (TCP-Server) Fingerabdrücke in den Metadaten und ermöglicht damit die Analyse des verschlüsselten Datenverkehrs mit Fingerabdrücken der nächsten Generation. Dieses leistungsstarke Framework reduziert Kollisionen, verknüpft verwandte Sitzungen und erleichtert die Erkennung von Angreifer-Infrastrukturen, die sich hinter gängigen Protokollen verstecken. Analysten erhalten klarere und schnellere Einblicke mit weniger Rauschen und besserem Kontext bei den Erkennungen. JA4T/JA4TS-Fingerprints werden jetzt in Stream und Recall unterstützt. Im Laufe des Jahres wird JA4T/JA4TS in Advanced Investigate (RUX) hinzugefügt. Lesen Sie hier mehr über die neuen Attribute.
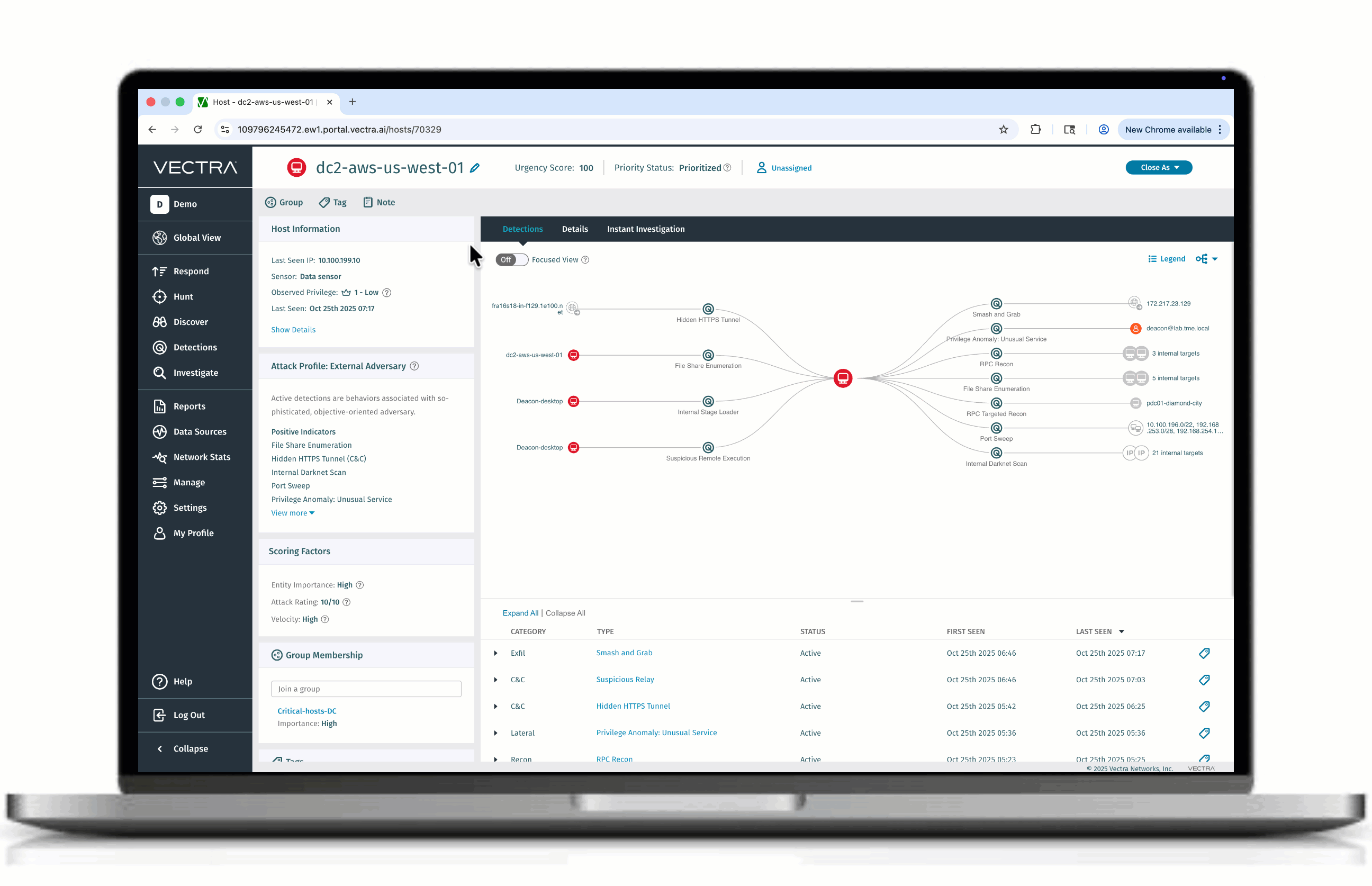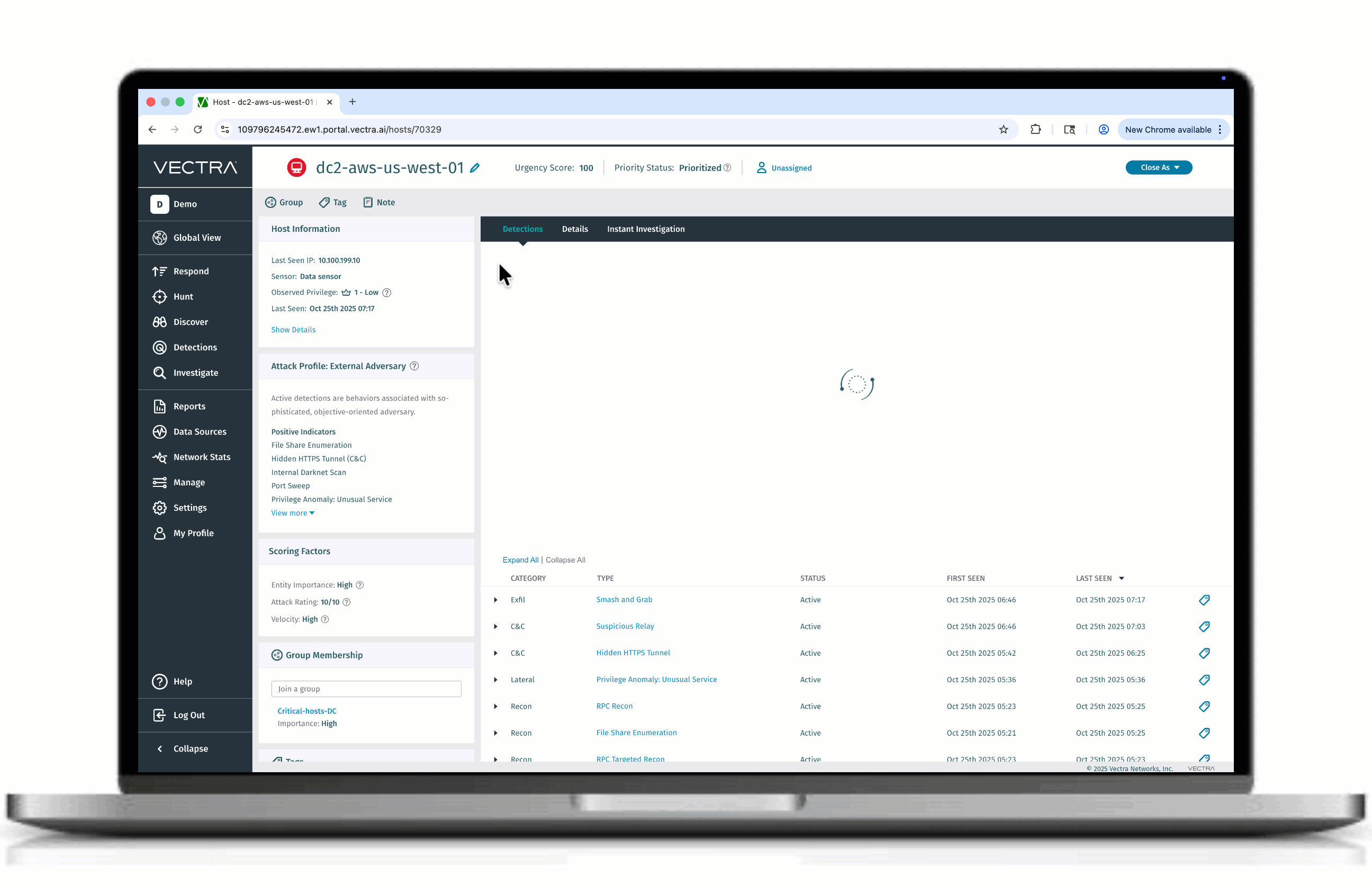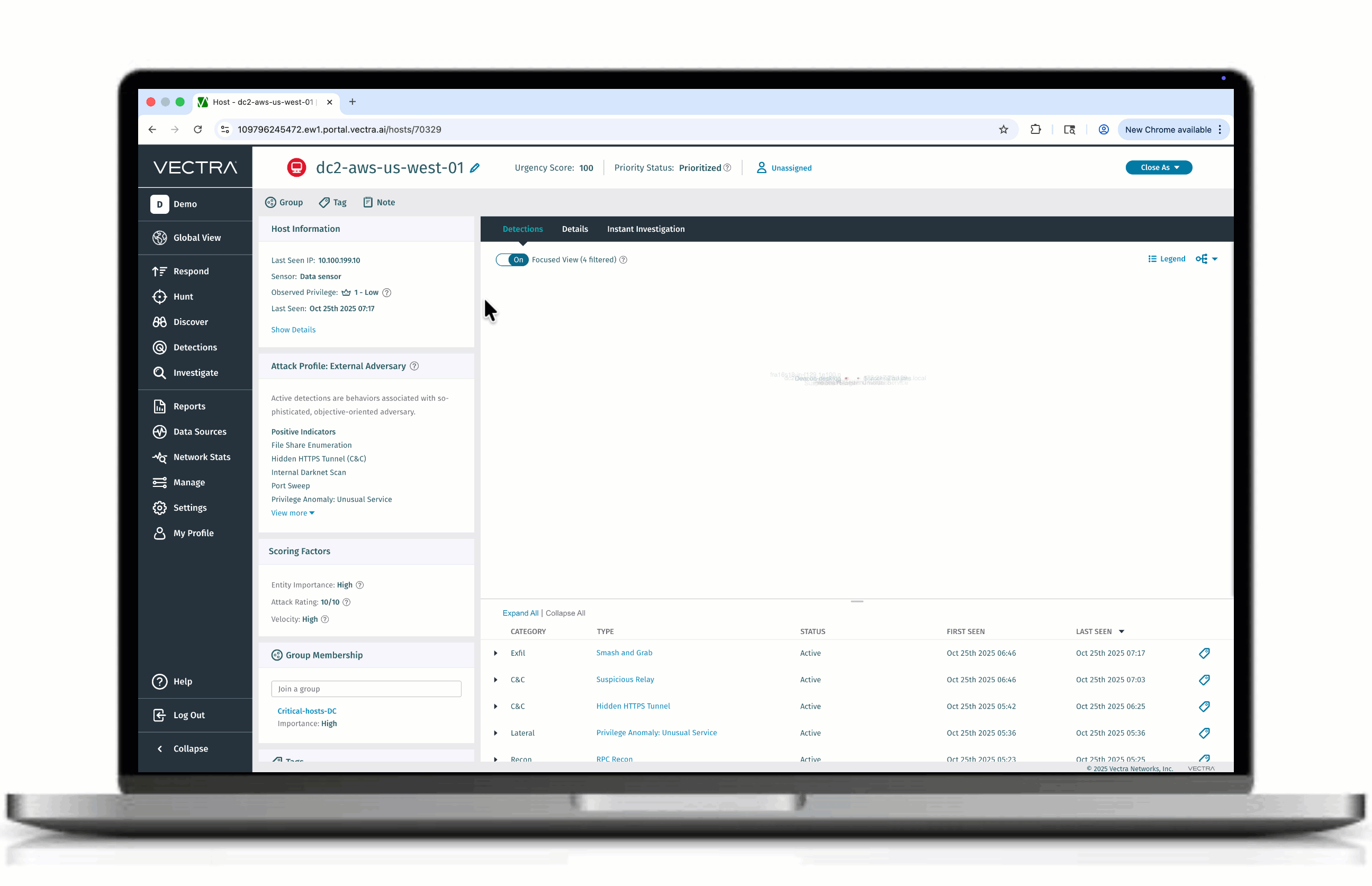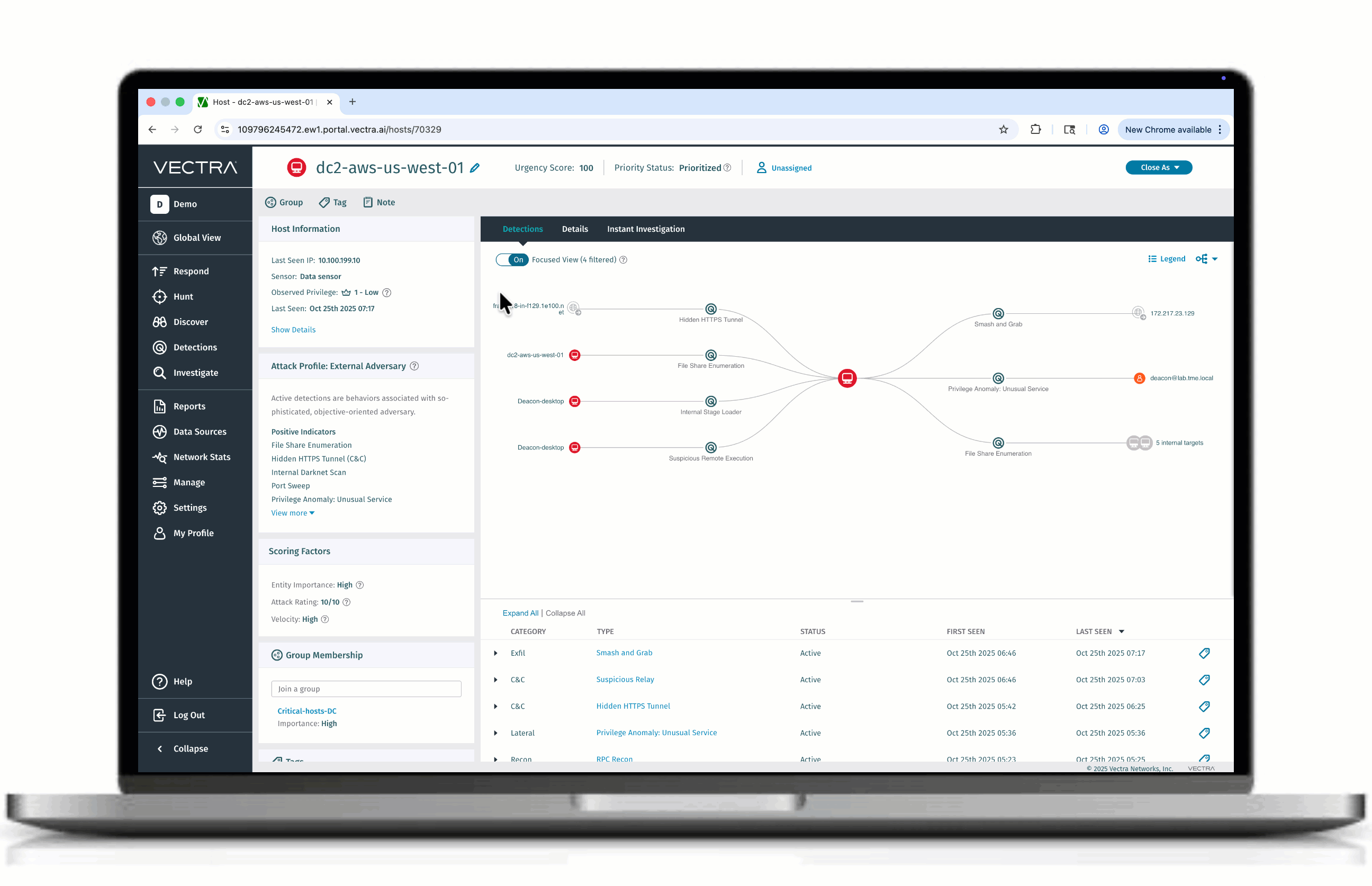
Angriffsdiagramm: Fokussierte Ansicht
Focused View ist eine neue Methode, um das Rauschen in komplexen Angriffsgraphen zu durchbrechen. Anstatt Analysten mit jedem Knoten und jeder Kante zu überfordern, filtert Focused View Erkennungen mit niedriger Priorität heraus und zeigt nur die kritischsten Verbindungen und Verlaufspfade an. Das Ergebnis: weniger Durcheinander, weniger Verwirrung und eine klare Perspektive auf die Entwicklung eines Angriffs. Mit Klarheit statt Unübersichtlichkeit können Sicherheitsteams ihre Untersuchungen beschleunigen, während sie bei Bedarf immer noch zum vollständigen Diagramm wechseln können.
