Die Illusion der Berichterstattung
Jeder Sicherheitsverantwortliche, der sein Geschäft unter Nutzung des Microsoft-Ökosystems aufgebaut hat, hat sich dieselbe Frage gestellt: Sind wir ausreichend geschützt?
MFA ist aktiviert. Bedingter Zugriff wird erzwungen. EDR ist bereitgestellt.
Dennoch gelangen Angreifer immer noch durch – nicht indem sie Schwachstellen ausnutzen, sondern indem sie Vertrauen missbrauchen.
Gruppen wie Midnight Blizzard, Scattered Spider, Mango Sandstorm und Peach Sandstorm beweisen dies immer wieder:
- Scattered Spider – Kostete die britische Co-operative Group 107 Millionen Dollar nach einem durch Identitätsdiebstahl ausgelösten hybriden Angriff auf ihre Einzelhandels- und Dienstleistungsaktivitäten.
- Midnight Blizzard (APT29) – Greift weiterhin Regierungs- und öffentliche Einrichtungen an, indem es groß angelegte Angriffe auf Anmeldedaten und den Diebstahl von Zugriffstoken nutzt.
- Mango Sandstorm (MERCURY) – Führte zerstörerische Angriffe auf lokale und cloud in hybriden Microsoft-Umgebungen durch.
Laut IBM belaufen sich die durchschnittlichen Kosten für die Behebung einer cloud öffentlichen cloud auf 4,7 Millionen US-Dollar.
Angreifer brechen nicht ein, sie melden sich an. Sie kapern legitime Identitäten von Menschen und Maschinen und agieren innerhalb der Grenzen von Richtlinien, die zum Schutz des Unternehmens entwickelt wurden. Sobald sie drin sind, bewegen sie sich lateral über das lokale Rechenzentrum, Active Directory, Entra ID, M365 und cloud, leben von dem, was sie vorfinden, und mischen sich unter legitime Aktivitäten.
Das Problem ist nicht die Prävention, sondern die Erkennung, wenn die Prävention versagt. Microsoft-Tools sind hervorragend geeignet, um bekannte Bedrohungen zu blockieren und die Sicherheitslage zu verbessern, aber sie bieten nur begrenzte Einblicke in Verhaltensweisen nach einer Kompromittierung: Missbrauch von Berechtigungen, laterale Bewegungen, Living-off-the-Land-Techniken und Datenexfiltration, die sich unbemerkt über miteinander verbundene Domänen ausbreiten.
Moderne Angreifer nutzen die Lücken zwischen diesen Systemen aus – die blinden Flecken, an denen die Telemetrie aufhört und der Kontext verloren geht. Dort entsteht der eigentliche Schaden, und dort sind die Erkennung, Untersuchung und Reaktion nach einem Angriff von entscheidender Bedeutung.
Wo native Tools an ihre Grenzen stoßen
Der Sicherheitsstack von Microsoft überwacht Konfiguration, Identität und Endpunkte – übersieht jedoch häufig die Bewegungen von Angreifern, wenn diese sich zwischen unzusammenhängenden Oberflächen des Ökosystems bewegen. Selbst innerhalb von Entra ID, M365 und Azure übersehen native Erkennungsmechanismen oft subtile, aber häufige Angreiferaktivitäten.
Eine weitere Herausforderung für SOC-Teams besteht darin, Signale über Microsoft-Oberflächen hinweg zu korrelieren, insbesondere wenn Warnmeldungen von unterschiedlichen Tools mit inkonsistenten Telemetrieformaten stammen. Jede Oberfläche spricht eine andere Sprache, sodass die Verteidiger den Kontext in Echtzeit übersetzen und zusammenfügen müssen. Wertvolle Zeit geht verloren, wenn man Warnmeldungen mit niedriger Priorität nachgeht, die, wenn man sie zusammen betrachtet, einen koordinierten Angreifer offenbaren, der sich über verschiedene Oberflächen hinweg bewegt. Ereignisse, die isoliert betrachtet harmlos erscheinen, werden oft kritisch, wenn sie korreliert und in einen Kontext gestellt werden – und genau diese Klarheit fehlt.