Architektur/Verwaltung
Einführung des Vectra Virtual Brain für Nutanix
Vectra bietet jetzt eine vollständig virtualisierte Brain-Appliance für Nutanix-Umgebungen an. Diese virtuelle Brain-Appliance ist mit einem Durchsatz von 10 Gbit/s erhältlich und bietet die gleichen fortschrittlichen Funktionen wie physische Appliances - optimiert für Skalierbarkeit, schnelle Bereitstellung und betriebliche Effizienz. Detaillierte Spezifikationen und unterstützte Konfigurationen finden Sie im Handbuch Appliance- und Sensorspezifikationen. Anweisungen zur Bereitstellung finden Sie im Nutanix Deployment Guide.
Erhöhte Sicherheit: Nur HTTPS-Zugang zur Vectra-Benutzeroberfläche
Um die Sicherheit der Plattform zu erhöhen, blockiert die Vectra-Benutzeroberfläche nun den externen Zugriff über Port 80 (HTTP), anstatt wie bisher automatisch auf Port 443 (HTTPS) umzuleiten. Mit diesem Update ist die Vectra-Benutzeroberfläche nun ausschließlich über HTTPS zugänglich, was die Sicherheit der Plattform weiter erhöht und sicherstellt, dass alle Verbindungen standardmäßig verschlüsselt sind. Dieses Update gilt nur für Vectra Brain und erfordert keine Maßnahmen seitens der Benutzer. Es sorgt dafür, dass Ihre Umgebung den modernen Best Practices für Sicherheit entspricht.
Datum:
Oktober 2025
Freigabe:
9.5
QUX: Appliance-Schnittstelle
Abdeckung
Sliver Command and Control Abdeckung
Vectra AI hat eine neue Erkennungsfunktion für Sliver Command & Control (C2)-Aktivitäten eingeführt. Dabei handelt es sich um ein fortschrittliches Framework, das von Red Teams und Bedrohungsakteuren verwendet wird, um herkömmliche Abwehrmaßnahmen zu umgehen. Sliver nutzt Verschlüsselung, mehrschichtige Kodierer und variable Zeit- und Datenmuster, um böswilliges Beaconing im normalen verschlüsselten Datenverkehr zu verschleiern. Das Deep-Learning-Modell von Vectra identifiziert diese subtilen Muster, ohne sich auf die Inspektion der Nutzdaten zu verlassen, und nutzt dabei den branchenweit größten Datensatz zum Netzwerkverhalten. Dieses Update verbessert unsere aktuellen Beaconing-C2-Algorithmen, die einen besseren Einblick in ausweichende C2-Kanäle bieten und Sicherheitsteams dabei helfen, ausgeklügelte Aktivitäten von Angreifern früher in der Angriffskette zu erkennen.
Neue Erkennung: Azure Suspect VM Logging Änderung
Vectra AI hat eine neue Erkennung eingeführt, die verdächtige Verhaltensweisen im Zusammenhang mit der Änderung von Protokollierungserweiterungen für Windows- und Linux-VMs, Virtual Machine Scale Sets und Hybrid-Maschinen aufzeigt. Dies bietet einen tieferen Einblick in verdächtige Aktivitäten, die auf Versuche hindeuten, die Sicherheitsüberwachung zu manipulieren (verschlechterte gegenüber vollständig deaktivierten Protokollen).
Verbesserung der Erkennung: Azure Cryptomining
Die Azure Cryptomining-Erkennung wurde verbessert, um Verhaltensweisen herauszufiltern, die mit der Änderung bestehender Recheninstanzen zusammenhängen. Durch diese Verbesserung wird die Zuverlässigkeit der Warnmeldungen bei der Erstellung neuer Recheninstanzen verbessert. Kunden sollten mit weniger Alarmen rechnen, die mit diesem Verhalten in ihrer Umgebung verbunden sind.
M365 Erkennungsverbesserungen
Bei den folgenden Erkennungen wurden Verbesserungen vorgenommen, um den Erfassungsbereich zu erweitern:
- M365 Suspicious mailbox Rule Creation und M365 Suspicious Mail Forwarding: Diese Erkennungen wurden erweitert, um Verhaltensweisen im Zusammenhang mit UpdateInboxRule abzudecken. Infolge dieser Verbesserung können Kunden einen leichten Anstieg der mit diesen Alarmen verbundenen Volumina beobachten.
Verbesserungen für eine schnelle Freigabe
Die folgenden Verbesserungen wurden seit dem letzten Software-Release-Zyklus an den Algorithmen vorgenommen. Kunden, die mit dem Update-Service von Vectra verbunden sind und den Remote-Support aktiviert haben, haben diese Verbesserungen erhalten. Alle anderen Kunden erhalten die folgenden Verbesserungen als Teil dieser Version:
- NDR-242: Vectra AI hat seine aktuellen Command & Control für Beaconing erweitert, um fortschrittliche C2-Beaconing-Techniken zu erkennen, die Daten- und Zeitjitter nutzen, um die herkömmliche Netzwerküberwachung zu umgehen. Das Ergebnis ist ein besserer Einblick in das verdeckte C2-Verhalten und eine frühere Erkennung von hochentwickelten Bedrohungen, die versuchen, sich in der normalen Netzwerkaktivität zu verstecken.
- NDR-302: Vectra AI hat die Erkennungsabdeckung für Klartext-TCP-Kommunikation verbessert und identifiziert verdächtige Befehlsaktivitäten, die sich im unverschlüsselten, textbasierten Datenverkehr verbergen. Dieses Update erkennt subtile Verhaltensmuster, wie z. B. einen anormalen Paketfluss und eine anormale Nutzdatenstruktur, um verdeckte Befehlskanäle aufzudecken, die sich einer herkömmlichen Prüfung entziehen. Es erweitert die Sichtbarkeit über verschlüsselten Datenverkehr hinaus und verbessert die Erkennung bei allen Kommunikationstypen.
- NDR-314: Vectra AI hat die Abdeckung um den englischen HTTP-Kanal von Sliver erweitert, der den Befehls- und Kontrollverkehr als Zeichenketten mit zufälligen englischen Wörtern tarnt, um legitim zu erscheinen. Diese Erweiterung verbessert die Erkennung von verschleierten Sliver-Aktivitäten innerhalb des normalen HTTP-Verkehrs und erhöht den Einblick in fortschrittliche C2-Umgehungstechniken.
Klarheit
Geringeres Alarmaufkommen mit verbesserter AI-Triage
Die KI-Triage von Vectra bietet jetzt erweiterte Funktionen für die gesamte Kill Chain und moderne Netzwerke und reduziert das Erkennungsvolumen erheblich. Es untersucht und behebt automatisch gutartige Alarme und verringert so die Ermüdung durch Alarme, während gleichzeitig der volle Einblick in echte Bedrohungen erhalten bleibt.
Diese benutzerdefinierte, rigoros getestete Funktion identifiziert Muster mit geringem Risiko, die in Ihrer Umgebung immer wieder auftreten, und löst sie automatisch auf, damit sich Ihr Team auf die wesentlichen Risiken konzentrieren kann.
Erwarten Sie weniger gutartige Erkennungen im Netzwerk C2, Recon, Azure AD, M365, Copilot für M365 und AWS.
Die Sichtbarkeit geht nie verloren - gelöste Erkennungen bleiben durchsuchbar, überprüfbar und vollständig nachvollziehbar. Nach der Lösung werden keine weiteren Maßnahmen in Ihrem Namen ergriffen.
Demnächst verfügbar: Erweiterter EDR-Prozess-Kontext
Im November wird Vectra das Vectra AI Stitching mit CrowdStrike EDR für alle Kunden freigeben. Diese Funktion rationalisiert Untersuchungen, indem sie automatisch den wahrscheinlichen Prozess im Zusammenhang mit einer NDR-Erkennung findet und ihn neben der Erkennung in der Plattform und bei der Erfassung des Ereignisses über die API präsentiert.
Das Ergebnis ist ein leistungsfähigerer NDR, weniger manuelle Arbeit und bessere Ergebnisse für Sicherheitsteams. Was war der Prozess, der C2 einen Browser oder ein PowerShell-Skript antreibt, wird er erwartet oder fällt er auf - das sind Fragen, die Analysten sofort beantworten müssen, und diese Funktion macht das sofort möglich.
Um eine reibungslose Bereitstellung dieser Funktion zu gewährleisten, empfehlen wir allen Crowdstrike-Kunden, NGSIEM Lese- und Schreibrechte zu erteilen, um die zukünftige Erfassung dieser Informationen zu unterstützen. Besuchen Sie die FAQ zur Crowdstrike EDR-Integration, um zu erfahren, wie Sie diese Berechtigungen erteilen können.
Kontrolle
Angriffsgrafik-Verbesserungen
Der Attack Graph von Vectra AIAI wurde durch zwei leistungsstarke Updates noch intelligenter. C2 Blast Radius zeigt sofort alle Hosts an, die mit demselben endpoint kommunizieren, was manuelle Querverweise überflüssig macht und die Triage beschleunigt. Gezielte Erkennungen verfolgen den Ausgangspunkt der Kompromittierung und die Bewegung des Angreifers und geben Analysten einen klaren Überblick darüber, wie jeder Host oder jedes Konto erreicht wurde. Zusammen sorgen diese Verbesserungen für mehr Transparenz, schnellere Untersuchungen und präzisere Reaktionen. Weitere Funktionen finden Sie in den FAQ zu Attack Graph.
Architektur / Verwaltung
SHA256-Dateiüberprüfung für das Support-Portal
Alle aktuellen und zukünftigen Dateien in Zusätzliche Ressourcen > Downloads auf unserem Support-Portal enthalten jetzt einen SHA256-Hash, um zu überprüfen, ob die heruntergeladene Datei mit der vom Support-Portal bereitgestellten Datei übereinstimmt. Heute gilt dies für den Download von OVA- und Vectra Match .
Erweiterte TLS/SSL-Cipher-Erkennung
Vectra AI hat seine TLS/SSL-Cipher-Suite-Zuordnung um die neuesten TLS 1.3 und moderne Cipher-Suites erweitert, um sicherzustellen, dass verschlüsselte Sitzungen genau identifiziert und mit eindeutigen, für Menschen lesbaren Namen angezeigt werden. Dieses Update verbessert die Sichtbarkeit und Genauigkeit bei der Analyse von verschlüsseltem Datenverkehr in Recall und Stream, wobei die Unterstützung von Advanced Investigations für eine zukünftige Version geplant ist.
Datum:
Oktober 2025
Freigabe:
2025.10
RUX: SaaS-Bereitstellung
Abdeckung
Verbesserungen für eine schnelle Freigabe
Die folgenden Verbesserungen wurden seit dem letzten Software-Release-Zyklus an den Algorithmen vorgenommen. Kunden, die mit dem Update-Service von Vectra verbunden sind und den Remote-Support aktiviert haben, haben diese Verbesserungen erhalten. Alle anderen Kunden erhalten die folgenden Verbesserungen als Teil dieser Version:
- Vectra AI erkennt jetzt LDAP-Abfragen, die auf Active Directory-Konten abzielen, denen die Kerberos-Vorauthentifizierung fehlt - ein häufiger Schritt bei AS-REP-Röstangriffen. Diese Verbesserung bietet einen früheren Einblick in die Erkundung von Anmeldeinformationen und hilft Sicherheitsteams, Angreifer zu stoppen, bevor der Missbrauch von Anmeldeinformationen beginnt.
- Vectra AI hat die Beschreibung seiner RDP Brute-Force- und Passwort-Spray-Erkennung aktualisiert, um sie besser an das Erkennungsverhalten anzupassen. Während die zugrundeliegende Logik unverändert bleibt, verdeutlicht die überarbeitete Beschreibung, wie Passwort-Spray-Aktivitäten in der Benutzeroberfläche dargestellt werden, was Analysten hilft, Alarme präziser zu interpretieren.
- Vectra AI die LDAP-Analyse verbessert, um die Erkundung von AD-Benutzern mit ServicePrincipalNames (SPNs) zu identifizieren – ein Vorläufer von Kerberoasting. Dieses Update ermöglicht eine schnellere Erkennung von Angriffen, die auf Anmeldedaten abzielen, und bietet Kunden einen besseren Einblick in versteckte Active Directory-Bedrohungen.
Klarheit
Einführung der AI-unterstützten Suche
Wir machen die threat hunting und Untersuchung threat hunting schneller und intelligenter. Mit der KI-gestützten Suche können Sie Fragen im Klartext stellen - in jeder gängigen Sprache - und erhalten sofort kontextreiche Antworten, visuelle Einblicke und Empfehlungen für die nächsten Schritte. Keine Abfragesyntax, kein Rätselraten - nur umsetzbare Informationen auf Knopfdruck. Erste Nutzer haben die Untersuchungszeit um bis zu drei Stunden pro Fall verkürzt und dabei Risiken aufgedeckt, die sie vielleicht übersehen hätten. Verfügbar ab sofort für RUX-Kunden mit mindestens 14 Tagen an Metadaten.
.gif)
AI-Priorisierungsagent
Der AI Prioritization Agent erkennt jetzt, wenn Angreifer neue Systeme einsetzen - von bösartigen Laptops bis hin zu Raspberry Pis - und berücksichtigt dies bei der Bewertung der Bedrohungen.
Es lernt auch aus historischen Trends, um wichtige seltene Erkennungstypen in Ihrer Umgebung zu markieren, was eine schnellere und genauere Priorisierung mit weniger Störungen ermöglicht.
Der Kunde kann eine kleine Anzahl von Hosts mit aktualisierten Ergebnissen sehen. Für weitere Informationen sehen Sie sich diesen Prodcast an. https://youtu.be/DvsvR57xCS8
Architektur & Verwaltung
Gruppen basierend auf Active Directory-Mitgliedschaft
Bringen Sie Ihre bestehenden AD-Gruppen nahtlos in Vectra ein und halten Sie sie perfekt synchron - keine manuelle Neuerstellung oder mühsame Pflege mehr. Durch den Massenimport entfällt die sich wiederholende Verwaltungsarbeit, sodass sich Ihre Teams auf die threat hunting und nicht auf die Gruppenverwaltung konzentrieren können. Durch die Straffung der Triage-Regeln und die Reduzierung des Rauschens können Sie schneller auf die wirklich wichtigen Alarme reagieren. Das ist Effizienz und Signalklarheit, direkt eingebaut. Besuchen Sie Active Directory (AD)-Gruppen für weitere Informationen.

Neue REST-API-Dokumentation ist verfügbar
Wir freuen uns, Ihnen das neue Vectra REST API-Dokumentationsportal vorstellen zu dürfen – Ihre zentrale Anlaufstelle, um Vectra-APIs schneller als je zuvor zu erstellen, zu testen und zu integrieren.
RAD ersetzt statische PDF-Dateien durch dynamische, stets aktuelle OpenAPI-Dokumentationen mit integriertem Client, mit dem Sie Anfragen direkt über Ihren Browser ausprobieren können.
Entwickler können nun Integrationen nahtlos erkunden, validieren und generieren – für eine schnellere Automatisierung, weniger Fehler und mehr Sicherheit in Ihrer Umgebung.
Ab API v3.5 werden alle Dokumentationen ausschließlich über das REST-API-Dokumentationsportal bereitgestellt: https://apidocs.vectra.ai
Datum:
September 2025
Freigabe:
2025.09
RUX: SaaS-Bereitstellung
Abdeckung
Sliver Command and Control Abdeckung
Vectra AI hat die Abdeckung um den englischen HTTP-Kanal von Sliver erweitert, der den Befehls- und Kontrollverkehr als Zeichenketten mit zufälligen englischen Wörtern tarnt, um legitim zu erscheinen. Diese Erweiterung verbessert die Erkennung von verschleierten Sliver-Aktivitäten innerhalb des normalen HTTP-Verkehrs und erhöht den Einblick in fortschrittliche C2-Umgehungstechniken.
Command and Control
Vectra AI hat die Erkennungsabdeckung für Klartext-TCP-Kommunikation verbessert und identifiziert verdächtige Befehlsaktivitäten, die sich im unverschlüsselten, textbasierten Datenverkehr verbergen. Dieses Update erkennt subtile Verhaltensmuster, wie z. B. einen anormalen Paketfluss und eine anormale Nutzdatenstruktur, um verdeckte Befehlskanäle aufzudecken, die sich einer herkömmlichen Prüfung entziehen. Es erweitert die Sichtbarkeit über verschlüsselten Datenverkehr hinaus und verbessert die Erkennung bei allen Kommunikationstypen.
Neue Erkennung: Azure Suspect VM Logging Änderung
Vectra AI hat eine neue Erkennung eingeführt, die verdächtige Verhaltensweisen im Zusammenhang mit der Änderung von Protokollierungserweiterungen für Windows- und Linux-VMs, Virtual Machine Scale Sets und Hybrid-Maschinen aufzeigt. Dies bietet einen tieferen Einblick in verdächtige Aktivitäten, die auf Versuche hindeuten, die Sicherheitsüberwachung zu manipulieren (verschlechterte gegenüber vollständig deaktivierten Protokollen).
Verbesserung der Erkennung: Azure Cryptomining
Die Azure Cryptomining-Erkennung wurde verbessert, um Verhaltensweisen herauszufiltern, die mit der Änderung bestehender Recheninstanzen zusammenhängen. Durch diese Verbesserung wird die Zuverlässigkeit der Warnmeldungen bei der Erstellung neuer Recheninstanzen verbessert. Kunden sollten mit weniger Alarmen rechnen, die mit diesem Verhalten in ihrer Umgebung verbunden sind.
Erweiterung der Ressourcenprotokollierung für das Speicherkonto (CDR für Azure)
Vectra AI nutzt jetzt Azure-Ressourcenprotokolle, die mit Speicherkonten verknüpft sind, um neue und zukünftige Erkennungsfälle zu unterstützen. Diese neuen Protokolle ermöglichen Vectra die Erkennung von Impakt- und Exfiltrationsverhalten, das in den letzten Stadien der cloud beobachtet wird. Alle neuen CDR for Azure-Konnektoren werden die Protokolle automatisch als Teil der Konnektoreinrichtung erhalten. Für bestehende CDR for Azure-Kunden müssen die automatischen Deployment-Skripte, die mit CDR for Azure verbunden sind, erneut ausgeführt werden. Die Vectra-Kundenteams werden Kontakt aufnehmen, um die Erweiterung der Protokollierung für bestehende Kunden zu erleichtern.
M365 Erkennungsverbesserungen
Bei den folgenden Erkennungen wurden Verbesserungen vorgenommen, um den Erfassungsbereich zu erweitern:
- Erstellung von Regeln für verdächtige Postfächer in M365 und Weiterleitung verdächtiger E-Mails in M365: Diese Erkennungsfunktionen wurden erweitert, sodass sie nun auch Verhaltensweisen im Zusammenhang mit UpdateInboxRule abdecken. Infolge dieser Erweiterung kann es zu einem leichten Anstieg der Anzahl dieser Warnmeldungen kommen.
Verbesserungen für eine schnelle Freigabe
Die folgenden Verbesserungen wurden seit dem letzten Software-Release-Zyklus an den Algorithmen vorgenommen. Kunden, die mit dem Update-Service von Vectra verbunden sind und den Remote-Support aktiviert haben, haben diese Verbesserungen erhalten. Alle anderen Kunden erhalten die folgenden Verbesserungen als Teil dieser Version:
- NDR-242: Vectra AI hat seine aktuellen Command & Control für Beaconing erweitert, um fortschrittliche C2-Beaconing-Techniken zu erkennen, die Daten- und Zeitjitter nutzen, um die herkömmliche Netzwerküberwachung zu umgehen. Das Ergebnis ist ein besserer Einblick in das verdeckte C2-Verhalten und eine frühere Erkennung von hochentwickelten Bedrohungen, die versuchen, sich in normalen Netzwerkaktivitäten zu verstecken.
- NDR-302: Vectra AI hat die Erkennungsabdeckung für Klartext-TCP-Kommunikation verbessert und identifiziert verdächtige Befehlsaktivitäten, die sich im unverschlüsselten, textbasierten Datenverkehr verbergen. Dieses Update erkennt subtile Verhaltensmuster, wie z. B. einen anormalen Paketfluss und eine anormale Nutzdatenstruktur, um verdeckte Befehlskanäle aufzudecken, die sich einer herkömmlichen Prüfung entziehen. Es erweitert die Sichtbarkeit über verschlüsselten Datenverkehr hinaus und verbessert die Erkennung bei allen Kommunikationstypen.
- NDR-314: Vectra AI hat die Abdeckung um den englischen HTTP-Kanal von Sliver erweitert, der den Befehls- und Kontrollverkehr als Zeichenketten mit zufälligen englischen Wörtern tarnt, um legitim zu erscheinen. Diese Erweiterung verbessert die Erkennung von verschleierten Sliver-Aktivitäten innerhalb des normalen HTTP-Verkehrs und erhöht den Einblick in fortschrittliche C2-Umgehungstechniken.
Klarheit
API-Verbesserungen für CDR für Azure Alerts
Vectra AI hat API-Erweiterungen eingeführt, um den CDR für Azure-Warnungen, die über API konsumiert werden, mit angereichertem, von Menschen lesbarem Kontext (Identitäts- und Anwendungs-ID-Namen) zu versehen. Diese unterstützen investigative Workflows, die die Zeit, die ein Analyst benötigt, um wichtigen Kontext zu sammeln, erheblich reduzieren. Zuvor waren diese angereicherten Werte nur in der Vectra-Plattform verfügbar. Die neuen Erweiterungen stellen sicher, dass diese Werte jetzt in API-zentrierten Workflows, die Kunden möglicherweise bereits einsetzen, vorhanden sind.
Geringeres Alarmaufkommen mit verbesserter AI-Triage
Die KI-Triage von Vectra bietet jetzt erweiterte Funktionen für die gesamte Kill Chain und moderne Netzwerke und reduziert das Erkennungsvolumen erheblich. Es untersucht und behebt automatisch gutartige Alarme und verringert so die Ermüdung durch Alarme, während gleichzeitig der volle Einblick in echte Bedrohungen erhalten bleibt.
Diese benutzerdefinierte, rigoros getestete Funktion identifiziert Muster mit geringem Risiko, die in Ihrer Umgebung immer wieder auftreten, und löst sie automatisch auf, damit sich Ihr Team auf die wesentlichen Risiken konzentrieren kann.
Erwarten Sie weniger gutartige Erkennungen im Netzwerk C2, Recon, Azure AD, M365, Copilot für M365 und AWS.
Die Sichtbarkeit geht nie verloren - gelöste Erkennungen bleiben durchsuchbar, überprüfbar und vollständig nachvollziehbar. Nach der Lösung werden keine weiteren Maßnahmen in Ihrem Namen ergriffen.
Angriffsdiagramm: Fokussierte Ansicht
Focused View ist eine neue Methode, um das Rauschen in komplexen Angriffsgraphen zu durchbrechen. Anstatt Analysten mit jedem Knoten und jeder Kante zu überfordern, filtert Focused View Erkennungen mit niedriger Priorität heraus und zeigt nur die kritischsten Verbindungen und Verlaufspfade an. Das Ergebnis: weniger Durcheinander, weniger Verwirrung und eine klare Perspektive auf die Entwicklung eines Angriffs. Mit Klarheit statt Unübersichtlichkeit können Sicherheitsteams ihre Untersuchungen beschleunigen, während sie bei Bedarf immer noch zum vollständigen Diagramm wechseln können.

Datum:
August 2025
Freigabe:
9.4
QUX: Appliance-Schnittstelle
JA4+ Fingerabdrücke
Vectra AI enthält jetzt JA4L-, JA4X- und JA4H-Fingerprints in den Metadaten und bietet damit die nächste Generation des Fingerprinting für die Analyse von verschlüsseltem Datenverkehr. Dieses leistungsstarke Framework reduziert Kollisionen, verknüpft verwandte Sitzungen und erleichtert die Erkennung von Angreiferinfrastrukturen, die sich hinter gängigen Protokollen verstecken. Analysten erhalten klarere und schnellere Einblicke mit weniger Rauschen und besserem Kontext bei den Erkennungen. JA4+ wird in Investigate (RUX), Stream und Recall unterstützt. Weitere Informationen über die neuen Attribute finden Sie hier.
Externe App-Benachrichtigungen (Webhook-Benachrichtigungen)
Mit External App Alerts liefert die Vectra AI sofortige Benachrichtigungen an die Collaboration-Tools Ihres Teams, wenn kritische Sicherheitsereignisse auftreten, z. B. Hosts oder Konten mit hoher Priorität und wichtige Systemwarnungen. Kein Zuschauen mehr auf dem Bildschirm oder verzögerte Antworten - Sie erhalten Echtzeitinformationen, die ein schnelleres Handeln ermöglichen. Verfügbar ab sofort mit direkter Microsoft Teams-Integration und Slack-Unterstützung in Kürze. Details zur Implementierung finden Sie unter External App Alerts.
Verwendung der Azure AD Scripting Engine
Vectra AI hat Verbesserungen eingeführt, um sowohl den Umfang der Verhaltensweisen als auch der von dieser Erkennung erfassten Benutzeragenten zu verbessern. Aktualisierungen der Parsing-Schicht filtern nun Benutzer-Agenten genauer aus den Protokollen, was die Genauigkeit erhöht und falsch-positive Ergebnisse reduziert.
UI-Verbesserungen bei Entra ID und M365-Erkennungen
Bei mehreren Erkennungen wurden Verbesserungen eingeführt, um zusätzlichen Kontext zu liefern und die Ermittlungsabläufe zu optimieren:
- AzureAD Privilege Operation Anomaly: Enthält jetzt Details zum Benutzer-Agenten, wenn verfügbar.
- Azure AD Suspicious Factor Registration: Aktualisiert, um das Feld result_reason aus den Protokollen einzubeziehen.
- Azure AD Suspicious Sign In: Aktualisiert, um den Gerätestatus für verbesserten Kontext anzuzeigen.
- M365 Spearphishing: Die Anzeige der Dateinamen wurde aktualisiert, um eine schnellere Auswertung zu ermöglichen.
Erweiterung des Azure Cloud Detection Model
Die Erweiterungen der Erkennung von deaktivierten Azure-Diagnoseprotokollen umfassen nun auch die Löschung von Protokollierungserweiterungen für Windows- und Linux-VMs. Dies bietet einen breiteren Einblick in verdächtige Aktivitäten, die auf Versuche zur Deaktivierung der Sicherheitsüberwachung hindeuten können.
Verbesserungen für eine schnelle Freigabe
Die folgenden Verbesserungen wurden seit dem letzten Software-Release-Zyklus an den Algorithmen vorgenommen. Kunden, die mit dem Update-Service von Vectra AIverbunden sind und den Remote-Support aktiviert haben, haben diese Verbesserungen erhalten. Alle anderen Kunden werden die folgenden Verbesserungen als Teil von 9.3 erhalten:
- NDR-251: Die Erkennung von verdächtigem Mimikatz-Zugriff über SMB-Datenverkehr wurde erweitert. Dies verbessert unsere Fähigkeit, potenzielle Techniken zum Diebstahl von Anmeldeinformationen zu erkennen, die häufig bei Angriffen verwendet werden.
- NDR-117: Erweitert die Abdeckung des Algorithmus für Admin-Aktivitäten des Remote Desktop Protocol (RDP) für eine bessere Sicherheitsabdeckung.
- NDR-241: Die Erkennung von Brute-Force-Angriffen auf die NTLM-Authentifizierung wurde erweitert, um Angreifer daran zu hindern, durch wiederholte Anmeldeversuche in Konten einzudringen.
Datum:
August 2025
Freigabe:
9.3
QUX: Appliance-Schnittstelle
Zscaler Internet Access SSE Integration in der öffentlichen Vorschau
Vectra AI und Zscaler haben sich zusammengetan, um blinde Flecken im verschlüsselten und cloud zu beseitigen. Durch die Integration mit Zscaler Internet Access (ZIA) gibt Vectra den Benutzerdatenverkehr von sicheren PCAPs wieder, um Bedrohungen aus dem gesamten Spektrum zu erkennen - und so fortgeschrittene C2 und Exfiltration aufzudecken, die herkömmliche Tools übersehen. Dies ist ein entscheidender Vorteil für die Sicherung von Remote- und cloud. Weitere Informationen finden Sie in der Pressemitteilung und im Podcast von Vectra AI. Bitte wenden Sie sich an Ihr Vectra AI , wenn Sie an der ZIA-Integration von Vectra interessiert sind. Einzelheiten zur Implementierung finden Sie unter Zscaler ZIA-Integration und -Optimierung.