Um zu verstehen, warum diese Signalklarheit so wichtig ist, betrachten wir drei reale Angriffe in Umgebungen, in denen die Vectra AI zusammen mit der nativen Sicherheitssuite von Microsoft eingesetzt wird.
Cloud ransomware (Fortune-500-Finanzdienstleister)
Während eines Scattered Spider , bei dem seitliche Bewegungen über Entra ID und M365 hinweg stattfanden, meldete Microsoft Defender einen Fund mit niedriger Priorität. Vectra AI 11 Angreifer-Verhaltensweisen, korrelierte und priorisierte Signale über Domänen hinweg zu einer einzigen dringenden Entität und stoppte den Angreifer, bevor Schaden entstand.
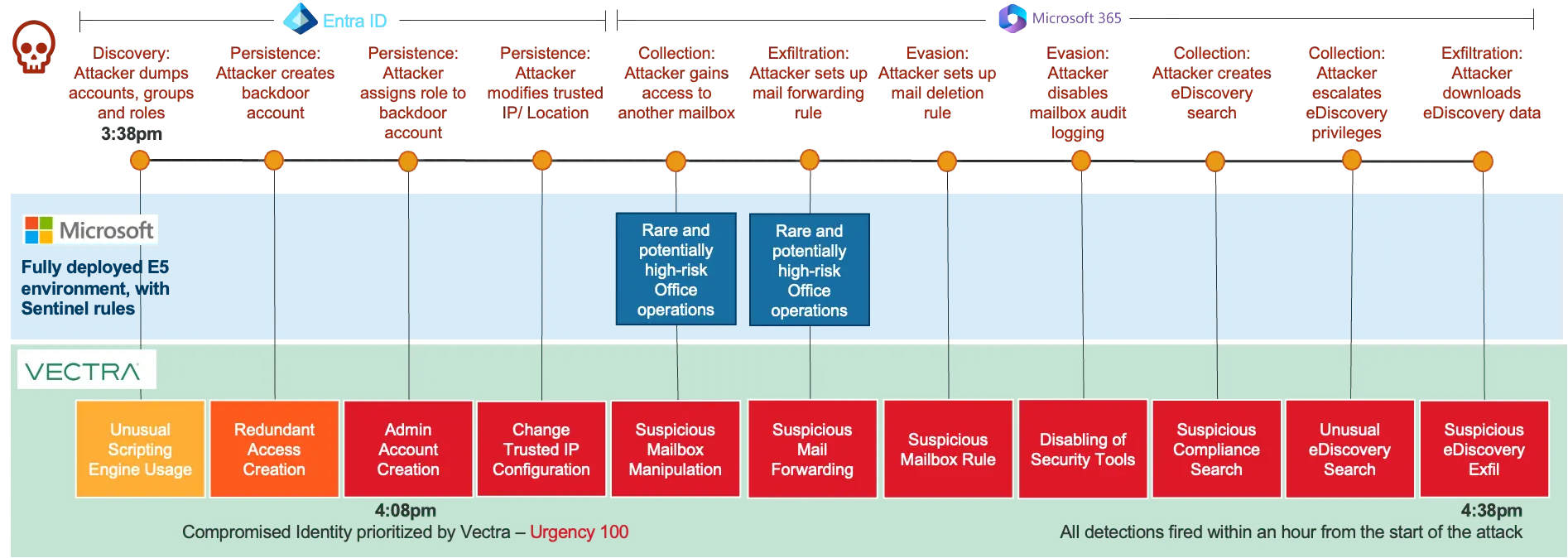
cloud (großer Versicherungskonzern)
Der Angreifer begann vor Ort, stahl Anmeldedaten und bewegte sich heimlich zu Entra ID, wobei er seine Aktivitäten auf die M365-Suite und cloud ausweitete. Microsoft gab einen Tag nach dem ersten Angriff zwei Warnmeldungen mit niedriger Priorität aus. Am ersten Tag Vectra AI innerhalb von 30 Minuten neun Techniken in fünf Domänen und stellte eine Verbindung zwischen verdächtigen Aktivitäten im lokalen Rechenzentrum, Active Directory, Entra ID, Microsoft 365 und cloud her cloud eine vollständige hybride Kill Chain wurde 24 Stunden vor der ersten Erkennung durch Microsoft aufgedeckt.