Vectra Match Integrierte Regelsatzverwaltung
Vectra Match erleichtert jetzt die Erkennung bekannter Sicherheitsrisiken (Indicators of Compromise, IOCs) mit Suricata-kompatiblen Signaturen - externe Tools sind nicht erforderlich. Ab 9.3 können Sie Regeln direkt in der Plattform verwalten, ändern, aktivieren oder deaktivieren, und Ihre Änderungen bleiben auch nach Emerging Threats-Updates erhalten. Das beschleunigt die Einrichtung, vereinfacht die Wartung und gibt Ihnen die volle Kontrolle über die Erkennungslogik in die Hand. Weitere Informationen finden Sie unter Vectra AI Match Rulesets verwalten.
Übersichtsbericht der Exekutive
Vectra AI stellt den Executive Overview Report vor - eine Momentaufnahme der Sicherheit in der Vorstandsetage. Er wurde speziell für CISOs und Sicherheitsverantwortliche entwickelt und liefert klare, aussagekräftige Metriken wie Noise-to-Signal-Trends und sich entwickelnde Angriffsmuster. In wenigen Minuten erhalten Sie Einblicke, um die Wirkung von Vectra darzustellen, strategische Entscheidungen zu steuern und nachzuweisen, wie Sie das Risiko von Sicherheitsverletzungen reduzieren - ohne tiefere Einblicke.
Angriffsgrafiken Visualisierungen in Quadrant UX
Das neue Angriffsdiagramm schafft sofortige Klarheit über aktive Bedrohungen, indem es visuell darstellt, wie sich Angreifer durch Ihr Netzwerk, Ihre cloud und Ihre Identitätsumgebung bewegen. Dank der Vectra AI wird jetzt jede Bedrohung direkt auf der Host- oder Kontoseite angezeigt, sodass Sie sofort erkennen können, wo der Angriff begann, mit welchen Systemen er interagierte und wie sich sein Risikoniveau im Laufe der Zeit entwickelte.
Sicherheitsteams können aus drei intuitiven Ansichten wählen, um Bedrohungen auf die Weise zu untersuchen, die am besten zu ihrem Arbeitsablauf passt:
- Angriffsgrafik - Sehen Sie, wie verschiedene Entitäten während des Angriffs miteinander verbunden sind.
- Angriffsfluss - Sehen Sie die Abfolge der Angreiferaktionen in einem strukturierten Pfad.
- Zeitleiste des Angriffs - Sehen Sie, wie sich das Bedrohungsrisiko verändert hat und eskaliert ist.
Diese Funktion ermöglicht es SOC-Teams, schnell und sicher zu handeln, da Kontext und Dringlichkeit in einer einzigen, umsetzbaren Ansicht dargestellt werden. Weitere Informationen finden Sie in den FAQ zum Attack Graph.
JA4/JA4S Fingerabdrücke
Vectra AI enthält jetzt JA4- und JA4S-Fingerprints in den Metadaten und bietet damit Fingerprinting der nächsten Generation für die Analyse von verschlüsseltem Datenverkehr. Dieses leistungsstarke Framework reduziert Kollisionen, verknüpft verwandte Sitzungen und erleichtert die Erkennung von Angreifer-Infrastrukturen, die sich hinter gängigen Protokollen verstecken. Analysten erhalten klarere und schnellere Einblicke mit weniger Rauschen und besserem Kontext bei den Erkennungen. JA4 wird von Investigate (RUX), Stream und Recall unterstützt, und weitere Funktionen der JA4+ Suite werden in Kürze folgen. Weitere Informationen über die neuen Attribute finden Sie hier.
Validierung des Netzwerkverkehrs UI in Quadrant UX
Mit der Version 9.3 hat Vectra AI neue Seiten für die Verkehrsüberprüfung eingeführt. Diese Seiten verwandeln den JSON-Bericht zur Verkehrsüberprüfung in ein intuitives Dashboard, das Einblicke schneller und ohne mühsames Parsen von Rohdaten anzeigt. Die wichtigsten Statistiken werden automatisch anhand vordefinierter Schwellenwerte überprüft, wobei rote oder gelbe Indikatoren die Bereiche hervorheben, die möglicherweise Aufmerksamkeit erfordern. Für weitere Informationen lesen Sie die FAQ.
AI-Triage löst jetzt automatisch mehr gutartige Bedrohungen
Die proprietäre KI von Vectra AIist jetzt noch intelligenter. Unser aktualisierter AI-Triage-Algorithmus untersucht und löst jetzt automatisch 50 % der gutartigen C&C- und 25 % der gutartigen Recon-Erkennungen und reduziert damit die Anzahl der gutartigen Ereignisse drastisch. Er nutzt sowohl lokale Muster als auch globale Erkenntnisse, um das bisher deutlichste Signal zu liefern. Weitere Einzelheiten zu AI-Triage finden Sie in dem Artikel und dem Video zu AI-Triage.
Verbesserte Bedrohungseinstufung mit AI-Priorisierung
Die Vectra AI wurde verbessert, um Bedrohungen besser zu erkennen, die die jüngsten Veränderungen im Verhalten von Angreifern widerspiegeln. Erwarten Sie eine bessere Unterscheidung zwischen hohen und kritischen Bedrohungen, eine intelligentere Priorisierung in Ihrer Umgebung und eine schnellere Priorisierung von Bedrohungen. Beachten Sie, dass sich die Bedrohungs- und Sicherheitsbewertungen einiger Hosts und Konten aufgrund der aktualisierten Bewertungslogik ändern können, sobald Ihr System aktualisiert wird.
Bewährte Praktiken der Triage
Vectra AI führt eine neue Serie von Best Practices ein, die Anwendern helfen soll, die wichtigsten Funktionen der Vectra AI optimal zu nutzen. Die erste Veröffentlichung in dieser Reihe konzentriert sich auf Triage. Der Leitfaden zu den Best Practices für die Triage umfasst gängige Terminologie, wann und warum eine Triage durchgeführt werden sollte, Anleitungen, FAQs und vieles mehr. Besuchen Sie den Artikel Triage Best Practices, um Ihren Triage-Workflow zu optimieren.
VirusTotal Entfernung
Vectra AI hat die VirusTotal-Integration aufgrund von Lizenzierungsänderungen aus Quadrant UX entfernt. Das Popup-Fenster "Externes Ziel" zeigt keine VirusTotal-Daten mehr an, und die Benutzeroberfläche wird in der nächsten Version vollständig bereinigt, um Verwirrung zu vermeiden. Für Feedback oder Fragen zu dieser Entfernung wenden Sie sich bitte an Ihr Vectra AI .
Neue Detection Suite: AWS S3
Vectra AI hat drei neue Erkennungen eingeführt, um verdächtige Verhaltensweisen im Zusammenhang mit der Nutzung von AWS S3 in der Impact- und Exfil-Phase der cloud aufzudecken:
- AWS Verdächtige S3-Batch-Löschung: Diese Erkennung zeigt Verhaltensweisen im Zusammenhang mit groß angelegten Downloads und Löschungen mehrerer Dateien. Dieses Verhalten kann auf die destruktive Manipulationsphase der ransomware in der Umgebung hinweisen.
- AWS Verdächtige S3-Objekt-Löschung: Wie die neue S3-Batch-Löschungserkennung hebt diese Erkennung Verhaltensweisen hervor, bei denen einzelne Objekte heruntergeladen und dann aus einem S3-Bucket auf eine Weise gelöscht wurden, die auf die destruktive Manipulationsphase von ransomware in der Umgebung hinweisen kann.
- AWS Verdächtige S3-Verschlüsselung: Diese Erkennung hebt ungewöhnliche Verschlüsselungsaktivitäten hervor, die auf eine laufende ransomware hindeuten könnten. Sie wurde entwickelt, um die Verschlüsselung vieler S3-Objekte aufzudecken, die entweder einen externenKMS -Schlüssel (SSE-KMS) oder einen vom Client kontrollierten Schlüssel (SSE-C) verwenden.
Signalverbesserungen für M365, Azure AD und Azure
Für die folgenden AAD-, Microsoft 365- und Azure-Erkennungen wurden Verbesserungen eingeführt, um das Risiko der zugrunde liegenden Verhaltensweisen besser zu berücksichtigen und sie zeitnah zur Überprüfung anzuzeigen. Die Einführung dieser Verbesserungen kann zu Änderungen bei der Anzahl der Entitäten führen, die innerhalb der Vectra AI Platform priorisiert werden:
- M365 Verdächtige Power Automate-Aktivität: Diese Erkennung warnt vor potenziellem Exfiltrations- oder C2-Verhalten unter Verwendung von Power Automate in der Umgebung. Die an dieser Erkennung vorgenommenen Verbesserungen führen zu einer erheblichen Verbesserung der Zuverlässigkeit dieser Erkennung und zu einer Verringerung der Rate der bei dieser und ähnlichen Erkennungen (M365 Power Automate HTTP Flow Creation und M365 Suspicious Power Automate Flow Creation) beobachteten False Positives.
- Azure AD Privilege Operation Anomaly: Diese Erkennung warnt vor anomalen Azure AD-Vorgängen, die möglicherweise mit einer Privilegieneskalation verbunden sind. Vectra AI verbessert diese Erkennung, um die Verhaltensweisen, die als anomal gelten, zu schärfen. Das erwartete Ergebnis ist ein geringeres Rauschen bei dieser Erkennung.
- Riskante Exchange-Operation: Diese Erkennung warnt vor privilegierten Vorgängen in Exchange, die von einem Angreifer missbraucht werden könnten. Vectra AI erweitert den Umfang der Verhaltensweisen, die für diese Warnung in Frage kommen, und entfernt potenziell harmlose Aktionen in Exchange (z. B. das Einrichten automatischer Antworten). Kunden können aufgrund dieser Verbesserungen mit einer deutlichen Reduzierung des Volumens rechnen (über 30 %).
- Azure-Diagnoseprotokollierung Deaktiviert: Diese Erkennung deckt das Verhalten von Verteidigungsbeeinträchtigungen im Zusammenhang mit der Löschung von Azure-Diagnoseprotokolleinstellungen auf. Die Erkennung wurde verbessert, um eine breitere Abdeckung bei der Löschung von Diagnoseprotokollen auf virtuellen Maschinen (VMs) zu erreichen. Kunden werden möglicherweise einen geringfügigen Anstieg des Erkennungsvolumens in Verbindung mit dieser Verbesserung feststellen.
Verbesserungen für eine schnelle Freigabe
Die folgenden Verbesserungen wurden seit dem letzten Software-Release-Zyklus an den Algorithmen vorgenommen. Kunden, die mit dem Update-Service von Vectra AIverbunden sind und den Remote-Support aktiviert haben, haben diese Verbesserungen erhalten. Alle anderen Kunden werden die folgenden Verbesserungen als Teil von 9.3 erhalten:
- NDR-222: Aktualisiert den Titel der Erkennung verdächtiger Protokollaktivitäten bei verdächtiger Verwendung von Windows Remote Management (WinRM). Der neue Titel lautet "Mögliche bösartige WinRM-Nutzung", um die Art des Verhaltens besser wiederzugeben.
- CS-10426: Es wurde ein Problem behoben, das einige Erkennungen von Suspect Protocol Activity betraf, bei denen Quell- und Ziel-IP-Adressen falsch zugeordnet wurden, da der Client als Proxy fungierte. Diese Korrektur wurde auf alle relevanten Erkennungsalgorithmen angewendet.
- NDR-251: Erweitert die Erkennungsabdeckung gegen Penetrationstechniken, die vom Kali Linux Package Repository verwendet werden.
- NDR-251: Erweitert die Erkennung von Tor-Aktivitäten durch die Identifizierung von Ziel-IPs, die mit bekannten Tor-Knoten übereinstimmen.
Datum:
August 2025
Freigabe:
2025.08
RUX: SaaS-Bereitstellung
Stärkerer Kontext mit neuen Angriffsgraphen-Upgrades
VectraVectra AI hat den Attack Graph um zwei leistungsstarke neue Funktionen erweitert. Erstens können Analysten jetzt Erkennungen sehen, die direkt auf die zu untersuchende Entität abzielen, was die Beantwortung der Frage erleichtert: "Wie wurde diese Entität kompromittiert?" Auf diese Weise lässt sich der "Patient Zero" auch in komplexen Lateral Movement-Szenarien schnell ausfindig machen. Zweitens visualisiert das Angriffsdiagramm jetzt den Explosionsradius von Command-and-Control (C2)-Kanälen und zeigt automatisch alle Entitäten an, die mit derselben bösartigen Domain oder IP verbunden sind. Zusammengenommen beschleunigen diese Upgrades die Ermittlungen, decken versteckte Verbindungen auf und geben Teams einen vollständigen Kontext, um Angriffe schneller zu stoppen.
Beschleunigung der Ermittlungen mit Five Minute Hunts
Wirfreuen uns, Ihnen mitteilen zu können, dass Five Minute Hunts jetzt in Advanced Investigations verfügbar sind. Diese geführten Suchen liefern aussagekräftige Erkenntnisse in Metadaten, ohne dass Kunden SQL oder spezielle Terminologie beherrschen müssen. Sicherheitsteams können mit nur wenigen Klicks schnell Angreifermuster aufdecken, proaktiven "Peace-Time"-Wert demonstrieren und die Effizienz steigern. Hinter den Kulissen wird die Funktion von unserem flexiblen Content-Delivery-Framework unterstützt - komplett mit adaptiven Layouts, sanften Animationen und ansprechenden Grafiken für ein nahtloses Analystenerlebnis.
Externe App-Benachrichtigungen (Webhook-Benachrichtigungen)
Mit External App Alerts liefert Vectra AI sofortige Benachrichtigungen an die Kollaborationstools Ihres Teams, wenn kritische Sicherheitsereignisse auftreten, z. B. Hosts oder Konten mit hoher Priorität und wichtige Systemwarnungen. Kein Zuschauen mehr auf dem Bildschirm oder verzögerte Antworten - Sie erhalten Echtzeitinformationen, die ein schnelleres Handeln ermöglichen. Verfügbar ab sofort mit direkter Microsoft Teams-Integration und Slack-Unterstützung in Kürze. Details zur Implementierung finden Sie unter External App Alerts.

JA4+ Fingerabdrücke
VectraVectra AI enthält jetzt JA4-, JA4S-, JA4L-, JA4X- und JA4H-Fingerprints in den Metadaten und bietet damit Fingerprinting der nächsten Generation für die Analyse von verschlüsseltem Datenverkehr. Dieses leistungsstarke Framework reduziert Kollisionen, verknüpft verwandte Sitzungen und erleichtert die Erkennung von Angreifer-Infrastrukturen, die sich hinter gängigen Protokollen verstecken. Analysten erhalten klarere und schnellere Einblicke mit weniger Rauschen und besserem Kontext bei den Erkennungen. JA4+ wird in Investigate (RUX), Stream und Recall unterstützt. Lesen Sie hier mehr über die neuen Attribute.
Einfachere Ermittlungen mit von Menschen lesbaren Azure CDR-Daten
Vectra AI hat Azure CDR benutzerfreundlicher gemacht, indem verwirrende UUIDs durch klare, für Menschen lesbare Namen ersetzt wurden. Kontonamen in der REST-API spiegeln jetzt erkennbare Entra-IDs wider, während die Erkennungsaktivitäten intuitive Objekt- und Anwendungsnamen anzeigen. Analysten müssen keine rohen IDs mehr dekodieren, wodurch die Triage schneller, die Untersuchungen reibungsloser und die Dashboards aussagekräftiger werden.
Datum:
Juli 2025
Freigabe:
2025.07
RUX: SaaS-Bereitstellung
Gruppen basierend auf Active Directory-Mitgliedschaft
Bringen Sie Ihre bestehenden AD-Gruppen nahtlos in Vectra ein und halten Sie sie perfekt synchron - keine manuelle Neuerstellung oder mühsame Pflege mehr. Durch den Massenimport entfällt die sich wiederholende Verwaltungsarbeit, sodass sich Ihre Teams auf die threat hunting und nicht auf die Gruppenverwaltung konzentrieren können. Durch die Straffung der Triage-Regeln und die Reduzierung des Rauschens können Sie schneller auf die wirklich wichtigen Alarme reagieren. Das ist Effizienz und Signalklarheit, direkt eingebaut. Besuchen Sie Active Directory (AD)-Gruppen für weitere Informationen.
Zscaler Internet Access SSE Integration in der öffentlichen Vorschau
Vectra AI und Zscaler haben sich zusammengetan, um blinde Flecken im verschlüsselten und cloud zu beseitigen. Durch die Integration mit Zscaler Internet Access (ZIA) gibt Vectra den Benutzerdatenverkehr von sicheren PCAPs wieder, um Bedrohungen aus dem gesamten Spektrum zu erkennen - und so fortgeschrittene C2 und Exfiltration aufzudecken, die herkömmliche Tools übersehen. Dies ist ein entscheidender Vorteil für die Sicherung von Remote- und cloud. Weitere Informationen finden Sie in der Pressemitteilung und im Podcast von Vectra. Bitte wenden Sie sich an Ihr Vectra-Kundenteam, wenn Sie an der ZIA-Integration von Vectra interessiert sind. Einzelheiten zur Implementierung finden Sie unter Zscaler ZIA-Integration und -Optimierung.
Tieferer Einblick in die Geschäftsführung mit Signalwirkung in CISO-Berichten
Vectra AI bringt jetzt Metriken zur Signalwirksamkeit direkt in die CISO-Berichte ein und zeigt, wie Erkennungen und Entitäten als gutartig, behoben oder unklassifiziert eingestuft wurden. Dieser zusätzliche Kontext beweist den Wert von Erkennungen, die für Analysten am wichtigsten sind, und zeigt die Ergebnisse von Abhilfemaßnahmen auf einen Blick. Führungskräfte erhalten einen klaren Einblick in die Qualität der Bedrohungen, was zu intelligenteren Sicherheitsentscheidungen führt und den messbaren Nutzen von Vectra demonstriert.
Bessere Sichtbarkeit mit dem Network Discovery Dashboard
Vectra AI stellt das Network Discovery Dashboard vor, eine leistungsstarke neue Methode zur Erkundung Ihrer Umgebung mit einer interaktiven Netzwerkkarte. Analysten können nun Hosts und IPs visuell verfolgen, Anomalien im Kontext erkennen und Untersuchungen mit intuitiver Navigation beschleunigen. Dieses Dashboard vereinfacht komplexe Umgebungen und verwandelt rohe Netzwerkdaten in verwertbare Erkenntnisse für eine schnellere und zuverlässigere Reaktion auf Bedrohungen.
Datum:
Juni 2025
Freigabe:
9.2
QUX: Appliance-Schnittstelle
Erweiterung des GCP Brain-Angebots
Mit der Version 9.2 führt Vectra zusätzliche Brain-Angebote ein, die in der Google Cloud Platform (GCP) gehostet werden. Die neuen GCP-Brains können 5Gb/s und 15Gb/s verarbeiten und unterstützen die gleichen Funktionen wie andere Cloud.
Gruppenunterstützung hinzugefügt Für v2.x. QUX API
Ab Version 9.2 unterstützt Vectra das Abrufen von Gruppenmitgliedern über den endpoint/groups. Für weitere Informationen siehe: https://support.vectra.ai/vectra/article/KB-VS-1638
AI-Triage für Cloud und Cloud
Vectra AI hat AI Triage, seine proprietäre agentenbasierte KI-Lösung, in sein AWS- und Azure-Abdeckungsportfolio aufgenommen. AI-Triage untersucht jetzt automatisch AWS Cloud und Azure Cloud auf der Grundlage von Faktoren wie Prävalenz und Bedrohungsprofilen, um gutartige Aktivitäten in den Umgebungen der Kunden herauszufiltern. Die Auswirkung von AI-Triage ist eine Reduzierung der priorisierten Entitäten und des entsprechenden Untersuchungsaufwands für SOC-Analysten.
Verdächtige Protokollaktivität: Interne Erkennungen
Vectra AI erweitert den Erfassungsbereich der Suspect Protocol Activity-Erkennungen. Suspect Protocol Activity umfasst nun auch die Erkennung interner lateraler/reflexiver Angriffe und unterstützt LDAP-, Kerberos-, NTLM- und SMB-Protokolle. Diese Funktion ist standardmäßig deaktiviert, kann aber vom Kunden aktiviert werden und ist in der Standardproduktlinie von Detect enthalten. Weitere Informationen zu SPA finden Sie unter https://support.vectra.ai/s/article/KB-VS-1793.
Verdächtige Protokollaktivität: Brute Force
Vectra AI erweitert die Reichweite der Erkennung von Suspect Protocol Activity. SPA kann nun Brute-Force-Versuche über alle Protokolle hinweg erkennen. Diese Regel erkennt Brute-Force-Angriffe, bei denen ein Angreifer mehrere Authentifizierungsanfragen in einem kurzen Zeitraum versucht. Brute-Force-Angriffe können auf verschiedene Protokolle wie SMB, LDAP, FTP, RDP, SSH und HTTP abzielen und werden häufig von Angreifern genutzt, um sich unbefugten Zugriff auf Konten zu verschaffen.
Neue Erkennung: NTLM-Relay-Aktivität
Vectra AI hat eine neue Erkennung für NTLM-Relay-Aktivitäten eingeführt. Dies verbessert die Sichtbarkeit von Vectra auf die von Angreifern verwendeten Techniken für laterale Bewegungen. Diese Erkennung identifiziert Versuche, die NTLM-Authentifizierung auszunutzen, indem sie beobachtet, wann ein Angreifer einen Host abfragt und die erfasste Authentifizierung an einen anderen Host weiterleitet - oft als Teil von Bemühungen zur Privilegienerweiterung oder Domänenkompromittierung.
Neue Detektion: M365 Copilot - Entdeckung sensibler Daten
Vectra AI hat eine neue Erkennung für Entdeckungsverhalten im Zusammenhang mit M365 CoPilot eingeführt. Die neue M365 CoPilot Sensitive Data Discovery-Erkennung zeigt, dass eine CoPilot-Sitzung von einer Identität genutzt wurde, um auf Dateien zuzugreifen, die möglicherweise sensible Informationen enthalten. Diese Erkennung zielt darauf ab, Bedrohungsakteure aufzuspüren, die ein Konto in der Umgebung nutzen, um sensible Informationen zu entdecken.
Neue Detection Suite: AWS Bedrock-Detektionen
Vectra AI hat vier neue Erkennungen eingeführt, um verdächtige Verhaltensweisen im Zusammenhang mit der Nutzung von AWS Bedrock aufzudecken, einem vollständig verwalteten Service von AWS, der die Erstellung und Bereitstellung von generativen KI-Anwendungen vereinfacht.
- AWS Bedrock-Protokollierungskonfiguration deaktiviert: Diese Erkennung hebt Fälle hervor, in denen ein Auftraggeber beobachtet wurde, der die Prompt-Protokollierung für AWS Bedrock auf regionaler Ebene deaktiviert hat. Die Deaktivierung der Eingabeaufforderungsprotokollierung stoppt die Erfassung aller Eingabeaufforderungs- und Antwortaktivitäten in allen AWS Bedrock-Modellen und kann auf einen Versuch hindeuten, die Verteidigung zu beeinträchtigen oder böswillige Nutzung zu verbergen.
- AWS Bedrock Novel Model Enabled: Diese Erkennung identifiziert verdächtige Aktivitäten im Zusammenhang mit der Aktivierung eines AWS Bedrock-Modells durch eine Identität, die in der Vergangenheit keine derartigen Aktionen durchgeführt hat. Sie kennzeichnet den potenziell unbefugten Zugriff auf generative KI-Services, die sicherheitsrelevant und mit hohen Kosten verbunden sein können.
- AWS Verdächtige Bedrock-Aktivität: Diese Erkennung identifiziert verdächtige Aktivitäten im Zusammenhang mit der Aktivierung und dem Aufruf eines AWS Bedrock-Modells durch eine Identität, die in der Vergangenheit keine derartigen Aktionen durchgeführt hat. Die Kombination aus Aktivierung und anschließendem Aufruf eines Modells lässt vermuten, dass ein Angreifer das Modell sowohl testet als auch verwendet, um Antworten auf Kosten des Opfers zu generieren.
- AWS Bedrock Novel Aktiviert: Es wird jede Instanz erkannt, wenn ein AWS Bedrock-Grundmodell aktiviert ist, da diese Aktion ungewöhnlich ist und Kosten- oder Sicherheitsauswirkungen haben kann. Es handelt sich hierbei um eine informatorische Erkennung, die nicht zur Bewertung oder Priorisierung der Entität beiträgt. Sie ist als sicherheitsrelevanter Einblick gedacht und darf nicht sofort als verdächtig eingestuft werden.
Signalverbesserungen
Erheblich weniger gutartige Priorisierungswarnungen durch Verbesserungen des KI-Priorisierungsalgorithmus von Vectra und Erkennungsupdates. In einigen Fällen sehen Kunden bis zu 50 % weniger priorisierte Host- und Kontowarnungen - ohne Abstriche bei der Erkennung echter Bedrohungen.
- Azure AD & M365: Die Priorisierungswarnungen für Konten mit bestimmten Erkennungen wurden verfeinert, wodurch die Anzahl der gutartigen Warnungen reduziert und die Erkennung moderner Angriffe beibehalten wurde. Zu den betroffenen Erkennungen gehören die verdächtige Download-Aktivität von M365, die jetzt den Kontext der Autonomous System Number (ASN) einbezieht, und die Azure AD Suspicious Scripting Engine mit verbessertem Parsing für User Ag
Verbesserungen für eine schnelle Freigabe
Die folgenden Verbesserungen wurden seit dem letzten Software-Release-Zyklus an den Algorithmen vorgenommen. Kunden, die mit dem Update-Service von Vectra verbunden sind und den Remote-Support aktiviert haben, haben diese Verbesserungen erhalten. Alle anderen Kunden werden die folgenden Verbesserungen als Teil von 9.2 erhalten:
- NDR-166: Diese Version verbessert die DNS-Tunnel-Erkennung, indem sie die Abdeckung aller DNS-Antworttypen erweitert und so eine breitere und genauere Erkennung von Bedrohungen ermöglicht.
- NDR-144: Verbessert die C2-Erkennung gegenüber den vom Covenant C2 Framework verwendeten Techniken.
- NDR-202: Diese Version verbessert die Leistung des Algorithmus, der unsere Exfiltrationserkennungen antreibt, und ermöglicht eine schnellere Identifizierung von Bedrohungen.
- NDR-195: Verbessert die HTTP-Erkennung gegen Penetrationstechniken, die vom Kali Linux Package Repository verwendet werden.
- NDR-221: Verbessert die HTTP-Erkennung bei verdächtiger Verwendung von Windows Remote Management (WinRM) und erhöht die Transparenz bei potenziellem Missbrauch dieses Protokolls.
- NDR-232: Verbessert die Erkennung verdächtiger HTTP-Aktivitäten, um die Nutzung von Proxys zu berücksichtigen und die Erkennungsgenauigkeit in Proxy-Umgebungen zu verbessern.
Datum:
Juni 2025
Freigabe:
2025.06
RUX: SaaS-Bereitstellung
AI-Triage löst jetzt automatisch mehr gutartige Bedrohungen
Die firmeneigene agentenbasierte KI von Vectra AIist jetzt noch intelligenter. Unser aktualisierter AI-Triage-Algorithmus untersucht und löst jetzt automatisch 50 % der gutartigen C&C- und 25 % der gutartigen Recon-Erkennungen - eine drastische Reduzierung der gutartigen Ereignisse. Er nutzt sowohl lokale Muster als auch globale Erkenntnisse, um das bisher deutlichste Signal zu liefern.Weitere Details zu AI-Triage finden Sie in der AI-Triage KB und in unserem jüngsten Update-Video.
Neue Detection Suite: AWS Bedrock-Detektionen
Vectra AI hat vier neue Erkennungen eingeführt, um verdächtige Verhaltensweisen im Zusammenhang mit der Nutzung von AWS Bedrock aufzudecken, einem vollständig verwalteten Service von AWS, der die Erstellung und Bereitstellung von generativen KI-Anwendungen vereinfacht.
- AWS Bedrock-Protokollierungskonfiguration deaktiviert: Diese Erkennung hebt Fälle hervor, in denen ein Auftraggeber beobachtet wurde, der die Prompt-Protokollierung für AWS Bedrock auf regionaler Ebene deaktiviert hat. Die Deaktivierung der Eingabeaufforderungsprotokollierung stoppt die Erfassung aller Eingabeaufforderungs- und Antwortaktivitäten in allen AWS Bedrock-Modellen und kann auf einen Versuch hindeuten, die Verteidigung zu beeinträchtigen oder böswillige Nutzung zu verbergen.
- AWS Bedrock Novel Model Enabled: Diese Erkennung identifiziert verdächtige Aktivitäten im Zusammenhang mit der Aktivierung eines AWS Bedrock-Modells durch eine Identität, die in der Vergangenheit keine derartigen Aktionen durchgeführt hat. Sie kennzeichnet den potenziell unbefugten Zugriff auf generative KI-Services, die sicherheitsrelevant und mit hohen Kosten verbunden sein können.
- AWS Verdächtige Bedrock-Aktivität: Diese Erkennung identifiziert verdächtige Aktivitäten im Zusammenhang mit der Aktivierung und dem Aufruf eines AWS Bedrock-Modells durch eine Identität, die in der Vergangenheit keine derartigen Aktionen durchgeführt hat. Die Kombination aus Aktivierung und anschließendem Aufruf eines Modells lässt vermuten, dass ein Angreifer das Modell sowohl testet als auch verwendet, um Antworten auf Kosten des Opfers zu generieren.
- AWS Bedrock Novel Aktiviert: Es wird jede Instanz erkannt, wenn ein AWS Bedrock-Grundmodell aktiviert ist, da diese Aktion ungewöhnlich ist und Kosten- oder Sicherheitsauswirkungen haben kann. Es handelt sich hierbei um eine informatorische Erkennung, die nicht zur Bewertung oder Priorisierung der Entität beiträgt. Es handelt sich um eine sicherheitsrelevante Erkenntnis, die nicht sofort als verdächtig eingestuft werden darf.