cloud (globale Fintech-Branche)
Ein Angreifer nutzte gestohlene Anmeldedaten, um auf Azure zuzugreifen, wechselte zu Entra ID und setzte eine bösartige Azure-Richtlinie ein, um die Protokollierung zu deaktivieren und die Datenexfiltration vorzubereiten. Native Microsoft-Tools meldeten eine einzige „verdächtige Anmeldung”. Vectra AI innerhalb von weniger als 90 Minuten sechs miteinander verbundene Techniken in cloud Entra ID und deckte so den gesamten Hintergrund des Angriffs auf.

Diese Beispiele zeigen, dass native Tools zwar Symptome erkennen, aber oft nicht das Gesamtbild erfassen. Die Lehre daraus ist klar: Wenn Prävention versagt, ist eine mehrschichtige, tiefgreifende Verteidigungsstrategie entscheidend, um zu verhindern, dass ein Vorfall zu einer Sicherheitsverletzung wird.
Wie Vectra AI diese Lücken Vectra AI
Die Hybrid-NDR-PlattformVectra AI verstärkt und erweitert den Wert der nativen Abwehrmaßnahmen von Microsoft, indem sie die Erkennung in lokalen Rechenzentren, IoT & OT, Remote-Standorten, Identitäten,cloud und M365 vereinheitlicht. Ihr patentiertes Attack Signal Intelligence sucht nach Angreiferverhalten, um Folgendes zu liefern:
- Abdeckung – Über 100 verhaltensbasierte KI-Erkennungen für Microsoft in Active Directory, Entra ID, M365, Copilot für M365 und Azure Cloud. Es erkennt Verhaltensweisen wie Policy Hijacking, Missbrauch verwalteter Identitäten und verdächtige Nutzung von Automatisierungskonten, die mit Posture-Tools nicht erkannt werden können.
- Klarheit – KI-basierte Triage und Priorisierung reduzieren Alarmmeldungen um bis zu 99 % und steigern die Effizienz des SOC um 40 %. Korrelierte, identitätsbezogene Signale verknüpfen automatisch menschliche und nicht-menschliche Entitäten und setzen sie in einen Kontext, um sie zu untersuchen. Analysten können innerhalb weniger Minuten von der Alarmmeldung zur Ursache gelangen, und mit Hilfe von geführten Angriffsdiagrammen und KI-gestützter Suche können Verteidiger proaktiv Muster und aufkommende Bedrohungen schneller aufdecken.
- Kontrolle – Native Integrationen mit Microsoft Sentinel und Defender for Endpoint die Automatisierung von Playbooks, die Sperrung von Konten und die Isolierung von Geräten für eine schnelle Eindämmung und Schadensbegrenzung in Microsoft-Umgebungen.
Vectra AI Investitionen in die nativen Tools von Microsoft und ermöglicht so einen echten Ansatz zur tiefgreifenden Verteidigung.
Zahlen als Beweis
Eine unabhängige Studie von IDC quantifiziert diesen mehrschichtigen Ansatz. Unternehmen, die Vectra AI einsetzen, erzielen folgende Ergebnisse:
- 52 % mehr Bedrohungen in 37 % weniger Zeit identifiziert
- 40% effizientere SOC-Teams
- 50 % weniger Zeitaufwand für Untersuchungen
Durch die Integration mit Microsoft Sentinel und Defender Vectra AI den Weg von der Erkennung zur Entscheidung und verwandelt hybride Komplexität in umsetzbare Gewissheit.
Kundenvalidierung: Klarheit, die Ergebnisse verändert
Der Unterschied zwischen Wissen und Sehen ist Klarheit. Drei Kunden zeigen, wie das in der Praxis aussieht:
Van-Gogh-Museum
„Bei Microsoft ist alles nur eine ID – Korrelations-IDs, Benutzer-IDs, endlose Zeichenfolgen von
Zeichen. Ich habe 25 Minuten damit verbracht, zwischen Portalen hin und her zu springen, um mir einen Reim darauf zu machen, nur um dann festzustellen, dass es nichts war. Ich bin ein Mensch. Ich brauche Namen und Kontext. Vectra AI meine Sprache. Es sagt mir genau, was passiert, ob es sich um einen Benutzer handelt, der versucht, auf sensible Dateien zuzugreifen, oder um einen Server, der sich verdächtig verhält. Diese Klarheit, alles an einem Ort, ist von unschätzbarem Wert, wenn jede Minute zählt.
- Rob de Zwaan, CISO, Van Gogh Museum
Durch den Schutz unschätzbarer digitaler und kultureller Vermögenswerte erzielte das Museum eine True-Positive-Rate von 84 % und eine frühzeitige Erkennung in Netzwerk-, Identitäts- und Azure-Umgebungen. Dank einheitlicher Transparenz und nachvollziehbarer Erkennungen kann das Team nun innerhalb von Minuten statt Stunden reagieren.
Fortune-500-Finanzdienstleistungsunternehmen
„Microsoft ist ein wichtiger Bestandteil unseres IT-Ökosystems, aber wenn es um Sicherheit geht, müssen wir mehr als nur das Nötigste tun. Mit Vectra AI erhalten wir die integrierten, aggregierten Bedrohungssignale, die wir zur wirksamen Verteidigung unserer Microsoft-Umgebung benötigen. Außerdem werden die Analyse und Korrelation dieser Signale zentralisiert, was uns Zeit und Aufwand spart.“
- CISO, Fortune 500 Finanzdienstleistungen
Dieses weltweit tätige Investmentunternehmen, das sowohl in Azure- als auch in lokalen Umgebungen operiert, konnte zwei identitätsbasierte Angriffe abwehren, die Microsoft E5 übersehen hatte, darunter eine phishing von AiTM. In einem separaten Angriffssimulationstest Vectra AI dank einheitlicher Transparenz und rauscharmer Erkennung in M365, Entra ID und Azure alle neun simulierten Angriffstechniken, die E5 nicht identifizieren konnte.
Advens
„Eine gemeinsame Ansicht von M365- und lokalen Umgebungen ist wirklich hilfreich. Diese Flexibilität ist unerlässlich. Sie ermöglicht uns eine schnellere und genauere Untersuchung. Viele Kunden glauben immer noch nicht, dass Multi-Domain-Angriffe real sind, bis wir ihnen diese zeigen. Wir führen Purple-Team-Übungen durch, wie beispielsweise Golden-HTML-Angriffe, und Vectra AI erkennt diese Vectra AI – während Microsoft-Tools die domänenübergreifenden Bewegungen übersehen.“
- Sébastien Wojcicki, Head of & Security Excellence bei Advens.
Als führender MSSP, der fast 200 Hybrid-Kunden unterstützt, Vectra AI Advens Vectra AI fragmentierte, unübersichtliche Warnmeldungen durch eine einheitliche Übersicht über Netzwerk, Identität und cloud Vectra AI cloud die Untersuchungen um das bis zu 100-fache cloud .
Mit dieser Klarheit deckt Advens die zwischen Microsoft-Umgebungen versteckten Angreiferaktivitäten auf und verkürzt damit Untersuchungen, die früher Stunden dauerten, auf wenige Minuten.
In diesen Geschichten war der Durchbruch nicht mehr Alarme, sondern Klarheit. Alles zu sehen bedeutete nichts, bis es sofort verstanden werden konnte.
Die Zwischenräume sichern
Moderne Angriffe beschränken sich nicht auf einen Bereich – das sollte auch für Ihre Abwehrmaßnahmen gelten. Da Unternehmen zunehmend KI-gesteuerte Tools, hybride Workloads und verteilte Identitäten einsetzen, nutzen Angreifer immer häufiger die unsichtbaren Verbindungen zwischen diesen.
Vectra AI bietet Verteidigern denselben Sichtbarkeitsvorteil, den auch Angreifer nutzen – indem sie Netzwerk-, Identitäts-, SaaS- und cloud in einer intelligenten Plattform vereint. Denn bei der Sicherung Ihrer Microsoft-Umgebung geht es nicht nur darum, jede Oberfläche zu schützen. Es geht darum, die Räume dazwischen zu schützen.
Sind Sie bereit, die Lücken in Ihrer Microsoft-Sicherheit zu schließen? Sehen Sie sich Vectra AI in Aktion an: https://youtu.be/ytWOynLTAco
Oder