Neue Detection Suite: AWS S3
Vectra AI hat drei neue Erkennungen eingeführt, um verdächtige Verhaltensweisen im Zusammenhang mit der Nutzung von AWS S3 in der Impact- und Exfil-Phase der cloud aufzudecken:
- AWS Verdächtige S3-Batch-Löschung: Diese Erkennung zeigt Verhaltensweisen im Zusammenhang mit groß angelegten Downloads und Löschungen mehrerer Dateien. Dieses Verhalten kann auf die destruktive Manipulationsphase der ransomware in der Umgebung hinweisen.
- AWS Verdächtige S3-Objekt-Löschung: Wie die neue S3-Batch-Löschungserkennung hebt diese Erkennung Verhaltensweisen hervor, bei denen einzelne Objekte heruntergeladen und dann aus einem S3-Bucket auf eine Weise gelöscht wurden, die auf die destruktive Manipulationsphase von ransomware in der Umgebung hinweisen kann.
- AWS Verdächtige S3-Verschlüsselung: Diese Erkennung hebt ungewöhnliche Verschlüsselungsaktivitäten hervor, die auf eine laufende ransomware hinweisen könnten.Sie wurde entwickelt, um die Verschlüsselung vieler S3-Objekte aufzudecken, die entweder einen externen KMS-Schlüssel (SSE-KMS) oder einen clientgesteuerten Schlüssel (SSE-C) verwenden.
Nahtloses Azure CDR Enablement
Vectra AI hat die Aktivierung von Azure CDR mit einem neuen Redirector Service Fix rationalisiert. Kunden können Azure CDR jetzt nahtlos einsetzen, ohne dass VPN- oder IP-Beschränkungen die Einrichtung blockieren. Dies beseitigt Reibungsverluste bei der Einrichtung der cloud und sorgt für eine schnellere Time-to-Value und sofortige Transparenz bei Azure-Bedrohungen. Sicherheitsteams erhalten eine schnellere Abdeckung mit weniger Aufwand.
Vectra Match Integrierte Regelsatzverwaltung
Vectra Match erleichtert jetzt die Erkennung bekannter Sicherheitsrisiken (Indicators of Compromise, IOCs) mit Suricata-kompatiblen Signaturen - externe Tools sind nicht erforderlich. Ab 9.3 können Sie Regeln direkt in der Plattform verwalten, ändern, aktivieren oder deaktivieren, und Ihre Änderungen bleiben auch nach Emerging Threats-Updates erhalten. Das beschleunigt die Einrichtung, vereinfacht die Wartung und gibt Ihnen die volle Kontrolle über die Erkennungslogik in die Hand. Weitere Informationen finden Sie unter Vectra Match Rulesets verwalten.
Datum:
Mai 2025
Freigabe:
2025.05
RUX: SaaS-Bereitstellung
Wir stellen vor: Executive Overview Report
Vectra stellt den Executive Overview Report über die Vectra AI Platform vor. Dieser Bericht richtet sich an CISOs und Sicherheitsverantwortliche, die in ihren Vorstands- oder Geschäftsführungssitzungen hochrangige Metriken präsentieren müssen. Zu den Metriken gehören der Noise-to-Signal-Tunnel, die mit Vectra eingesparte Untersuchungszeit, Angriffstrends und mehr. Dieser Bericht ermöglicht es Führungskräften, strategische Entscheidungen zu treffen und zu bewerten, wie Vectra das Risiko von Sicherheitsverletzungen für ihr Unternehmen reduziert.
Wir stellen vor: Globale Ansicht
Global View ermöglicht es großen Unternehmen und MSSPs, Bedrohungen über mehrere Brains und Tenants hinweg von einer einzigen RUX-Bereitstellung aus zentral zu verwalten und zu untersuchen - ideal für globale Unternehmen mit komplexen Umgebungen.
Wir stellen vor: Angriffsgrafiken
Das neue Angriffsdiagramm schafft sofortige Klarheit über aktive Bedrohungen, indem es visuell darstellt, wie sich Angreifer durch Ihr Netzwerk, Ihre cloud und Ihre Identitätsumgebung bewegen. Dank der KI-Priorisierung von Vectra wird jetzt jede Bedrohung direkt auf der Host- oder Kontoseite angezeigt. So erhalten Sie sofortigen Einblick, wo der Angriff begann, mit welchen Systemen er interagierte und wie sich sein Risikoniveau im Laufe der Zeit entwickelte.
Sicherheitsteams können aus drei intuitiven Ansichten wählen, um Bedrohungen auf die Weise zu untersuchen, die am besten zu ihrem Arbeitsablauf passt:
- Konnektivitätsdiagramm - Sehen Sie, wie verschiedene Entitäten während des Angriffs miteinander verbunden sind.
- Baumdiagramm - Zeigt die Abfolge der Angreiferaktionen in einem strukturierten Pfad an.
- Historischer Wert im Laufe der Zeit - Verstehen Sie, wie sich das Risiko der Bedrohung verändert und eskaliert hat.
Diese Funktion ermöglicht es SOC-Teams, schnell und sicher zu handeln, da Kontext und Dringlichkeit in einer einzigen, umsetzbaren Ansicht dargestellt werden.
Download des Verkehrsvalidierungsberichts Problem behoben
Wir haben ein Problem behoben, das einige Kunden - vor allem in großen RUX-Umgebungen - daran hinderte, den Netzwerk-Verkehrsvalidierungsbericht herunterzuladen, wenn dessen Größe ca. 6 MB überstieg. Der Arbeitsablauf wurde verbessert, um größere Berichtsdownloads zu unterstützen und einen zuverlässigen Zugriff auf die Daten der Verkehrsüberprüfung unabhängig von der Berichtsgröße zu gewährleisten.
Datum:
Mai 2025
Freigabe:
9.1
QUX: Appliance-Schnittstelle
Einführung des Vectra X47/M47-Systemnetzes
Mit der Version 9.1 führt Vectra die neuen Systeme X47 und M47 ein. Wie andere Systeme der X-Serie kann auch das X47 als Brain, Sensor oder im gemischten Modus eingesetzt werden. Der M47 unterstützt Vectra Stream mit einer Geschwindigkeit von bis zu 75 Gbps. Die Hardware verfügt über 4x1 Gbps Copper und 2 x 10/25 Gbps SFP28. Weitere Informationen zu den technischen Daten der Appliance finden Sie in den Appliance- und Sensor-Spezifikationen.
Die Anleitungen für den Einsatz finden Sie im X47 Quick Start Guide oder im M47 Quick Start Guide.
Ändern des Gruppentyps im Quadrant UX-Netzwerk
Ab Version 9.1 unterstützt Vectra die Konvertierung zwischen statischen und dynamischen Gruppentypen für QUX-Bereitstellungen. Bestehende Triage-Filter, die auf eine statische Gruppe verweisen, funktionieren weiterhin, ohne dass eine Änderung erforderlich ist, nachdem die Gruppe mithilfe einer Regex in der Konfiguration der dynamischen Gruppe neu definiert wurde. Dies sollte eine größere Flexibilität und eine einfachere Implementierung ermöglichen, wenn Kunden auf dynamische Gruppen umsteigen. Weitere Informationen über dynamische Gruppen finden Sie in den FAQ zu dynamischen Gruppen.
Verbesserungen der SSL-Schlüsselverarbeitung
Ab Version 9.1 unterstützt Vectra AI nun Zertifikate der Elliptischen Kurven-Kryptographie (ECC). Kunden können ihr eigenes Zertifikat über die vorhandenen Befehle hochladen. Außerdem wurden die Befehle zur Unterstützung von Certificate Signing Request (CSR) aktualisiert. Verwendung:
- `certificate replace-key`, um einen neuen Schlüssel und ein selbstsigniertes Zertifikat für den HTTPS-Server zu generieren, das im Wesentlichen auf die Standardeinstellungen zurückgesetzt wird, dem Kunden aber die Möglichkeit gibt, die Schlüssellänge anzupassen.
- Zertifikatsinfo", um dem Benutzer einige Informationen über das aktuelle HTTPS-Zertifikat zu zeigen.
Ausführliche Informationen zur Zertifikatsinstallation finden Sie unter: Installation von SSL-Zertifikaten (nur Quadrant UX).
Vectra Match Suricata Version Upgrade
Vectra AI hat Suricata aktualisiert, um neue Funktionen in der Suricata-Engine, einschließlich JA4, zu unterstützen, und wir haben Protokoll-Parsing für OT-Protokolle aktiviert. Die Basiskonfiguration suricata.yaml wurde ebenfalls aktualisiert, um die neuesten Suricata-Funktionen zu berücksichtigen. Details zur Suricata-Konfiguration von Vectra finden Sie hier: Vectra Match Suricata-Konfiguration.
Oauth2-Unterstützung für v2.x hinzugefügt. QUX-APIs
Vectra ai hat die QUX v2.x APIs aktualisiert, um Unterstützung für OAuh2-Authentifizierung zu bieten. Jetzt werden sowohl das bestehende Personal Access Token (PAT) als auch der Oauth2-Flow in v2.x unterstützt. Das Oauth2-Zugangs-Token ist 6 Stunden lang gültig, danach läuft es ab und ein neues Token muss mit den Anmeldedaten des API-Clients angefordert werden. Die Erstellung eines API-Clients darf nur über die Vectra-Benutzeroberfläche erfolgen. Der Zugriff auf v2.x-APIs, die älter als v2.5 sind, funktioniert auf die gleiche Weise wie bei v2.5. Die öffentliche Postman-Sammlung wurde für alle v2.x-Versionen aktualisiert. Für weitere Informationen siehe: REST API Schnellstartanleitung für Postman v2.5 mit OAuth2 (QUX).
Verbesserung der Erkennung versteckter Tunnel
Die Erkennung von versteckten Tunneln wurde verbessert, um neue beaconlose Verbindungen zu identifizieren, die mit externen Systemen in Kontakt treten. Diese Verbesserung bietet eine neue Abdeckung für Hidden Tunnel Kommandozeilen-basierte beaconless Angriffstools. Weitere Informationen über die Hidden Tunnel-Erkennung im Allgemeinen finden Sie unter Verständnis der Vectra AI .
Verbesserung der RDP-Aufdeckungserkennung
Die RDP Recon-Erkennung wurde erweitert, um RDP Password Spray-Angriffe zu erkennen, bei denen ein Angreifer versucht, eine kleine Anzahl von Passwörtern gegen eine große Anzahl von Konten zu testen. Die vorherige Version von RDP Recon konzentrierte sich auf den Versuch eines Angreifers, eine große Anzahl von Passwörtern gegen ein Konto auszuprobieren. Diese Erweiterung deckt nun auch Szenarien ab, in denen ein sehr oberflächlicher Brute-Force-Angriff über viele Konten hinweg durchgeführt wird.
AWS-Erkennungsverbesserungen AWS
An den folgenden AWS-Erkennungen wurden Verbesserungen vorgenommen, um die damit verbundene Zuverlässigkeit zu erhöhen. Die Einführung dieser Verbesserungen führt zu einer breiteren Abdeckung bösartiger Verhaltensweisen und kann mit einer geringfügigen Zunahme der priorisierten Entitäten in Kundenumgebungen verbunden sein.
- AWS Cryptomining: Diese Erkennung warnt vor dem Verhalten beim Starten mehrerer Hochleistungs-Recheninstanzen. Sie wurde erweitert, um ein breiteres Spektrum von Cryptomining-Aktivitäten aufzudecken, die sowohl menschlichen als auch nicht-menschlichen Auftraggebern zugeschrieben werden. Kunden können einen leichten Anstieg des Erkennungsvolumens beobachten.
- AWS-Angriffs-Tools: Diese Erkennung warnt vor bekannten Angriffstools in einer AWS-Umgebung. Sie wurde verbessert, um die Zuverlässigkeit zu erhöhen und die Falsch-Positiv-Rate zu senken.
Signalverbesserungen
Erheblich weniger gutartige Priorisierungswarnungen durch Verbesserungen des KI-Priorisierungsalgorithmus von Vectra und Erkennungsupdates. In einigen Fällen sehen Kunden bis zu 50 % weniger priorisierte Host- und Kontowarnungen - ohne Abstriche bei der Erkennung echter Bedrohungen.
- Azure AD & M365: Die Priorisierungswarnungen für Konten mit bestimmten Erkennungen wurden verfeinert, wodurch die Anzahl der gutartigen Warnungen reduziert und gleichzeitig die Erkennung moderner Angriffe beibehalten wurde. Zu den betroffenen Erkennungen gehören M365 DLL Hijacking Activity, Azure AD Suspicious Access from Cloud Provider und Azure AD Suspicious Sign-on.
- Netzwerk: Die Prioritätswarnungen für Hosts mit bestimmten Erkennungsmerkmalen wurden verfeinert, so dass weniger gutartige Warnungen ausgegeben werden, moderne Angriffe aber weiterhin erkannt werden. Zu den betroffenen Erkennungen gehören Muster wie verdächtige Admin-Aktivitäten und das gleichzeitige Auftreten von Port Scanning, Darknet Scanning und Port Sweeps.
Verbesserungen für eine schnelle Freigabe
Die folgenden Verbesserungen wurden seit dem letzten Software-Release-Zyklus an den Algorithmen vorgenommen. Kunden, die mit dem Update-Service von Vectra verbunden sind und den Remote-Support aktiviert haben, haben diese Verbesserungen erhalten. Alle anderen Kunden werden die folgenden Verbesserungen als Teil von 9.1 erhalten:
- NDR-96: Diese Version führt eine Verbesserung unseres RDP Recon-Algorithmus ein und erweitert die Abdeckung von RDP Sweep-Angriffen, bei denen die Anzahl der versuchten Passwörter pro Konto durch Umgehungen begrenzt wird.
- NDR-106: Verbessert unsere C2-Erkennung gegen die von Mythic C2 verwendeten Techniken.
- NDR-104: Mit dieser Version wird die Angriffsabdeckung für den Apache Camel Case Exploit eingeführt: CVE-2025-27636.
- NDR-73: Diese Version führt eine Verbesserung des Angriffssignals für den externen Fernzugriff ein, um gutartige True-Positive-Erkennungen für beliebte Ziele zu verringern.
- NDR-108: Diese Version führt eine Verbesserung ein, um die Skalierung und den Zustand von Beacon Detector bei hoher Last zu verbessern, indem Beacon-Metadaten für beliebte, gutartige Ziele in der Umgebung begrenzt werden.
Datum:
April 2025
Freigabe:
2025.04
RUX: SaaS-Bereitstellung
Verbesserte Suche nach Sensornamen
Wir haben die Suchfunktion auf der Seite "Erkennungen" erweitert, um die Suche nach dem Sensornamen anstelle der internen Sensor-LUID zu unterstützen. Dieses Update geht auf Kundenfeedback ein und erleichtert die Suche nach Erkennungen, die mit bestimmten Sensoren verbunden sind, die erkennbare Namen verwenden.
Verbesserte Erkennung von Copilot-Missbrauch in M365
Als Reaktion auf das starke Kundeninteresse erweitern wir den Schutz vor potenziellem Missbrauch von Microsoft Copilot. Zusätzlich zur bestehenden M365-Erkennung von verdächtigen Copilot-Zugriffen (die Zugriffe von ungewöhnlichen Standorten kennzeichnet) führen wir eine neue Erkennung ein: M365 Copilot Sensitive Data Discovery. Damit wird das Verhalten von Angreifern identifiziert, die versuchen, sensible Dokumente über Copilot in Microsoft 365 zu finden.
Datum:
März 2025
Freigabe:
2025.03
RUX: SaaS-Bereitstellung
Anreicherung des AI-Priorisierungskontexts
Vectra zeigt jetzt maßgeschneiderte Angriffsprofile an, wenn sich die Erkennungen über mehrere Angriffsflächen erstrecken, und hilft so, komplexe Bedrohungen klarer zu identifizieren. Es wurden zwei neue Profiltypen eingeführt:
- Hybrider Netzwerk-Angreifer: Weist auf einen Angreifer hin, der sowohl in Netzwerkidentitäts- als auch in cloud aktiv ist, was auf koordinierte Aktivitäten in lokalen und cloud hindeutet.
- Cloud : Ein Angreifer, der über mehrere cloud Dienste wie Identitätsanbieter, SaaS-Plattformen oder öffentliche cloud hinweg operiert, ohne direkt in die Identitätssysteme des Netzwerks einzugreifen.
Diese Profile sollen die Art der hybriden Bedrohungen widerspiegeln und den Bedrohungskontext in der Benutzeroberfläche verbessern.
Unterstützung von AI Triage für Azure-Erkennungen
Vectra verbessert die Unterstützung für Azure-Erkennungen durch die Aktivierung von AI Triage für Azure CDRCloud Detection and Response) Alarme. Für jeden bestehenden Azure-Erkennungstyp evaluieren wir geeignete KI-Destillationsalgorithmen und wenden sie an, definieren relevante Kontextfelder und berücksichtigen alle spezifischen Verarbeitungsanforderungen. Dies wird dazu beitragen, effizientere Erkenntnisse zu gewinnen und die Klarheit der Erkennung innerhalb der Plattform zu verbessern.
Datum:
März 2025
Freigabe:
9.0
QUX: Appliance-Schnittstelle
Einführung von dynamischen Gruppen auf Quadrant
Ab Version 9.0 unterstützt Vectra AI jetzt dynamische Gruppen in der Quadrant UX. Dynamische Gruppen sind eine Funktion der Vectra AI , mit der Kunden mithilfe von Regex-Regeln definieren können, welche Hosts oder Konten zu den einzelnen Triage-Gruppen gehören sollen, so dass Entitäten bei ihrer Erkennung automatisch in Gruppen sortiert werden. Diese Funktion verringert den Zeitaufwand, den Kunden für die Verwaltung und Aktualisierung von Gruppen aufwenden müssen. Die Unterstützung für diese Funktion durch Respond UX wurde im Dezember 2024 eingeführt. Weitere Informationen finden Sie unter: https://support.vectra.ai/s/article/KB-VS-1839.
Hochleistungs-GCP-Gehirn-Netzwerk
Vectra ai hat eine neue 64-Kern-Variante des GCP Brain entwickelt und das bestehende 96-Kern-Brain validiert, um einen höheren Gesamtdurchsatz als bisher veröffentlicht zu unterstützen. Einzelheiten finden Sie im GCP Brain Deployment Guide.
Proxy-Unterstützung für verdächtige Protokollaktivitäten und Match
Ab Version 9.0 bietet Vectra AI automatische Proxy-Unterstützung für Match und SPA. Obwohl keine Benutzeraktion erforderlich ist, sind zusätzliche Variablen für Match verfügbar. Weitere Informationen finden Sie in der Match https://support.vectra.ai/s/article/KB-VS-1635.
Southside Proxy IPs über CLI
Seit Version 9.0 bietet Vectra die Möglichkeit, die Proxy-IPs der Southside Learned List über die Kommandozeile anzuzeigen. Southside Proxies identifizieren Proxies, bei denen Vectra zwischen dem Client und dem Proxy sitzt. Dies unterscheidet sich von Northside-Proxys, die unter Verwalten -> Proxys in der Benutzeroberfläche konfiguriert werden. Verwenden Sie "show proxy --southside", um die Southside-Proxys anzuzeigen, die das System aus der Beobachtung des Netzwerkverkehrs gelernt hat.
Verbesserter Verkehrsüberprüfungsbericht
Ab Version 9.0 hat Vectra AI neue Felder in den erweiterten Bericht zur Überprüfung des Netzwerkverkehrs aufgenommen, der auf der Seite Netzwerkstatistiken verfügbar ist. Die neuen Felder enthalten Statistiken zu NIC-Fehlern, Paketabschneidungen und Datenverlusten/Löchern im Datenverkehr. Weitere Informationen finden Sie unter: https://support.vectra.ais/article/KB-VS-1648.
S1 SFP+-Schnittstellen für MGT1 oder Capture-Verwendung unterstützt
Starting in 9.0, Vectra now supports the use of the S1’s two onboard SFP+ interfaces for capture or management. The command “set management <default|sfp>” will alter the interface configuration for the MGT1 port. The command “set capture <default|sfp>” will alter the interface assignment used for capture. This creates 4 total configurations for management or capture. All options with new interface assignment diagrams for each are detailed in the S1 Quick Start Guide. Please note: The rated throughput of the S1 appliance does not change when using SFP+ ports. This only changes the physical interface assignments. Care should be taken to only forward a supported amount of traffic to the S1.
X29/M29 Appliance - Neue Syntax für die Verwendung von SFP+ für MGT
The X29/M29 appliances have an option to configure one of their SFP+ interfaces to be used as the MGT1 management port. The command has changed in version 9.0 to be consistent with the command syntax that is used now for all appliances that offer options to change similar interface options. The old command was “set management speed <1G|10G>” and the new command is “set management <default|sfp>”. Please see the X29 Quick Start Guide or the M29 Quick Start Guide for details.
Erweiterungen der AWS-Erkennungen
An den folgenden AWS-Erkennungen wurden Verbesserungen vorgenommen, um die damit verbundene Zuverlässigkeit zu erhöhen. Die Einführung dieser Verbesserungen führt zu einer breiteren Abdeckung bösartiger Verhaltensweisen und kann mit einer geringfügigen Zunahme der priorisierten Entitäten in Kundenumgebungen verbunden sein.
- AWS CloudTrail-Protokollierung deaktiviert: Diese Erkennung warnt vor einer Technik zur Umgehung der Verteidigung, bei der die AWS-Protokollierung deaktiviert wird. Es wurden Verbesserungen am Modell vorgenommen, um das Verhaltensprofil für dieses bösartige Verhalten zu erweitern.
- AWS CloudTrail-Protokollierung modifiziert: Diese Erkennung warnt vor der Verteidigungsumgehungstechnik der Herabstufung der AWS-Protokollierung. Es wurden Verbesserungen am Modell vorgenommen, um das Verhaltensprofil für dieses bösartige Verhalten zu erweitern.
- AWS User Hijacking: Diese Erkennung warnt vor Persistenztechniken bei der Erstellung von AWS-Zugangsschlüsseln. In diesem Modell wurde zusätzliches Lernen eingeführt, um das wiederholte Auftreten von Verhaltensweisen und die daraus resultierenden Auswirkungen auf das Volumen der auftauchenden Warnungen zu berücksichtigen. Diese Erweiterung führt zu einer verbesserten Wirksamkeit der Warnungen vor diesem riskanten Verhalten.
Verbesserungen bei der Auswertung von M365-Erkennungen
Für die folgenden Microsoft 365-Erkennungen wurden Verbesserungen eingeführt, um das Risiko der zugrunde liegenden Verhaltensweisen besser zu berücksichtigen und sie zeitnah zur Überprüfung anzuzeigen. Die Einführung dieser Verbesserungen kann zu Änderungen bei der Anzahl der Entitäten führen, die innerhalb der Vectra-Plattform priorisiert werden:
- M365 Verdächtige Power Automate-Aktivität: Diese Erkennung warnt vor potenziellem Exfiltrations- oder C2-Verhalten unter Verwendung von Power Automate in der Umgebung. Die an dieser Erkennung vorgenommenen Verbesserungen führen zu einer erheblichen Verbesserung der Zuverlässigkeit dieser Erkennung und zu einer Verringerung der Rate der bei dieser und ähnlichen Erkennungen (M365 Power Automate HTTP Flow Creation und M365 Suspicious Power Automate Flow Creation) beobachteten False Positives.
Datum:
Februar 2025
Freigabe:
2025.02
RUX: SaaS-Bereitstellung
Unterstützung für die Authentifizierung über OAuth bereitstellen
Vectra unterstützt sowohl den bestehenden Personal Access Token (PAT) als auch den Oauth2-Flow in v2.x. Der Oauth2-Zugangstoken ist 6 Stunden lang gültig, danach läuft er ab, und ein neuer Token muss mit den Anmeldedaten des API-Clients angefordert werden. Die Erstellung eines API-Clients darf nur über die Vectra-Benutzeroberfläche erfolgen. Der Zugriff auf v2.x-APIs, die älter als v2.5 sind, funktioniert auf die gleiche Weise wie bei v2.5. Die öffentliche Postman-Sammlung wurde für alle v2.x-Versionen aktualisiert.
M365 GCC-Unterstützung
Vectra unterstützt jetzt Microsoft 365 Government Community Cloud (GCC) Umgebungen. Während die Unterstützung bisher für GCC-High- und Azure AD-Kunden bestand, erweitert dieses Update die Abdeckung auf Kunden, die in GCC-Umgebungen arbeiten, die üblicherweise von US-Bundesstaaten, lokalen und Bundesbehörden genutzt werden. Durch die Integration mit Microsofts GCC-spezifischen Endpunkten gewährleistet Vectra AI eine sichere und konforme Log-Aggregation, um vollständige Transparenz und Bedrohungserkennung über alle cloud für Behörden zu bieten.
Cybereason EDR-Unterstützung
Vectra hat Unterstützung für die Aufnahme von EDR-Alarmen von Cybereason hinzugefügt. Kunden, die Cybereason verwenden, können jetzt ihre Integration in Cantina konfigurieren, um die Aufnahme von Alarmen und die Sichtbarkeit zu ermöglichen.
Ändern des Gruppentyps
Ab Version 9.1 unterstützt Vectra die Konvertierung zwischen statischen und dynamischen Gruppentypen für QUX-Bereitstellungen. Bestehende Triage-Filter, die auf eine statische Gruppe verweisen, funktionieren weiterhin, ohne dass eine Änderung erforderlich ist, nachdem die Gruppe mithilfe einer Regex in der Konfiguration der dynamischen Gruppe neu definiert wurde. Dies sollte eine größere Flexibilität und eine einfachere Implementierung ermöglichen, wenn Kunden auf dynamische Gruppen umsteigen. Weitere Informationen zu dynamischen Gruppen finden Sie in den FAQ zu dynamischen Gruppen
Datum:
Januar 2025
Freigabe:
2025.01
RUX: SaaS-Bereitstellung
Unterstützung der Deaktivierung der DNS-Erkennung
Benutzer können jetzt die DNS-Antwortpaketprüfung auf der Seite Einstellungen deaktivieren. Bei Auswahl dieser Option wird eine Warnmeldung angezeigt, um die Benutzer darüber zu informieren, dass die Deaktivierung der Protokollierung von DNS-Antwortpaketen Auswirkungen auf entsprechende Erkennungen haben kann.
Untersuchen Sie von jedem Ort aus: Zuletzt gesehene IP
Benutzer können jetzt von wichtigen Datenpunkten außerhalb der Seite "Erweiterte Ermittlungen" zu den erweiterten Ermittlungen wechseln. Mit diesem Update wird ein neues Menü für das Feld "Zuletzt gesehene IP" innerhalb der Host-Karten auf der Seite "Antworten" eingeführt. Wenn Sie den Mauszeiger über das Feld "Zuletzt gesehene IP" bewegen, können Benutzer eine Abfrage auswählen, die die IP-Adresse enthält, und direkt in die Ergebnisse der Abfrage auf der Seite "Erweiterte Untersuchungen" wechseln.
Verbesserte Hauptnavigation
Um die wachsende Zahl von Dashboards zu unterstützen, wurde die Navigation von horizontalen Registerkarten auf eine zusammenklappbare vertikale Seitenleiste umgestellt. Diese Neugestaltung bietet den Nutzern eine skalierbarere und benutzerfreundlichere Möglichkeit, auf Dashboards zuzugreifen und sie zu verwalten.
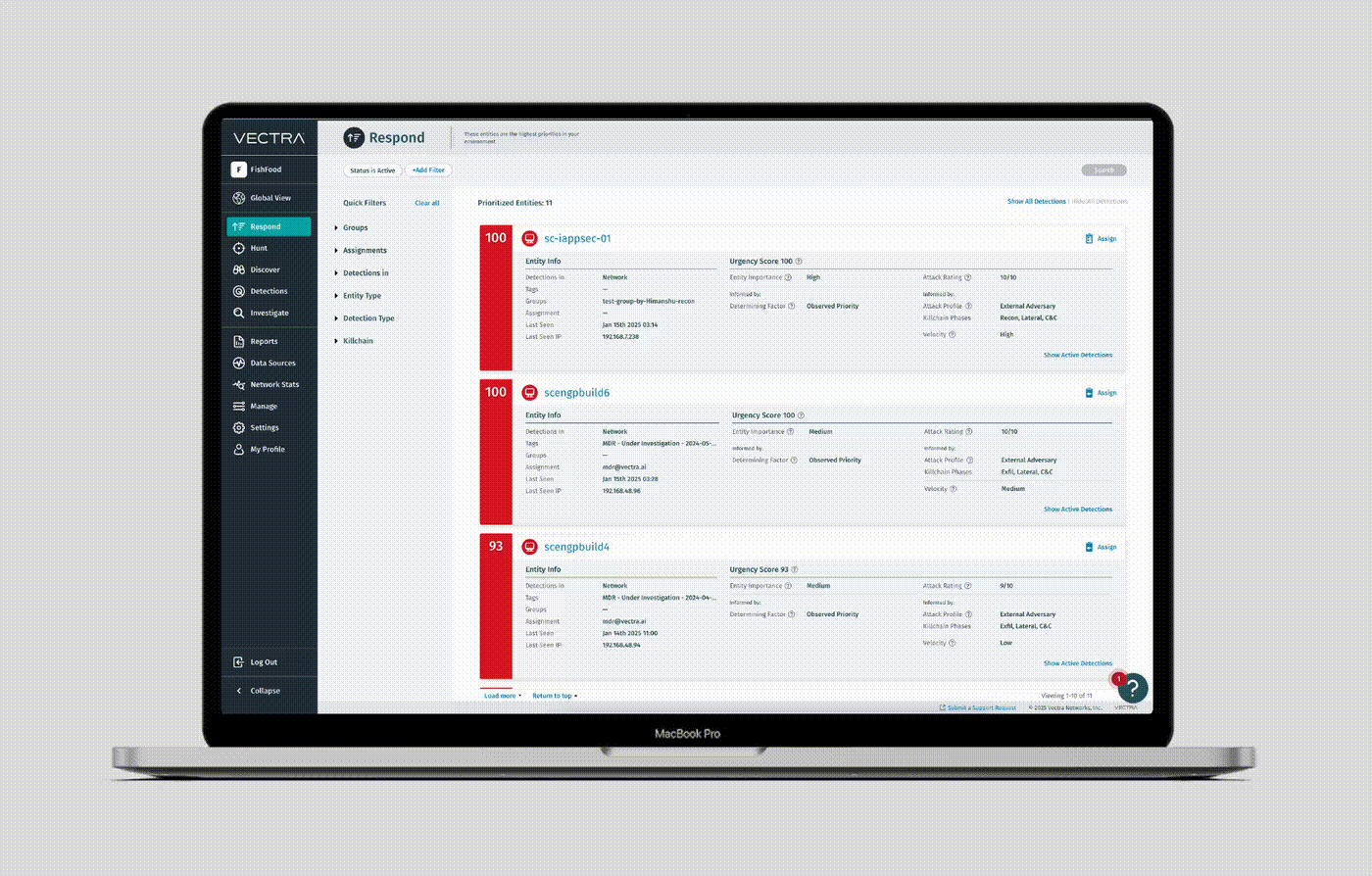
Verbesserungen bei der Abstimmung von Konten im Verbund
Dieses Update bietet Unterstützung für den Abgleich von Federated-Konten in EntraID mit den entsprechenden User Principal Names (UPNs), einschließlich des Abgleichs mit passenden Azure CDR-Entitäten und M365/AzureAD-Konten.
Datum:
Januar 2025
Freigabe:
8.10
QUX: Appliance-Schnittstelle
Verbesserungen bei der Sicherung von Ausfallzeiten
Ab Version 8.10 hat Vectra die Backup-Ausfallzeit auf weniger als zehn Minuten verkürzt. Die Benutzerfreundlichkeit der Backup-Funktion bleibt gleich, diese Lösung führt zu einer drastisch reduzierten Abschlusszeit für Backups.
Neuer VMWare vSensor
Ab Version 8.10 erhöht Vectra die Bandbreitenfähigkeiten der VMWare vSensoren. Die VMWare-Sensoren sind in der Lage, einen Datenverkehr von 20 Gb/s zu verarbeiten und unterstützen die gleichen Funktionen wie andere Cloud. Weitere Informationen finden Sie in unserem Implementierungsleitfaden: https://support.vectra.ai/s/article/KB-VS-1075
Versteckter DNS-Tunnel - NoReply-Erweiterung
Als Teil der Version 8.10 hat Vectra die Erkennung von versteckten DNS-Tunneln verbessert, um Szenarien zu erkennen, in denen ein Angreifer versucht, Daten über DNS zu exfiltrieren, indem er Techniken einsetzt, bei denen der Server nicht reagiert (der Tunnel ist also nur ein einseitiger Tunnel, bei dem der Angreifer die Daten vom Eingang zum Ausgang streamt).
Scoring-Verbesserungen für Azure AD und M365-Erkennungen
Für die folgenden Microsoft 365- und Azure AD-Erkennungen wurden Verbesserungen eingeführt, um das Risiko der zugrundeliegenden Verhaltensweisen besser zu berücksichtigen und sie zeitnah zur Überprüfung anzuzeigen. Die Einführung dieser Verbesserungen kann zu Änderungen bei der Anzahl der Entitäten führen, die innerhalb der Vectra-Plattform priorisiert werden:
- Azure AD/Entra ID
- Azure AD-Domäneneinstellungen geändert: Diese Erkennung warnt, wenn eine neue, nicht verifizierte oder verifizierte Domäne verdächtigerweise zur Umgebung hinzugefügt wird.
- Azure AD Mandantenübergreifende Zugriffsänderung: Diese Erkennung warnt, wenn die Einstellungen für den mandantenübergreifenden Zugriff eines Partners hinzugefügt oder aktualisiert werden.
- Azure AD Neue Zertifizierungsstelle registriert: Diese Erkennung warnt, wenn eine neue Zertifizierungsstelle für den Mandanten registriert wird.
- Azure AD Privilege Operation Anomaly: Diese Erkennung warnt vor potenzieller Privilegienerweiterung oder Account-Takeover-Verhalten in der Umgebung. Die an dieser Erkennung vorgenommenen Verbesserungen führen zu einer erheblichen Verbesserung der Erkennungsgenauigkeit und einer Verringerung der Rate der Fehlalarme.
- Microsoft 365
- M365 Phishing Konfigurationsänderung: Diese Erkennung warnt, wenn die mit einem Phishing verbundene Konfiguration geändert wird.
M365 SecOps Mailbox-Änderung: Diese Erkennung warnt, wenn die mit einem SecOps-Konto verbundene Konfiguration geändert wird.
Datum:
Dezember 2024
Freigabe:
2024.12
RUX: SaaS-Bereitstellung
Einführung von CDR für Azure
Vectra AI fügt KI-gestützte Erkennungsfunktionen hinzu, die das Verhalten von Angreifern aufdecken, die auf Microsoft cloud und Microsoft Copilot abzielen, und liefert so die dringend benötigte Verstärkung für die nativen Tools der Kunden:
- Erkennt Angreifer, die Azure Cloud missbrauchen
- Identifiziert echte Angriffe in Echtzeit und verbindet die Punkte in Azure IaaS, Active Directory, Microsoft 365, Copilot und Microsoft Entra ID in einem einzigen Fenster.
- Stoppt Azure-Kompromittierung und ermöglicht es Sicherheitsteams, 1) Sicherheitslücken für Azure Cloud zu identifizieren, 2) einfach auf relevante, angereicherte Azure-Aktivitäts- und Ressourcenprotokolle zuzugreifen und 3) entscheidende Reaktionsmaßnahmen zu ergreifen, um an einem Angriff beteiligte Microsoft Entra ID-Konten schnell einzudämmen
Dynamische Gruppen
Gruppen wurden erweitert, um eine dynamische Mitgliedschaft durch die Definition eines regulären Ausdrucks (RegEx) zu unterstützen, um die Namen der einzuschließenden Mitglieder zu beschreiben. Dies führt zu einer enormen Einsparung von Arbeitsaufwand bei der Verwaltung von Gruppen für Triage oder Scoring. Die Gruppenzugehörigkeit wird zur Laufzeit ausgewertet, um sicherzustellen, dass neue Entitäten korrekt kategorisiert werden, ohne dass Sie zusätzlichen Aufwand betreiben müssen. Dies gilt für Gruppen für Hosts oder Konten.
Datum:
November 2024
Freigabe:
2024.11
RUX: SaaS-Bereitstellung
Gespeicherte Abfragen für die Erweiterte Untersuchung
Rationalisierung des Abfrageverwaltungsprozesses innerhalb der Advanced Investigation Experience von Respond UX durch die Möglichkeit, Abfragen zu speichern und zu teilen.
Analysten können Abfragen nahtlos erstellen, speichern, aktualisieren und löschen, was Wiederholungen reduziert und die Wiederverwendung fördert. Analysten können außerdem gespeicherte Abfragen mit anderen Analysten teilen, was die Zusammenarbeit und den Wissensaustausch in Teams fördert.
Datum:
Oktober 2024
Freigabe:
2024.10
RUX: SaaS-Bereitstellung
Region Schweiz ist aktiviert
Wir unterstützen jetzt Respond UX-Bereitstellungen in der Schweiz. Dies ermöglicht es Schweizer Kunden, bei Bedarf innerhalb ihrer eigenen Grenzen zu hosten. Diese neue Region unterstützt alle Vectra-Produkte.
Selektive PCAPs sind für Kunden des Respond UX-Netzwerks aktiviert
Mit dieser Version unterstützen wir nun vollständig selektive PCAPs für unsere Respond UX Netzwerkkunden. Diese Funktion ermöglicht es Ihnen, den Vectra-Sensor-Footprint zu nutzen, um eine benutzerdefinierte Paketerfassung aus der Ferne durchzuführen - ohne Zugriff auf die lokale Infrastruktur zu erhalten.
Datum:
September 2024
Freigabe:
2024.09
RUX: SaaS-Bereitstellung
Vectra Match - Kuratiertes Regelwerk
Mit dieser Version hat Vectra einen Link zum Herunterladen eingeführt, über den die Benutzer das kuratierte Regelwerk für Vectra Match abrufen können. Ein neuer Link wird in der Benutzeroberfläche auf der Vectra Match für täglich aktualisierte Inhalte erscheinen und kann auch über die API konsumiert werden. Weitere Details finden Sie unter Vectra Match Curated Ruleset.
Datum:
Juli 2024
Freigabe:
2024.07
RUX: SaaS-Bereitstellung
Copilot für M365 Dashboard für Bedrohungsoberflächen
Dies ist ein neues Dashboard in Respond UX für M365, das sich auf die unternehmensweite Copilot-Nutzung konzentriert. Verwenden Sie dieses Dashboard, um die Copilot-Nutzung innerhalb Ihrer Organisation zu verstehen und um zu sehen, auf welche Dateien Copilot zugreift.
Integration Health Endpunkte zur V3 API hinzugefügt
Neuer endpoint auf der V3 Respond UX API, um Einblicke in Integrationen wie EDR, AD usw. zu ermöglichen, so dass Sie diese kritischen Integrationen im Laufe der Zeit überwachen können.
Datum:
Juni 2024
Freigabe:
2024.06
RUX: SaaS-Bereitstellung
Vectra Match jetzt auch in Instant und Advanced Investigations verfügbar
Mit dieser Version wird Vectra Match in Respond UX unterstützt. Die Unterstützung von Respond UX umfasst die gesamte WebUI- und API-Unterstützung von Quadrant UX sowie die Unterstützung von Instant und Advanced Investigation für Match . Weitere Einzelheiten entnehmen Sie bitte dem Match Deployment Guide.
Benutzerverwaltung zur V3-API hinzugefügt
Neuer endpoint auf der V3 Respond UX API zur Verwaltung eigenständiger Benutzer innerhalb Ihres Respond UX Tenants. Verwenden Sie diese API, um Benutzer automatisch aus Ihren Onboarding- oder Offboarding-Playbooks bereitzustellen oder zu entfernen.
Datum:
Mai 2024
Freigabe:
2024.05
RUX: SaaS-Bereitstellung
AzureAD-Konto automatisch sperren
AzureAD Account Automatic Lockdown wurde entwickelt, um Vectra-Benutzer mit proaktiven Abwehrmechanismen gegen Bedrohungen auszustatten. Wenn Sie diese Funktion aktivieren, können Sie jetzt zwei wichtige Einstellungen konfigurieren: Dringlichkeitsscore und Wichtigkeit der Entität. Dieser duale Konfigurationsansatz stellt sicher, dass eine Entität, die vordefinierte Schwellenwerte für Dringlichkeit und Wichtigkeit überschreitet, automatisch für eine vom Benutzer festgelegte Dauer in einen Sperrzustand übergeht. Diese Zeitspanne ermöglicht eine gründliche Untersuchung und stellt sicher, dass potenzielle Bedrohungen untersucht werden und eine wirksame Reaktion erfolgen kann.
Datum:
April 2024
Freigabe:
2024.04
RUX: SaaS-Bereitstellung
Netzwerk-Bedrohungsfläche Dashboard
Erste Veröffentlichung eines neuen Threat Surface Dashboards für unsere Respond UX Netzwerkkunden. Dieses Dashboard enthüllt eine Fülle von Informationen über Ihre Umgebung und deckt Angriffsflächen und Compliance-Probleme auf. Nutzen Sie dieses Dashboard, um die Verwendung veralteter und veralteter Protokolle in Ihrer Umgebung zu untersuchen und die Einhaltung Ihrer festgelegten Richtlinien für Bereiche wie SMBv1 sicherzustellen.
Detect for AWS - Unterstützung für S3 copyObject in CloudTrail-Protokollen
Standardmäßig füllt CloudTrail S3-Buckets durch putObject-Ereignisse auf. Beim Ingest verwarf Vectra Ereignisse, die mit dem Befehl copyObject gefüllt wurden. Mit dieser Änderung nimmt Vectra Ereignisse auf, die mit copyObject oder putObject erstellt wurden.
Konsolidierung von AzureAD und AD-Lockdown
Für Kunden mit der Option, sowohl AzureAD- als auch AD-Konten zu sperren (Kunden mit Netzwerk und Detect für AzureAD), haben wir die Erfahrung harmonisiert, um eine bessere Gesamterfahrung zu bieten - die Integration dieser beiden unterschiedlichen Funktionen und die Ermöglichung einer größeren Transparenz und Selektivität für die Aktion, die Sie durchführen möchten. Wählen Sie aus, ob Sie Azure AD oder AD oder beides sperren möchten, und zwar über dieselbe Anwendung.
Datum:
März 2024
Freigabe:
2024.03
RUX: SaaS-Bereitstellung
AD-Konto automatisch sperren
AD Account Automatic Lockdown wurde entwickelt, um Vectra-Benutzern proaktive Abwehrmechanismen gegen Bedrohungen zu bieten. Wenn Sie diese Funktion aktivieren, können Sie jetzt zwei wichtige Einstellungen konfigurieren: Dringlichkeitsscore und Wichtigkeit der Entität. Dieser duale Konfigurationsansatz stellt sicher, dass eine Entität, wenn sie vordefinierte Schwellenwerte für Dringlichkeit und Wichtigkeit überschreitet, automatisch für eine vom Benutzer festgelegte Dauer in einen Sperrzustand übergeht. Diese Zeitspanne ermöglicht eine gründliche Untersuchung und stellt sicher, dass potenzielle Bedrohungen untersucht werden und eine wirksame Reaktion erfolgen kann.
Verbesserungen in der Benutzerverwaltung
Mit dieser Erweiterung erhalten Respond UX-Administratoren das vertraute Erscheinungsbild der Benutzerverwaltungsoberfläche, die auf unserer Quadrant UX-Plattform angeboten wird. Administratoren können nun Benutzer und ihre Rollen einfach verwalten und so bei der Bereitstellung von Benutzern und der Überprüfung des Systemzugriffs ein Höchstmaß an Genauigkeit gewährleisten.
Azure AD Verdächtiger Zugriff von Cloud
Vectra hat die Fähigkeit eingeführt, Angreifer zu erkennen, die eine Identität kompromittieren und von einem öffentlichen cloud wie Amazon, Azure oder GCP darauf zugreifen, um die Erkennung zu umgehen und ihren wahren Standort zu verbergen. Die Erkennung nutzt maschinelles Lernen, um festzustellen, ob ein Benutzer normalerweise über die öffentliche cloud auf sein Konto zugreift. Bening-Warnungen können ausgelöst werden, wenn ein Benutzer eine Anwendung verwendet, die über eine öffentliche cloud oder cloud gehostete virtuelle Maschinen läuft. Diese neue Warnung priorisiert ein Konto, wenn es zusammen mit anderen Warnungen auftritt, ähnlich wie die Azure AD Suspicious Sign-On Warnung.